Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Sarcoma Group Ransomware is a recently discovered ransomware that poses a serious threat to personal computers and corporate networks. This comprehensive guide will help you understand what Sarcoma Ransomware is, how it infects computers, and most importantly, how to completely remove it from your system using the specialized Trojan Killer tool.
| Common Names |
|
| Type | Ransomware, File Encryptor |
| First Detected | 2024 |
| Platforms Affected | Windows 7, 8, 8.1, 10, 11, Windows Server |
| Infection Level | Critical |
| Data Risk | Extremely High – encrypts files, steals sensitive data, and demands ransom |
Sarcoma Group Ransomware is a sophisticated ransomware that encrypts files on an infected computer or network and demands payment for their recovery. Unlike simpler malware, Sarcoma uses advanced infiltration methods, including zero-day vulnerability exploitation, as demonstrated during the attack on Smart Media Group Bulgaria in October 2024.
Sarcoma Group employs double extortion tactics: in addition to encrypting files, the group also exfiltrates confidential data and threatens to publish it if the ransom isn’t paid. According to Microsoft Security Intelligence research, this approach significantly increases the likelihood of victims paying the ransom.
Unlike less sophisticated ransomware, Sarcoma Ransomware exploits system vulnerabilities for initial access and has more sophisticated methods of removing shadow copies and other backup mechanisms, making recovery without a decryption key more difficult.
Based on data collected from various cybersecurity reports and our own threat intelligence:
Source: Microsoft Security Intelligence Report, Analysis of Sarcoma Group activity, 2024
Sarcoma Group uses several advanced distribution methods:
Source: CISA Cybersecurity Advisory, Ransomware trends analysis, 2024
Learn more about how ransomware work and spread to better protect your system.
Pay attention to the following symptoms indicating a Sarcoma infection:
Source: NVD – National Vulnerability Database, Ransomware financial impact analysis, 2024
Sarcoma poses many serious threats to infected systems and organizations:
Understanding how Sarcoma compares to other known ransomware helps better recognize its unique features and evolution in the malware ecosystem.
Sarcoma Ransomware represents a new generation of industry-targeted ransomware. Unlike mass campaigns, Sarcoma conducts targeted attacks with thorough target reconnaissance. Sarcoma’s main feature is its use of zero-day vulnerabilities for initial access, making traditional perimeter defense measures less effective. The group specializes in attacks against companies in the media and advertising industry, where data value and potential reputational damage are particularly high. Sarcoma applies advanced encryption methods that are practically impossible to break without a key and uses double extortion tactics to maximize pressure on victims. Technically, the program demonstrates a high degree of complexity, including multi-stage infection processes and detection evasion.
While not as technically advanced as some threats like LockBit 4.0 Ransomware which utilizes multi-threaded encryption and triple extortion tactics, Sarcoma Group compensates with its highly targeted approach and industry-specific knowledge when selecting victims.
TrickBot, while originally developed as a banking trojan, evolved into a platform often used to deliver ransomware. Unlike Sarcoma, TrickBot is usually the first stage of an attack rather than the final payload. It specializes in credential collection and establishing persistent access that can then be used to deploy ransomware. TrickBot has a modular architecture allowing operators to add various functionalities depending on the target. While both TrickBot and Sarcoma can be part of ransomware attacks, their roles and technical approaches differ significantly.
Emotet, similar to TrickBot, started as a banking trojan but developed into a multi-purpose malware delivery platform. Emotet typically spreads through phishing campaigns, using stolen email content to create convincing attacks. Unlike Sarcoma, which focuses on vulnerabilities for initial access, Emotet relies on social engineering and document macros. Emotet is often used as an initial entry point, followed by other malware, including ransomware. Compared to Sarcoma’s targeted approach, Emotet is typically used in broader, less targeted campaigns.
The distinguishing feature of Sarcoma in this landscape is its specialization in specific industries and high-tech approach to initial access. While many ransomware rely on phishing or brute-forcing credentials, Sarcoma’s use of zero-day vulnerabilities demonstrates the group’s high level of technical capabilities and resources. This makes Sarcoma an especially dangerous threat that requires advanced defense strategies.
Trojan Killer is specifically designed to remove complex trojans and ransomware, including Sarcoma:

Warning: Manual removal of Sarcoma is extremely difficult due to its advanced persistence mechanisms and analysis protection features. This approach should only be attempted by users with significant technical experience.
schtasks /query /fo LIST /v to list all scheduled tasksschtasks /delete /tn "TaskName" /fAfter removing Sarcoma Ransomware, your files will unfortunately remain encrypted. You have several options:
Protection against Sarcoma requires a comprehensive security approach:
These protective measures will help guard not only against Sarcoma but also against other threats such as trojan downloaders and potentially unwanted applications that might create vulnerabilities in your system.
