About Golden Axe
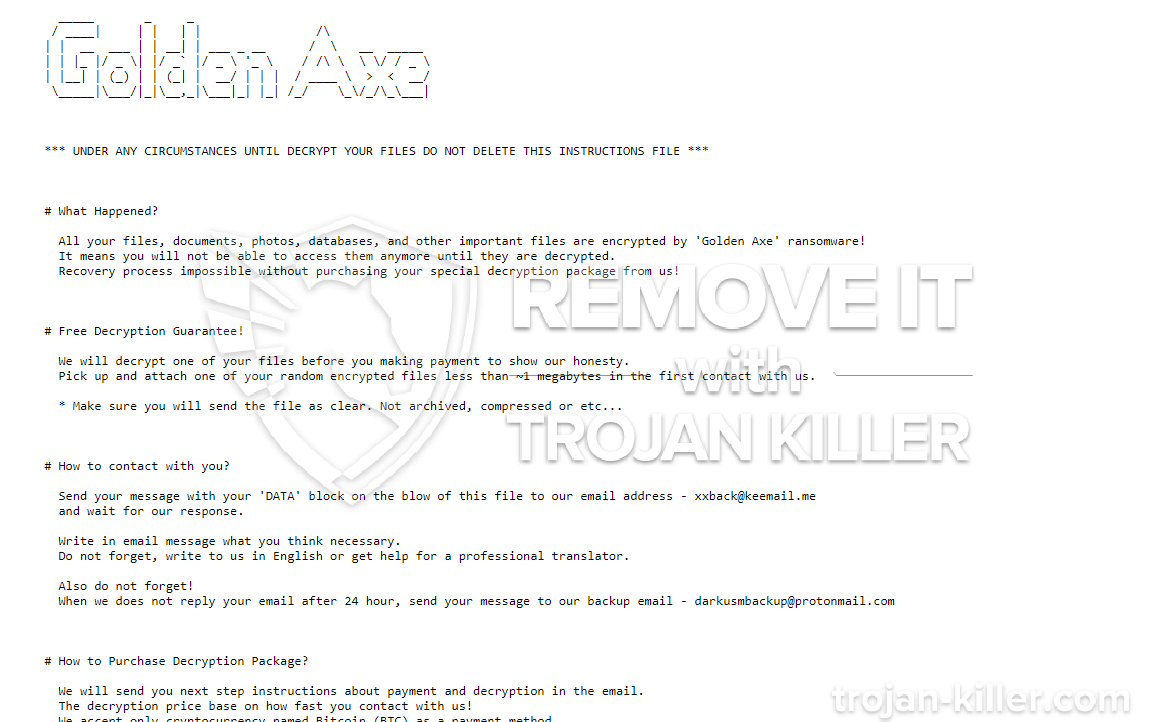
Golden Axe is identified by our malware research study group as the brand-new ransomware infection. Some anti-virus programs already discover it, nonetheless, there are certain applications that bypass it and hence permit its breach. Individuals have actually concerned calling it that, because of the extension, it adds at the end of your data. Allow’s elaborate. Ransomware tool invade your computer via slyness and skill. After that, once they get in, they spread their corruption. They utilize security algorithms to lock your files. After that, extort you for their release. After Golden Axe slips right into your system, it puts every one of your data under lock-down. It affixes its own expansion at the end, thus making it hard to reach. And, no documents can escape its reach. It targets papers, archives, photos, music, video clips, all of it! Afterwards, you can longer open it. Relocating the data, or relabeling it, will not aid. The only method to release your information from the ransomware’s maintain, is conformity. The infection expects you to pay a ransom, if you want to release your documents. It makes that clear, in the ransom note it leaves after file encryption. The note is normally a text data, left on your Desktop. You can additionally find it in every folder which contains secured data. It explains your predicament, as well as offers you an escape. According to Golden Axe, the only means to release your files is with an unique decryption secret. And, to get it, you should pay a ransom money. The amount varies, and also it’s typically asked for in Bitcoin. Yet other cryptocurrencies are additionally an option. The infection assures, to send you the key you require, after you finish the transfer. As well as, that’s it. That’s all you get– a guarantee. You have absolutely no assurances that conformity leads to something positive. Don’t hinge on the word of cyber lawbreakers. These are undependable individuals with harmful programs. People, who will certainly double-cross you. Do NOT pay them a penny. Don’t call them Do NOT adhere to their demands. It may seem a difficult phone call to make, however it’s the appropriate one.
