
Analysts from Sucuri company found in WP Live Chat Support-plugin dangerous bug.
Vulnerability allows to unauthorized attackers perform XSS-attack and implement malware on all pages of the website that use this extension.“An XSS flaw is pretty serious in itself. It allows hackers to inject malicious code in websites or web apps and compromise visitors’ accounts or expose them to modified page content”, — say Sucuri specialists.
After receiving information about this disadvantage, developers fixed it with the next release of their product.
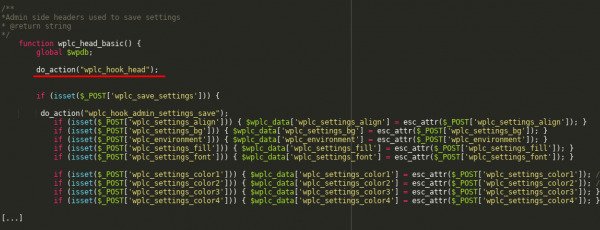
Problem linked with incorrect application of admin_init request. As discovered researchers, WP Live Chat Support creators used this hook for calling wplc_head_basic function that is responsible for update of plugin parameters. With this mechanism of users’ rights check on performing of such actions was absent in program’s code.
Sucuri specialists argue that as admin_init works through system utilities admin-post.php or admin-ajax.php, attacker should update parameter wplc_custom_js and accommodate his code there.
With this, cybercriminal can add malware script on any page of vulnerable website where installed WP Live Chat Support. For attack, hacker will not need any additional privileges and even authorization on web-resource. Attackers may act with the use of simple bots, automatically putting their code in page headings through the wplc_head_basic parameter.
Researchers informed developers about a bug on April 30, 2019, and on May 15 creators of extension released WP Live Chat Support version 8.0.27 where vulnerability was fixed. All plugin users are recommended to install patch ASAP.
According to WordPress repository, problematic extension installed on more than 60 thousand websites. As shows experience, cybercriminals trace information about bugs in extensions and try to find unpatched resources, even if developers have already released a patch.
Source: https://www.bleepingcomputer.com
