
No primeiro trimestre deste ano, especialistas da Palo Alto Networks, observou 6536 tenta baixar criptógrafo Compartilhar da base do seu cliente. Cerca de um terço dos pedidos perigosas vieram de computadores dos EUA.
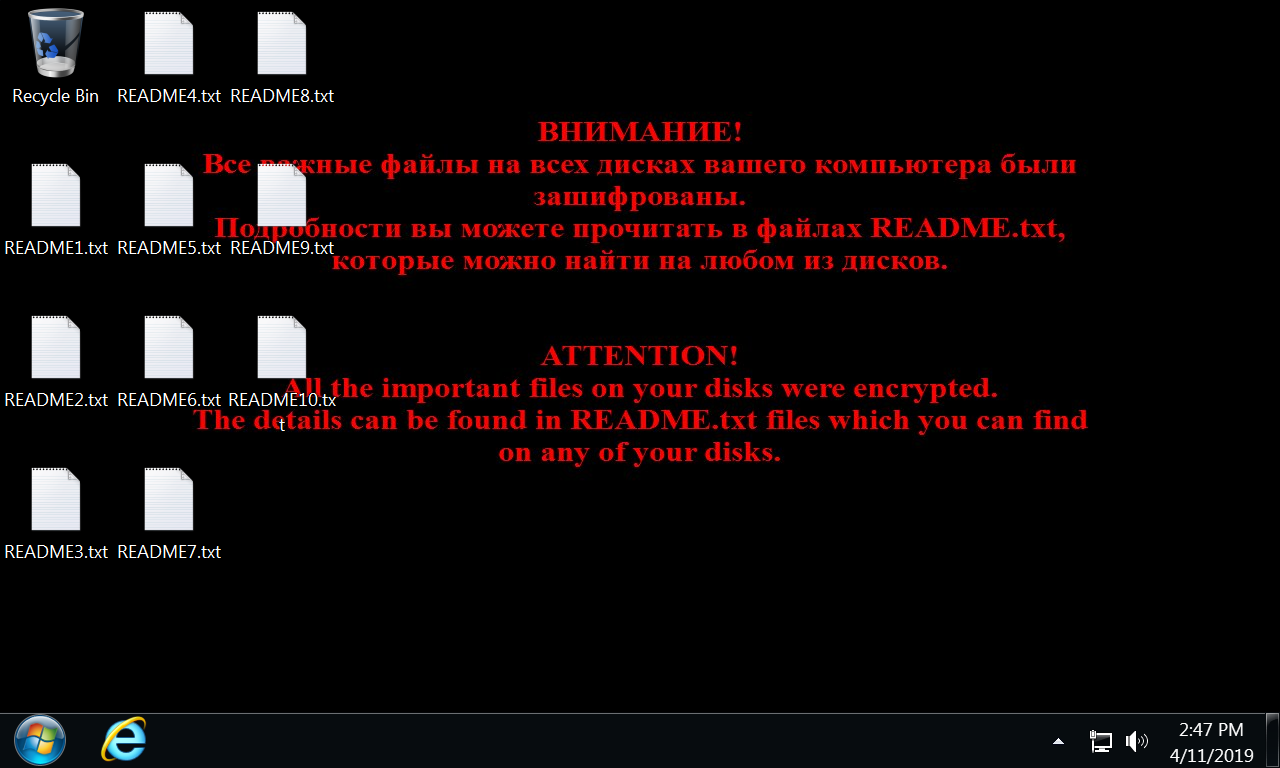
Windows-ransomware Sombra, também conhecido como Troldesh, chegou na Internet no final de 2014 - começo de 2015. Ela está espalhada majorly contra spam, e às vezes – with the use of exploit-packs.For coordination of data, malware creates 256-bites AES keys, e, saving them in the final file, encrypts them with RSA-3072 key. In every folder with encrypted files and on the desktop is placed up to 10 identical README.txt documents with instructions in English and Russian. After work is finished, Shade deletes all shadow files’ copies on all disks.
During the time of its existence, cryptographer also demonstrated some other skills, as cheating clicks on advertising banner and downloading additional malware (Pony, Teamspy, Trojans bancários).
