
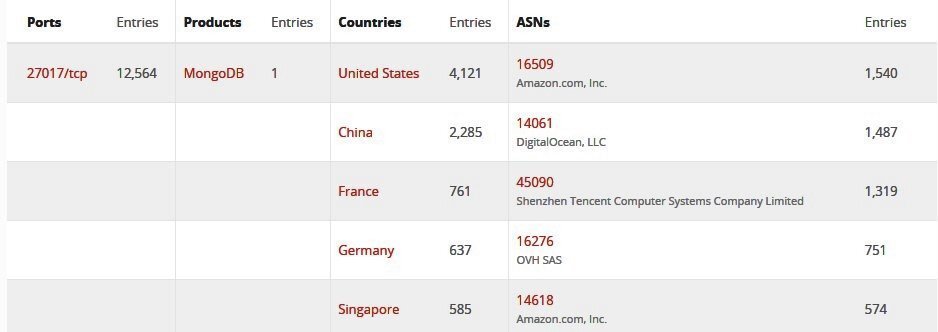
Independente especialista internet de segurança Sanyam Jain descobriu mais de 12 bancos de dados de mil MongoDB que destruíram cibercriminosos.
UMAttackers excluem todas as notas do armazenamento e propõem que a vítima entre em contato para restauração de informações. Especialistas vincular ataques com mais cedo banda Unistellar desconhecido.“Primeiro eu observei os ataques em abril 24, quando inicialmente descoberto um banco de dados que limpou MongoDB, em vez das enormes quantidades de dados vazados que costumava encontrar, continha apenas a seguinte nota: “restaurar ? Contato : unistellar@yandex.com ”, - disse Sanyam Jain.
A campanha da Unistellar começou no final de abril deste ano e afetou banco de dados com informações sobre 257 milhões de cidadãos da Índia encontrados em acesso aberto por especialista em segurança Bob Diachenko. O pesquisador descobriu um armazenamento desprotegido que continha dados de identificação pessoal, em abril 23. As notas incluíam nomes, números de telefone, e-mails e detalhes do endereço físico.
Especialista relatou sobre sua descoberta no centro indiano de reações sobre ameaças cibernéticas (CERT-In), Contudo, banco de dados estava disponível apenas até maio 8, quando os cibercriminosos unistelares o destruíram.
Os especialistas dizem que os cibercriminosos usam um script automatizado que procura bases MongoDB desprotegidas e apaga as informações que elas contêm. Malware adiciona linhas de células livres com a proposta de escrever em um dos e-mails para restauração.
Os analistas observam que os invasores criam pontos para restauração de informações, embora não esteja claro se eles criam uma cópia de reserva das bases destruídas. Rastrear a compra também não é possível, pois os cibercriminosos não publicam números de carteiras digitais, mas apenas fornecem as vítimas em correspondência pessoal.
Diachenko descobriu na Internet sobre 150Gb de dados, coletado por Verificações[.]Eu agência de marketing. Powered by MongoDB base continha mais de 800 milhões de emails, datas, nomes, números de telefone e outros dados sobre pessoas privadas e organizações. Posteriormente, outros pesquisadores descobriram mais dois depósitos que pertenciam à empresa. por este, o volume de dados comprometidos consistia 2 bilhões de registros.
Esses ataques podem acontecer apenas porque os bancos de dados MongoDB são acessíveis remotamente e o acesso a eles não está devidamente protegido. Isso significa que os proprietários do banco de dados podem evitar facilmente tais ataques, seguindo etapas bastante simples, projetadas para proteger adequadamente suas instâncias de banco de dados.
MongoDB fornece detalhes sobre como proteger um banco de dados MongoDB implementando a autenticação adequada, controle de acesso, e criptografia, e também oferece uma lista de verificação de segurança para os administradores seguirem.
