especialistas da Sophos publicou um relatório, dedicados ao aumento da actividade de MegaCortex cryptographer.
Tseu extorsionista é orientado principalmente para o setor corporativo e usado nos ataques direcionados cuidadosamente planejados.Tais incidentes são uma tendência real na última hora, e muitas grandes empresas sofreram ataques direcionados: vale a pena lembrar LockerGoga “ações heroicas”. Sua vítima foi uma das principais produtoras de alumínio do mundo, a Norsk Hydro, e uma série de grandes empresas químicas.
Outras ameaças com abordagem semelhante são Ryuk, BitPaymer, Dharma, Samsam e Matriz.
O analista da Sophos disse que megacortex foi descoberto em janeiro 2019, quando alguém carregou a amostra de malware no VirusTotal. Desde então, o número de ataques cresce constantemente: no total, os especialistas observaram 76 incidentes, com 47 deles (quase dois terços) ocorrido na última semana.
Ataques MegaCortex afetaram empresas nos EUA, Canadá, Holanda, Irlanda, Itália e França.
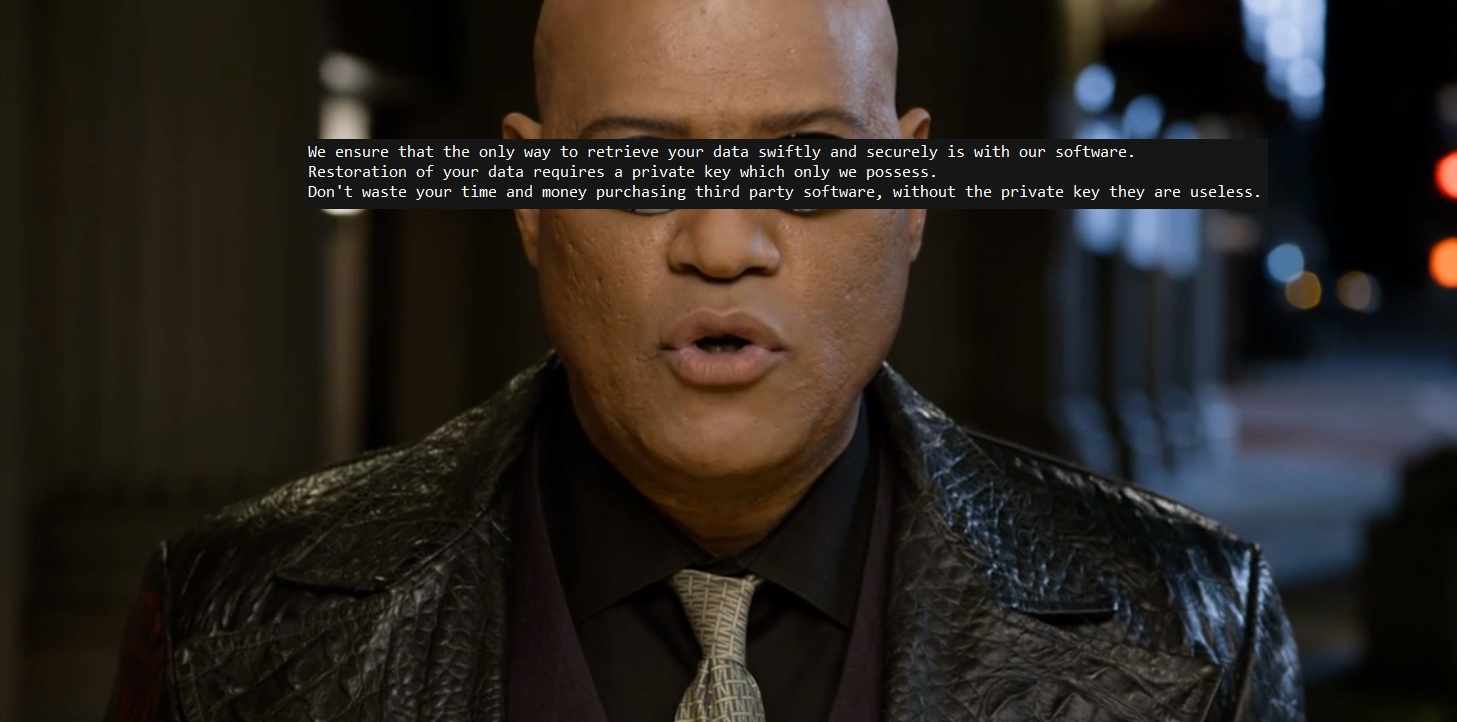
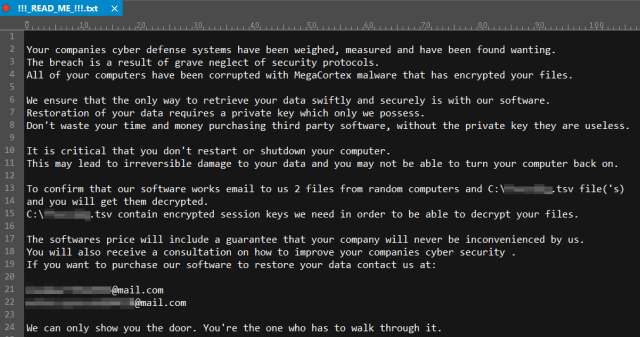
Os operadores dos criptógrafos tentam, o mais rápido possível, alcançar os controladores do domínio e espalhar a ameaça no máximo de sistemas possível. “Reconhecer” o MegaCortex é fácil devido à mensagem dos extorsionários que pode ser vista abaixo, ou alterando as extensões dos arquivos à medida que o malware os altera em uma sequência aleatória de oito símbolos.
No relatório, os pesquisadores da Sophos reconhecem que não conseguiram detectar como o extorsionário entra em hosts infectados. Por sua vez, Especialistas em TI escrevem em redes sociais que o MegaCortex supostamente usa para isso Rietpoof uploader. Esta é uma observação bastante interessante, pois geralmente os criptógrafos entram nas redes por meio da força bruta dos pontos de extremidade RDP mal protegidos ou como uma carga útil da segunda fase do ataque, logo após a infecção de máquinas com fotografar ou trickbot Malware.
Como o ataque parece indicar que uma senha administrativa foi abusada pelos criminosos, também recomendamos a adoção generalizada da autenticação de dois fatores para tudo que atualmente requer apenas uma senha, e pode usar 2FA.
Manter backups regulares de seus dados mais importantes e atuais em um dispositivo de armazenamento off-line é a melhor maneira de evitar o pagamento de um resgate..
Fonte: https://news.sophos.com