Exactly how did my computer got harmed by Golden Axe?
Your computer systems gets infected with the Golden Axe virus because of your failure to be alert. Some people do not pay attention to crucial details while surfing the web or setting up numerous programs. As well as, perhaps this is the means you ended up with an infection. Below’s the important things. The infection makes use of the old but gold invasive methods to fool you. As well as, slide past you unnoticed. That includes concealing behind corrupted web links, sites, and also torrents. It utilizes freeware as a way to hide itself. As well as, poses as a fake system or program upgrade. Like, Adobe Flash Player or Java. However, usually, it utilizes spam e-mails. You obtain an e-mail that seems ahead from a well-known firm. Like, Amazon or PayPal. And, the email urges you to click a web link, or download and install an add-on. If you do, you end up with a ransomware. Bear in mind that these kinds of risks victimize your recklessness. They need you to hurry, as well as skip doing due diligence. That reduces their hidden seepage. They rely upon you to leave your fate to possibility. Don’t! Do not select carelessness over caution. One keeps infections out. The other invites them in.
Why is Golden Axe unsafe?
Do NOT act the method Golden Axe instructs you. Following its hazardous commands is dangerous and also will undoubtedly make your pocketbook thinner. Thus, do not pay them money. Don’t reach out to the cyber abductors. If you do, you’ll regret it. It’s a futile attempt to restore your information, and it will not finish well for you. Below’s why. There are a few circumstances that can unfold, when you see the ransom note on your screen. State, you decide to conform. You connect to the extortionists, pay their ransom money, as well as wait. You wait on them to send you the decryption secret they assured. Well, what if they don’t? Nevertheless, you have no warranties. All, you hinge on, is a promise. Can you absolutely think words of cyber kidnappers? The response is ‘No.’ These are people, that will dissatisfy you. Do not give them loan! There’s also one more option. They can, actually, send you a decryption key. But, when you try to use it, it falls short to function. Yes, they can send you the wrong one. Then, you have less cash, as well as your data stays locked. Don’t pay! And, even your best-case circumstance, isn’t a reason for delight. What happens after you pay the ransom money, obtain the right secret, and free your documents? Well? Think of it. You paid money to eliminate a symptom, however not the infection creating it. So, you remove the encryption, but the Golden Axe ransomware remains. It’s still hiding in the corners of your system, cost-free to strike once more. After that, you’re back at square one. There aren’t enough means to worry this enough. Do NOT pay!
So, your computer got attacked by Golden Axe and probably you have actually lost time trying to remove it by hand. We are definitely confident that the service below will absolutely work in removing Golden Axe in an automatic means. Yet allow us first talk about prevention of such ransomware attacks in future. Is there something that you can do to avoid this type of unpleasant hazard from entering your computer beforehand? There are couple of things we would love to discuss below. Initially one is your personal responsibility for being extremely mindful while you use your computer as well as largely while you surf the internet. When examining your e-mail as well as see some suspicious add-ons consisted of, do not hurry up to open them. In the same way, when you get on Facebook as well as somebody in your calls sends you messages containing attachments, be extremely mindful, especially if these are some executable data. The 2nd thing to take into consideration is examining the reliability of your current anti-virus program. Regretfully, there are a lot of safety applications these days that only assert to be reliable, whereas in times of actual malware invasions they just fail to do the task as advertised. In case Golden Axe passed through into your computer system this means that your existing anti-virus did not execute its advertised function and also really fell short to safeguard your system. So, undoubtedly, it is a factor for you to reconsider your selections and also most definitely switch to some other application that can certainly make the desired level of defense. We can also discuss some portion of users that choose not to have any anti-virus software application whatsoever. Surely, this is a major error on their part, because presently the world wide web has lots of cyber risks that might privately infiltrate at risk systems, specifically those that are not furnished with some basic level of safety. So, having anti-malware permanently running as well as shielding your PC is a must-do thing in today’s cyber world.
STEP 1. Recover files from Golden Axe ransomware encryption
There are a lot of different ransomware viruses on the internet. Some of them are more dangerous than the others because they not only leaving malicious processes to protect themselves, but also removing backups of your system to make the recovery process impossible.