This section provides detailed technical information about Sarcoma’s architecture, internals, and detection methods for security researchers, threat hunters, and incident response professionals.
Sarcoma uses a sophisticated infrastructure for its operations:
Sarcoma Core Components:- Loader → Initial infection component (~150-300 KB)- Core Module → Main functionality controller (~300-500 KB)- Configuration → Encrypted command and control settings- Encryption Module → Responsible for file encryption- Exfiltration Module → Manages data theftExecution Sequence:1. Loader executes and establishes persistence2. Core module loads and decrypts embedded configuration3. Core module contacts C2 servers for instructions4. Exfiltration module collects and transmits valuable data5. Encryption module encrypts files and creates a ransom note |
Sarcoma’s command and control infrastructure uses a multi-layered architecture:
| Component | Technical Details | Features |
|---|---|---|
| Communication Protocol | HTTPS with certificate pinning and multi-layer proxy chain | Use of one-time domains for communication |
| Server Structure | Multi-tiered architecture with front-end proxy servers | Use of secure hosting and .onion domain |
| Fallback Mechanism | Several hardcoded IP addresses | Use of cryptocurrency networks for alternative communication |
| Data Encryption | AES-256 for file encryption, RSA-4096 for keys | Unique keys for each victim |
Security researchers should monitor the following indicators associated with Sarcoma:
Security professionals can implement the following approaches to protect their organization:
For system administrators working with affected systems:
# Enabling shadow copies (after malware removal)vssadmin resize shadowstorage /for=C: /on=C: /maxsize=10GBvssadmin create shadow /for=C:# Checking and removing suspicious tasksschtasks /query /fo LIST /v | findstr /i "powershell cmd.exe regsvr32"# Checking and restoring important Windows servicessc query wuauservsc config wuauserv start= autosc start wuauserv# Blocking known Tor exit nodes on the firewallnetsh advfirewall firewall add rule name="Block Tor Exit Nodes" dir=in action=block remoteip=torlist.txt |
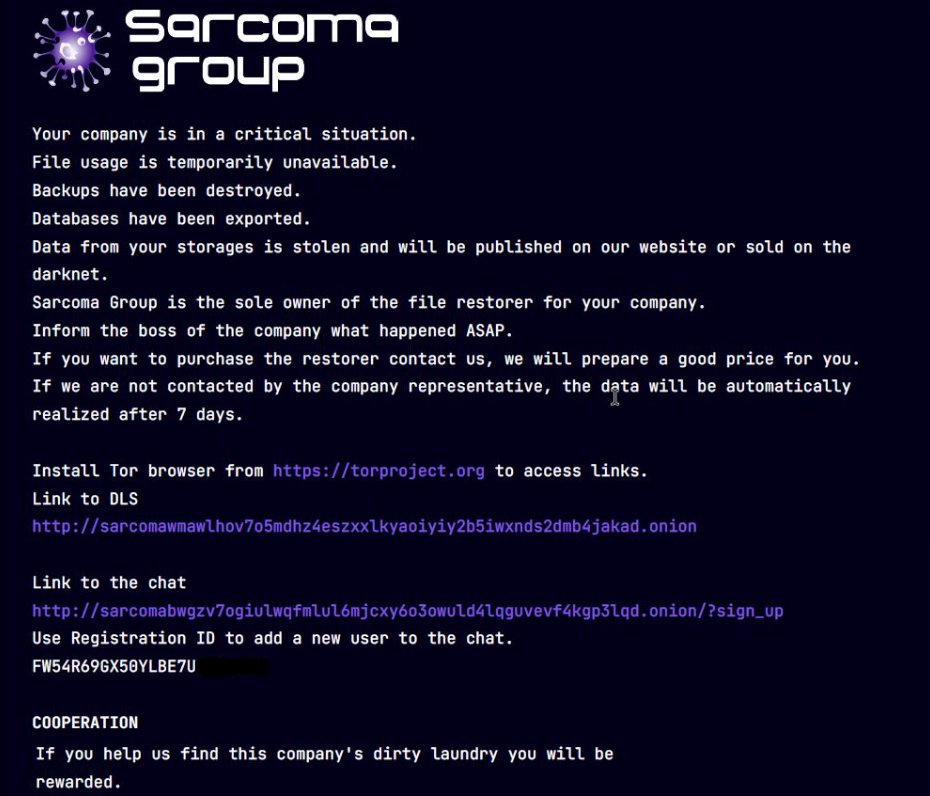
Below is an example of the contents of the FAIL_STATE_NOTIFICATION.pdf file created by Sarcoma Ransomware:
# SARCOMA NOTICE## YOUR SYSTEMS HAVE FAILEDYour data has been encrypted and exfiltrated. The encryption uses a military grade algorithm that cannot be broken.## WHAT HAPPENED?1. We've penetrated your network and stayed undetected for weeks2. We've downloaded more than 40GB of your sensitive data3. We've encrypted your files with a unique key## YOUR OPTIONSYou have exactly 7 days to pay 50 BTC to the address below. After payment, you will receive:- Decryption tool and key- Deletion of all stolen data- Security report showing how we accessed your network## COMMUNICATIONContact us using one of these Tor sites:- sarcomabwgzv7ogiulwqfmlul6mjcxy6o3owuld4lqguvevf4kgp3lqd.onion- sarcomawmawlhov7o5mdhz4eszxxlkyaoiyiy2b5iwxnds2dmb4jakad.onion## WARNINGDO NOT:- Contact law enforcement- Attempt to restore systems without our key- Ignore this messageCONSEQUENCES:- After 7 days, the price doubles- After 14 days, your data will be published- After 30 days, decryption becomes impossible## PROOF OF COMPROMISEWe've attached sample files to prove we have your data. |
These technical details provide security professionals with the information needed to better understand, detect, and protect against Sarcoma Ransomware in their environment.
