
Cynerio, a company that provides healthcare facilities with its Healthcare IoT platform, recently published a report on the current state of connected medical device security in hospitals of all sizes. The company’s research report on the industry covers the various crucial questions.The report also contains the executive summary and the background of the research.
“For decades, patient care has seen improvements resulting from the data, insight and
timeliness provided by connected devices. However, as the number of these devices
has grown, so too have the number of threats, vulnerabilities, and entry points for bad
actors within healthcare networks,” a Cynerio Research Report.
The statistics on healthcare IoT device security
The information in this report is based on the company’s analysis of over 10 million IoT and IoMT devices collected from current Cynerio implementations at over 300 hospitals and other healthcare facilities in the US and around the world, fully anonymized and analyzed by
company’s Data Team.
In the report introduction specialists provided statistics from various resources on the current cyber security state in the healthcare industry. And according to them:
- It was over 500 healthcare breaches in 2021( US Department of Health and Human Services (HHS);
- The instances of Ransomware attacks on hospitals increased by 123% in the past year (2021 SonicWall Cyber Threat Report);
- Ransomware attacks cost hospitals nearly 21 billion USD last year ( Comparitech);
- The average hospital losses make up 8 million USD per ransomware attack and it takes 278 days for hospitals to fully recover from it ( Emsisoft Report: The State of Ransomware in the US);
- The percentage of healthcare breaches caused by connected devices is directly proportional to the percentage of healthcare breaches caused by phishing (Ponemon Research Report: The Impact of Ransomware on Healthcare During COVID-19 and Beyond).
Healthcare has become the leader among the most targeted victims of ransomware outrunning the runner-ups by 100 to 200%. Cyber security specialists say that Personal Health Information (PHI) may be 50 times more valuable in terms of profit for the cyber criminals than stolen cards can bring on the black market.
What cybercriminals target in healthcare?
IoT (Internet of Things). Specialists use this term for any network connected device or other asset that could not be considered traditional information technology (IT). Here they include smart door locks, VOIP phones and security cameras. But computers or servers don’t belong to this category.
IoMT (Internet of Medical Things). Such devices are used in hospitals for medical purposes. The most common kinds include: glucometers, heart monitors, IV pumps and MRI machines. Perhaps a decade ago they didn’t have many internet connections but today they have.
OT (Operational Technology). OT means hardware, software and communications systems that help to run large scale industrial equipment and assets. In hospitals it usually includes devices like electrical grids, elevators, HVAC (Heating, Ventilation and Air Conditioning) systems.
Connected Devices. The devices in this category are much more simple than those mentioned above. The examples will include a coffee machine or a light switch.
What Are the Most Common Healthcare IoT Device Vulnerabilities?
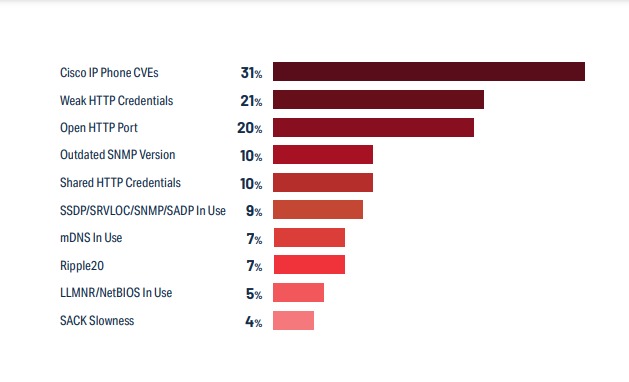
If you read last year’s news headlines on cybersecurity you might get the idea that the most common vulnerabilities would be Ripple20 or URGENT/11. But on the contrary the most common ones are much more obvious and connected to the bad elementary cyber hygiene like usage of the default passwords and settings. And potential attackers can easily find the device manuals online and, of course, try the most obvious thing left unchecked: default passwords and settings. In more than half of healthcare IoT devices there`s one critical vulnerability.
The executive summary of the report
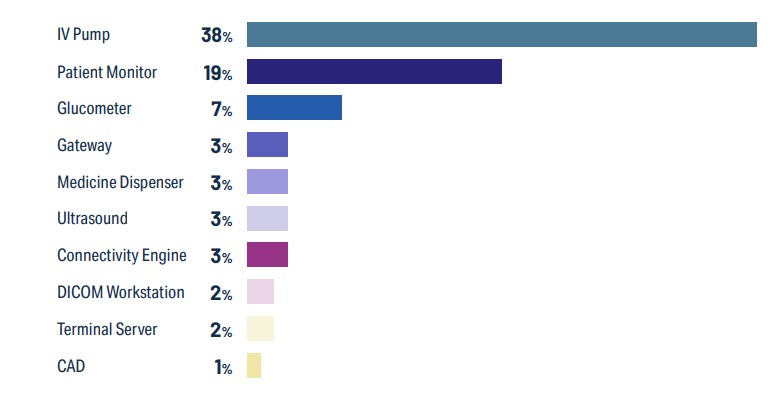
IV Pumps are the most common healthcare IoT device and possess the highest degree of risk. IV pumps have 38% of a hospital’s typical healthcare IoT footprint. And astonishingly 73% of those IV pumps have a vulnerability that could endanger service availability, data confidentiality or patient safety.
53% of IoMT and IoT devices contain critical risks. More than half of connected medical and other IoT devices in hospitals have a well-known critical vulnerability. The fact that puts in danger data confidentiality, service availability and patient safety. A third of bedside healthcare IoT devices, the devices that are closest to patient care and those that patients most depend on, have an identified critical risk.
Urgent11 and Ripple20 had the most headlines, but the most common device risks are simple negligence of cyber hygiene. The most common IoMT and IoT devices often have default passwords and settings that attackers can exploit without much effort. They simply just have to check the manuals for specific devices online. Also the said Urgent11 and Ripple20 vulnerabilities affected only 10 percent of devices with attack vectors that usually are difficult for attackers to exploit successfully.
Critical Healthcare IoT runs outdated Windows versions. Although devices that run an older version of Windows than Windows 10 make up a small portion of a typical hospital’s healthcare IoT infrastructure, they are used in one of the most critical departments. Since those versions are already past the end of life this puts a significant risk on patients who use them. But the problem is that the replacing of the machines those versions run on in most cases will take several years to do.
Most Healthcare IoT devices are used so regularly that it makes them difficult to securely update. Nearly 80% of healthcare IoT devices are monthly and more frequently engaged in patient care meaning they almost don’t have the downtime time for hospital security teams to analyze them for risks and possibilities of attacks, apply the latest available patches, and carry out segmentation for protection of the devices on the network.
At the end specialists outlined the future possible solutions for healthcare IoT security. And they say identifying and addressing risk vectors that are already being exploited in the wild
is a good first step towards implementing much needed security measures.