Please Note: Not all ransomware infections are able to remove backups of your system, so it is always worth to try a windows recovery method below. In order to protect your backups from this danger, try our Anti-Ransomware product:
We recommend use Safe Mode with command prompt to safely perform a recovery of your files. You will have to reboot your computer, so you better save this instruction some where on your hard drive or read if from second computer.
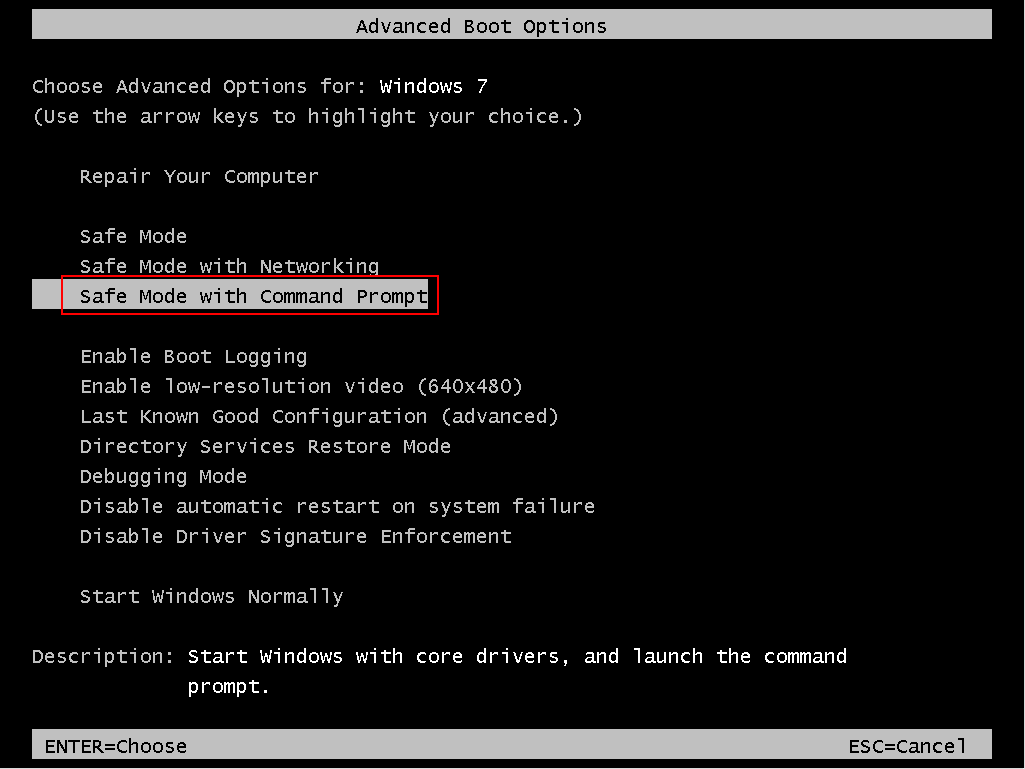
- Windows 7 users: You need to reboot your system and before its loaded constantly press “F8” button until you see boot options.
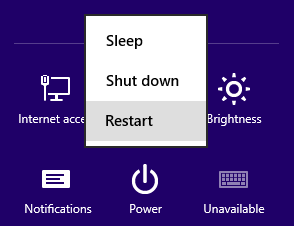
- Windows 8/10 users: Press the “Power” button from Windows login screen or Settings. Hold the Shift key on your keyboard and click on “Restart”
- After your computer reboots – Click on “Troubleshoot” – press “Advanced options” – “Startup Settings”
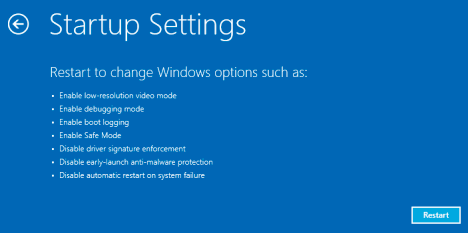
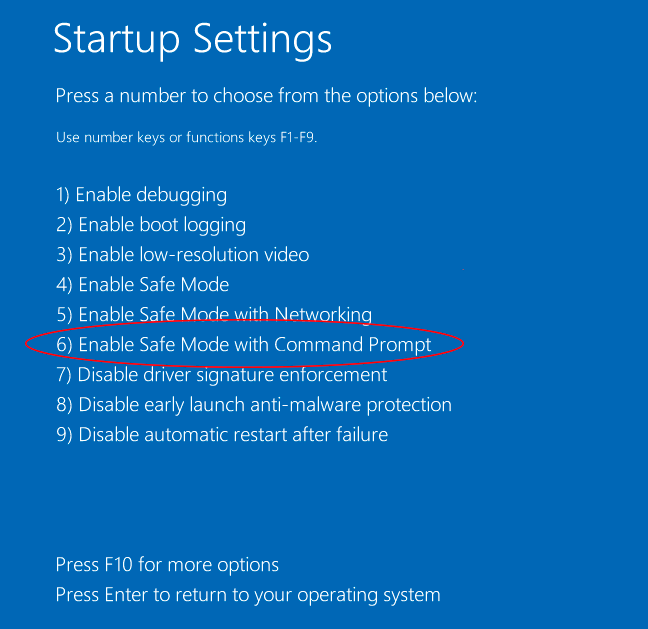
- Click the “Restart” button and your computer will reload again and show you the list with all options. You need to choose the “Safe Mode with Command Prompt”
- When your windows loads, enter the following line: cd restore and press Enter.