Free decoder for Shade created long time ago and no available on No More Ransome project’s website, Contudo, practice says that malware operators still hope to collect tribute from inattentive users with its help.
Spam messages that are still spread for its sowing, mostly target Russian-speaking public, and among victims are listed Russia, Japão, Alemanha, France and Ukraine citizens. No fim de 2016 was fixed targeting mailing in Australia.
According to Palo Alto, between January and March 2019 malware tour’s geography significantly changed:
- US – 2010 appeals;
- Japão- 1677;
- India – 989;
- Thailand – 723;
- Canada – 712;
- Espanha- 505;
- Russia – 86;
- France – 71;
- UK- 67;
- Kazakhstan – 21.
Most often Shade tried to upload representatives of IT-industry, commercial and educational institutions.
- IT-technology – 5009 appeals;
- Trade – 722;
- Education – 720;
- Telecommunications – 311;
- Finances – 51;
- Transport and logistics – 24;
- Industrial enterprises – 32;
- Professional services (legal assistance) 8;
- Utilities and energy – 4;
- Local administration – 1.
Experts emphasize that data was collected in company’s clients’ base, so lists cannot claim to cover full auditory of current attacks.
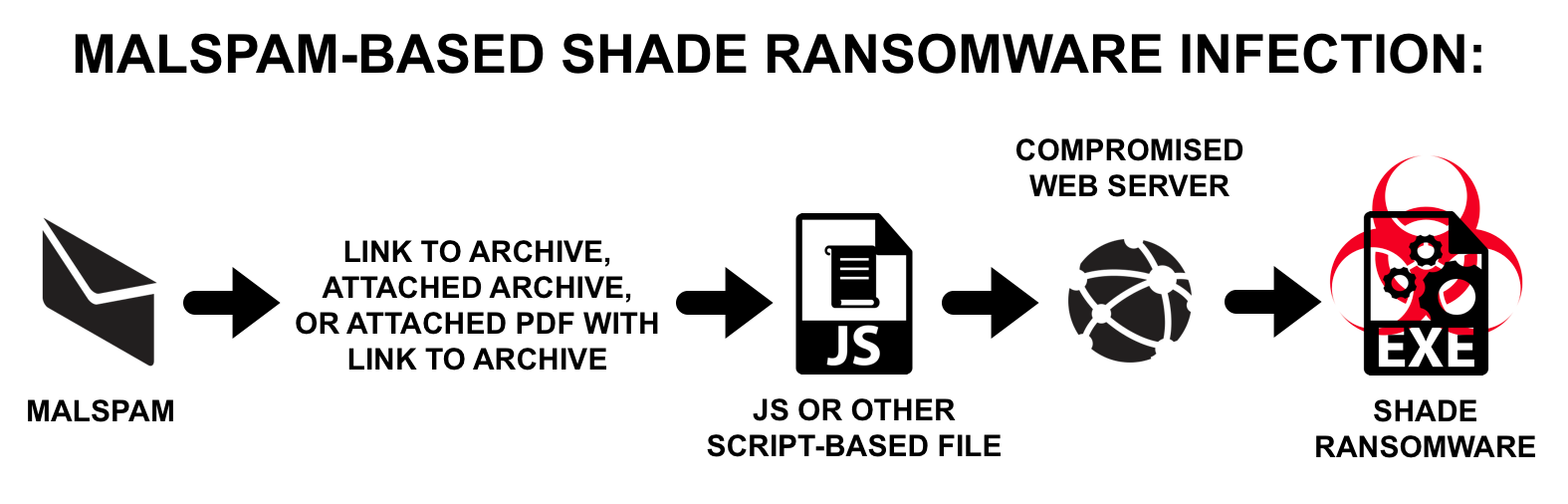
In total researchers accounted 307 Shade samples that spread in frames of new campaign. Analyses demonstrated that extortionist’s identifying marks remained the same.
assim, it still added to the encrypted files .crypted000007 extensão, that was firstly noted in April 2017 (Em 2015-2016 Shade authors often changed this attachment, but later experiments stopped). Message with the demand of buyout is displayed on the screen unchanged during the entire existence of the malware, and the onion-domain for receiving payments has not changed since 2016.
Fonte: https://gbhackers.com