While Sarcoma Group predominantly targets corporate networks and organizations, home users are also at risk. Attackers can use phishing emails or compromised websites to spread malware to personal computers. Home users often have fewer resources for detecting and responding to such attacks, making them vulnerable. For protection, it’s recommended to use reliable antivirus software, regularly update your operating system and programs, create backups of important data, and be cautious when opening email attachments or clicking on suspicious links.
If your system is already infected, you need to act quickly. First, disconnect your computer from the internet to prevent further spread of the malware or data leakage. Then use specialized tools, such as Trojan Killer, to scan for and remove malicious components. Unfortunately, already encrypted files will likely remain inaccessible without a decryption key. Check the availability of Windows shadow copies or restore data from backups if you have them. If it’s a corporate environment, immediately contact your IT security team and consider involving incident response specialists. Paying the ransom is not recommended, as it doesn’t guarantee recovery of your data.
There are several characteristic signs indicating infection specifically by Sarcoma. First, look at the extension of encrypted files – Sarcoma adds the .xp9Mq1ZD05 extension to files. Second, check for the presence of a notification file named FAIL_STATE_NOTIFICATION.pdf in folders with encrypted files. The content of this file is also characteristic – it usually mentions specific Tor addresses for communication: sarcomabwgzv7ogiulwqfmlul6mjcxy6o3owuld4lqguvevf4kgp3lqd.onion and sarcomawmawlhov7o5mdhz4eszxxlkyaoiyiy2b5iwxnds2dmb4jakad.onion. Also, Sarcoma typically mentions data theft before encryption (double extortion tactic) and gives a limited time to pay the ransom, after which it threatens to publish the stolen data.
Sarcoma Group chooses media and advertising companies as primary targets for several reasons. First, these organizations often possess valuable data – customer information, marketing plans, intellectual property, and confidential materials that can be used for blackmail. Second, media companies typically depend on continuous access to their systems to meet tight publication deadlines, making them more vulnerable to ransomware time pressure tactics. Third, the public nature of media companies means that data leaks will lead to significant reputational damage, increasing the likelihood of ransom payment. Finally, some media organizations may have less mature cybersecurity systems compared to financial or government institutions, making them easier targets.
At the time of writing this article, there are no reliable free decryptors for Sarcoma Ransomware. Since Sarcoma uses modern encryption methods (a combination of asymmetric RSA-4096 and symmetric AES-256), breaking the encryption without a key is technically extremely difficult. Law enforcement agencies and security researchers continuously work on analyzing new ransomware, and decryptors sometimes become available if vulnerabilities in encryption implementation are discovered or keys fall into the hands of specialists. It’s recommended to periodically check Microsoft Security Intelligence resources and specialized security forums for up-to-date information on possible solutions. However, the most reliable recovery method remains pre-created backups.
Sarcoma Group Ransomware represents a serious threat to organizations and individuals. This advanced ransomware combines sophisticated infiltration techniques, powerful encryption, and double extortion tactics, making it particularly dangerous.
The best protection against Sarcoma and similar threats is a comprehensive approach to cybersecurity, including regular updates, multi-factor authentication, network segmentation, and most importantly, a reliable backup strategy. Remember that prevention is always more effective than treatment, especially when it comes to ransomware.
If you do encounter Sarcoma, decisive actions to isolate the system, remove the malware, and restore from backups are your best steps. Specialized tools such as Trojan Killer can help detect and remove malicious components, although encrypted files will likely require restoration from backups.
Stay vigilant, keep your systems up to date, and monitor for new threats in the constantly changing cyber threat landscape.