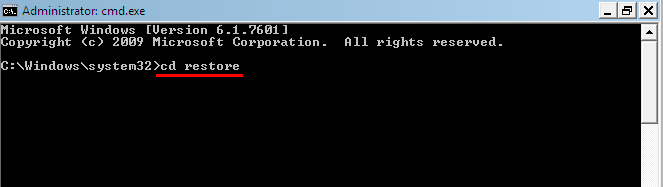
- After that type rstrui.exe line and press Enter.
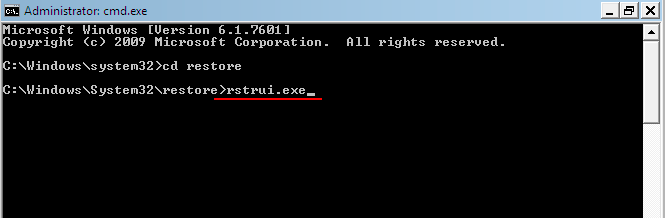
- A recovery window will open before you, Click Next to proceed.
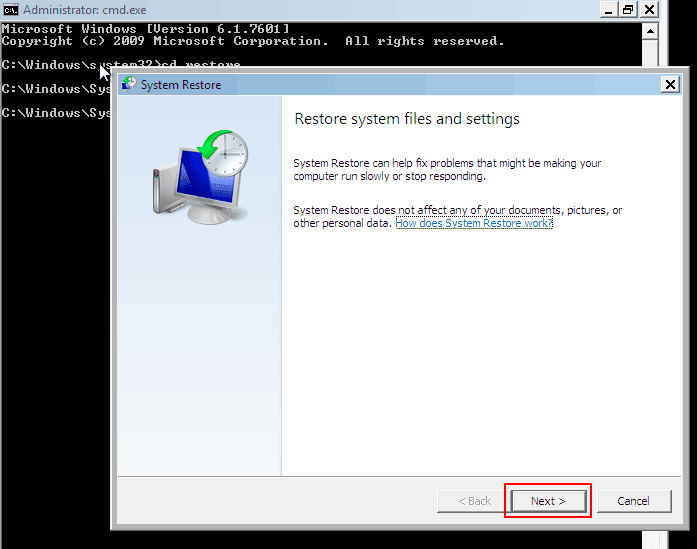
- In the next window, you need to choose a Restore point. All files in protected drives will be recovered at the time when this point was created (prior to the infection with Golden Axe). In the case when ransomware removes these backups, there will be no Restore points listed. Select a Restore point and click “Next”.
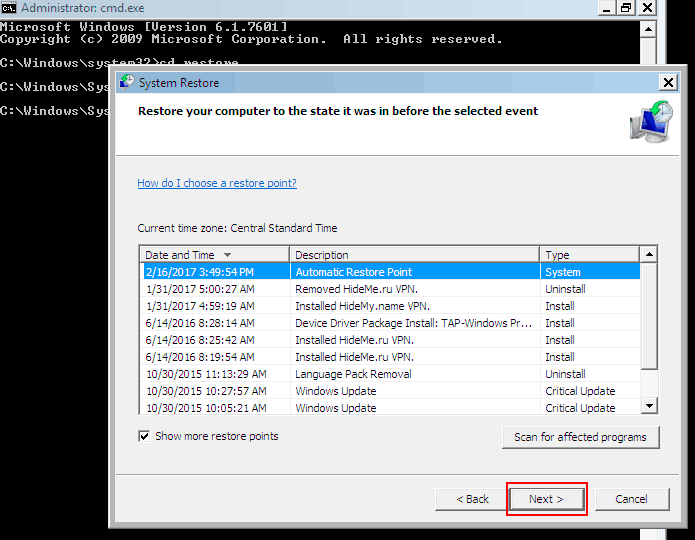
- Click “Finish” in this window and confirm the recovery process by pressing “Yes“.
