Sophos specialists published a report, dedicated to increased activity of MegaCortex cryptographer.
This extortionist is orientated majorly of corporate sector and used in the carefully planned targeted attacks.Such incidents are a real trend in the latest time, and many big companies suffered from targeted attacks: it is worth remembering LockerGoga “heroic actions”. Its victim was one of the world’s main aluminum producers Norsk Hydro, and a series of big chemical enterprises.
Other threats that similar approach are Ryuk, Bitpaymer, Dharma, SamSam and Matrix.
Sophos analysist said that MegaCortex was discovered in January 2019, when someone uploaded malware’s specimen on VirusTotal. Since that time number of attacks constantly grows: in total experts noted 76 incidents, with 47 of them (almost two thirds) occurred in the last week.
MegaCortex attacks affected companies in US, Canada, Netherlands, Ireland, Italy and France.
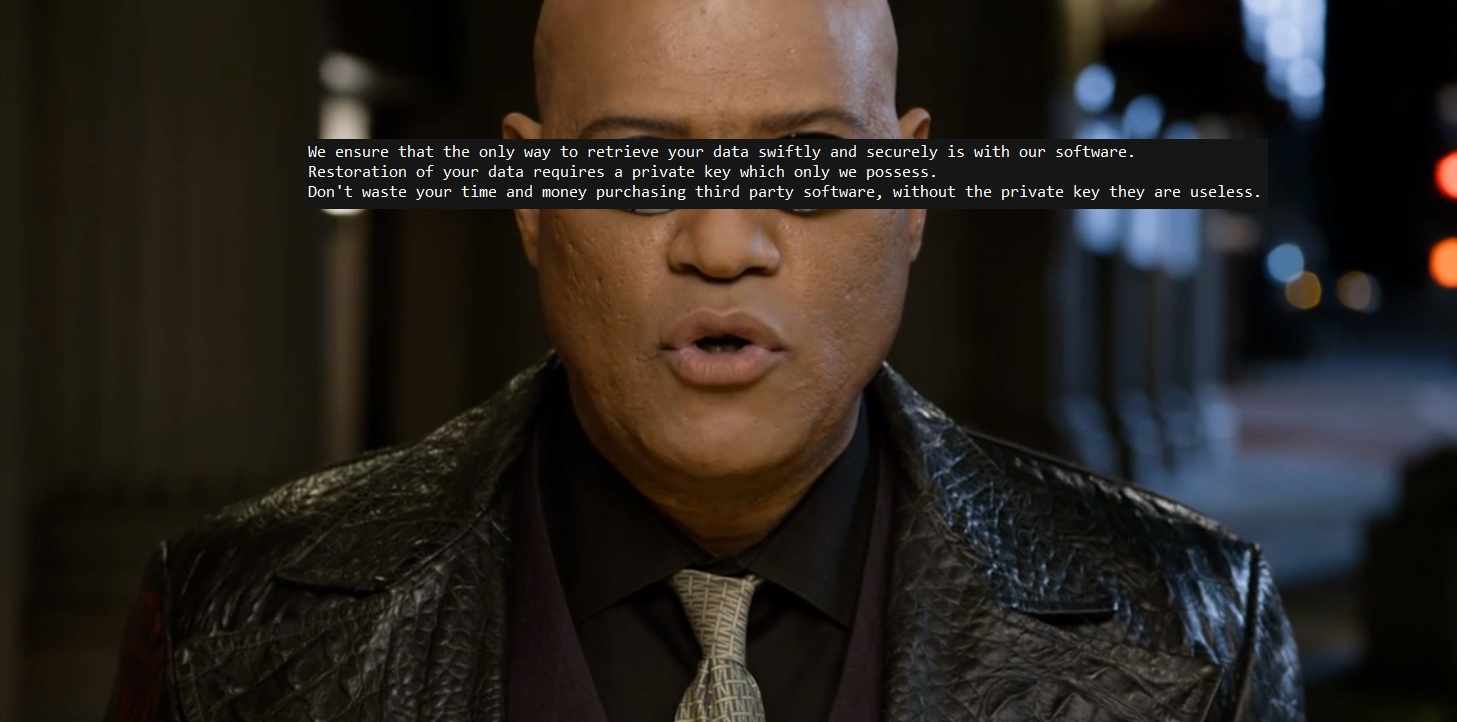
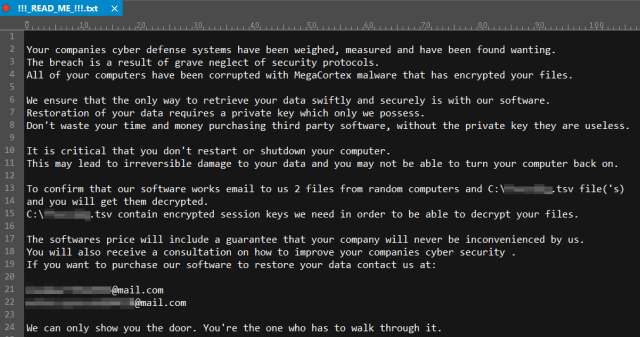
Cryptographers’ operators try as soon as possible to reach domain’s controllers and spread threat on as much systems as possible. “Recognize” MegaCortex is ealy due to extortionists’ message that can be seen below, or by changes files’ extensions as malware changes them on random sequence of eight symbols.
In the report Sophos researchers acknowledge that could not detect how extortionist gets on infected hosts. In its turn, IT-experts write in social networks that MegaCortex allegedly uses for it Rietpoof uploader. This is quite interesting observation as usually cryptographers get in networks through the brutforce of the poorly protected RDP-endpoints or as an payload of the second phase of the attack, just after infection of machines with Emotet or Trickbot malware.
As the attack seems to indicate that an administrative password was abused by the criminals, we also recommend the widespread adoption of two-factor authentication for everything that currently requires just a password, and can use 2FA.
Keeping regular backups of your most important and current data on an offline storage device is the best way to avoid having to pay a ransom altogether.
Source: https://news.sophos.com