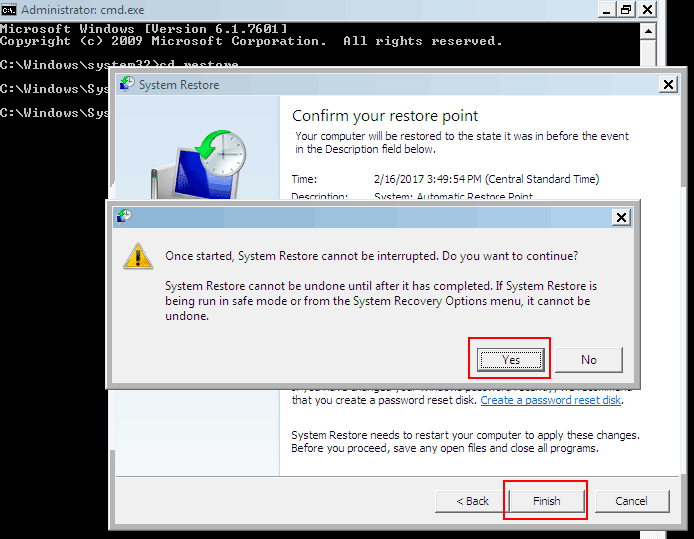
Simple example of how to recover your files from ransomware infection:
STEP 2. Removing Golden Axe ransomware malicious files
Once the recovery process is complete, you should consider scanning your computer with a GridinSoft Anti-Malware in order to find any traces of Golden Axe infection. Though some ransomware viruses are removing themselves right after the encryption of your files, some may leave malicious processes on your computer for special purposes of cyber criminals.
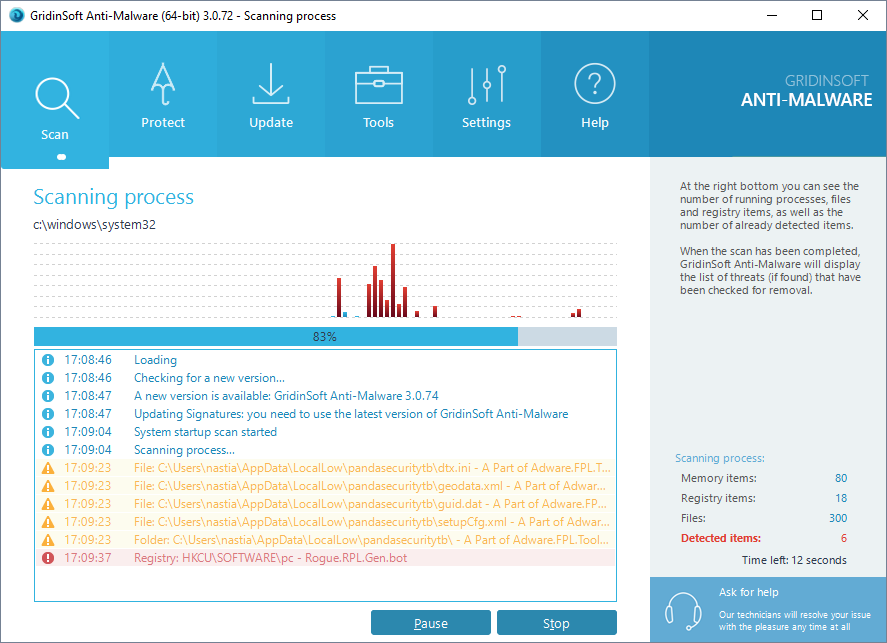
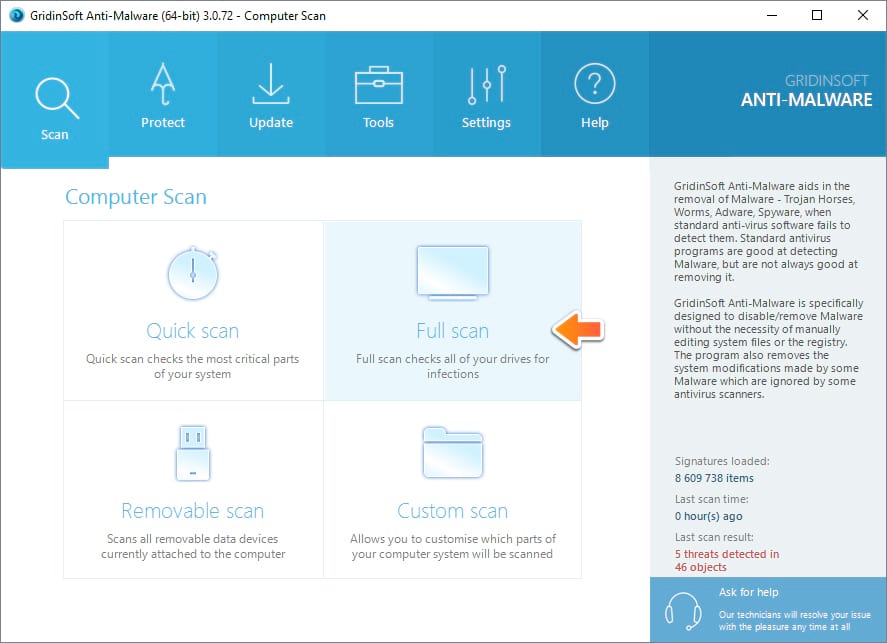
- Run GridinSoft Anti-Malware and choose the scan type, which is suitable for your needs. Of course, for the accuratest scan results we recommend you to choose the “Full Scan”.
- Give Anti-Malware a little time to check your system:
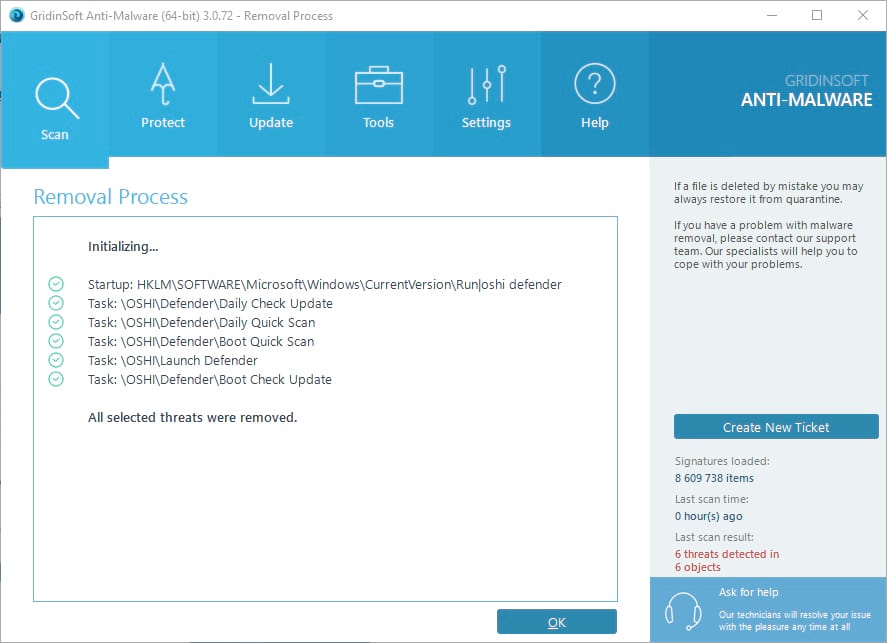
- Move to quarantine all the viruses and unwanted files, that you see in the results list:
- Enjoy the malware removal process:
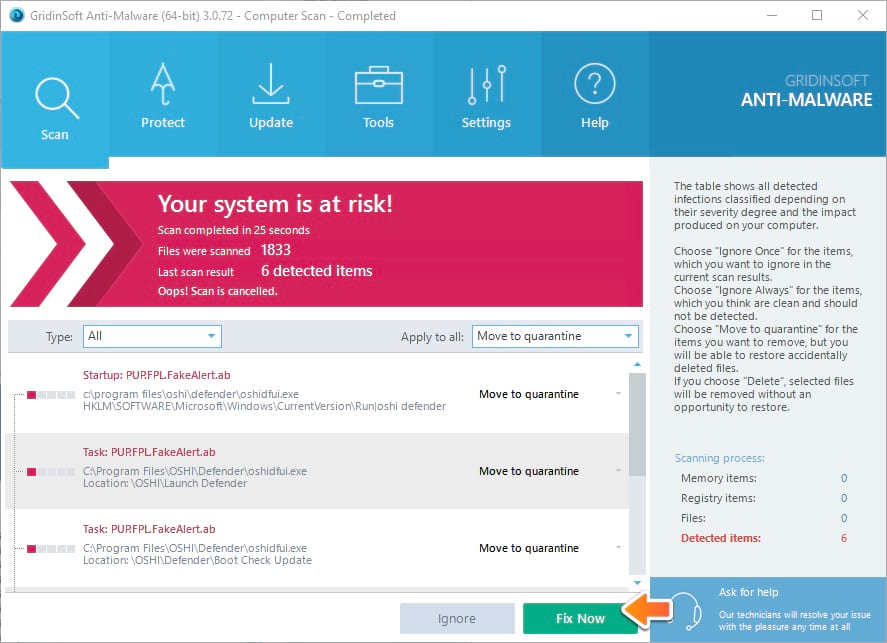
Use of On-run protection may additionaly prevent different types of cyber attacks, our protect may flag the downloader of the ransomware as a malicious application preventing the download of Golden Axe.
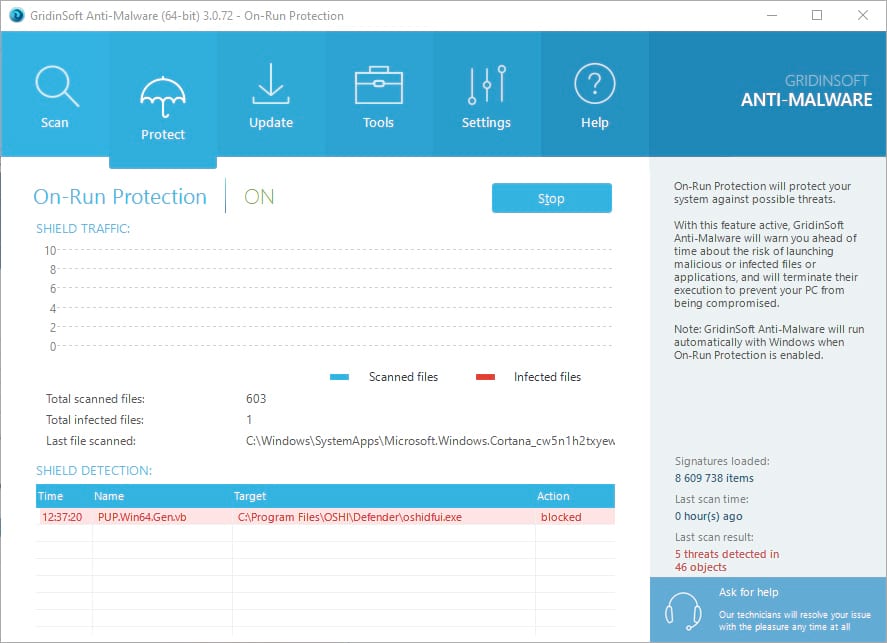
STEP 3. Prevent the Golden Axe ransomware infection with GridinSoft Anti-Ransomware
Despite that some ransomware can remove backups of your OS, our product GridinSoft Anti-Ransomware is able to protect them from the removing in the first place. When some kind of a malicious program or ransomware virus tries to delete your backups, out program intercepts this request and blocks the sending process.
Note: that the product is still in Beta testing phase, some bugs and glitches are possible.
Besides the protection tool, you should read and learn few simple rules. Follow them every time you work on your computer and your will decrease chances of your infection to a minimum:
- Don’t open suspicious spam letters. No way! Be very careful with your downloads. Download and install software preferably from its official website.
- Do backups of your important files regularly. Storing your really important files in few different places is a good decision.
- Keep your system free from adware, hijackers and PUPs The infected computer will be more likely compromised with other malicious software, and ransomware is not an exception in this case.
- Don’t panic and be reasonable. Don’t pay the ransom fee right after you got infected, it is always best to search on the internet for some answers. It is possible that someone have developed a decryption tool that might help you.