
Especialistas de Fidelis Cybersecurity estudou vulnerabilidades que eram mais populares entre os hackers no primeiro trimestre de 2019.
TEmbora o valor das vulnerabilidades caia drasticamente imediatamente após a publicação de patches para elas, intrusos não se recusam a exploração de bugs tão rapidamente. de fato, hackers continuam a usar as vulnerabilidades até que eles possam chegar a qualquer objetivos dignos com a sua ajuda.“Além de se manter atualizado com as novas técnicas e campanhas de ameaças, nossa equipe de inteligência sente que também é fundamental garantir que não percamos o foco em ameaças já identificadas e existentes”, - considere em Fidelis Cybersecurity.
De acordo com o relatório da Fidelis Cybersecurity, muitas das ameaças mais reais no primeiro trimestre de 2019 são velhos, bugs bem conhecidos, patches para eles chegaram há alguns anos.
assim, quase um terço de todos os problemas detectados no primeiro trimestre (exploits, vulnerabilidades, Malware) encontro 2017 e anteriores.
Por exemplo, os malwares mais ativos eram H-W0rm (Houdini) e CRU, dois Trojans de acesso remoto (RATO) que existem pelo menos desde 2012. Além disso, especialistas sugerem que os desenvolvedores dessas "ferramentas" trabalhem juntos.
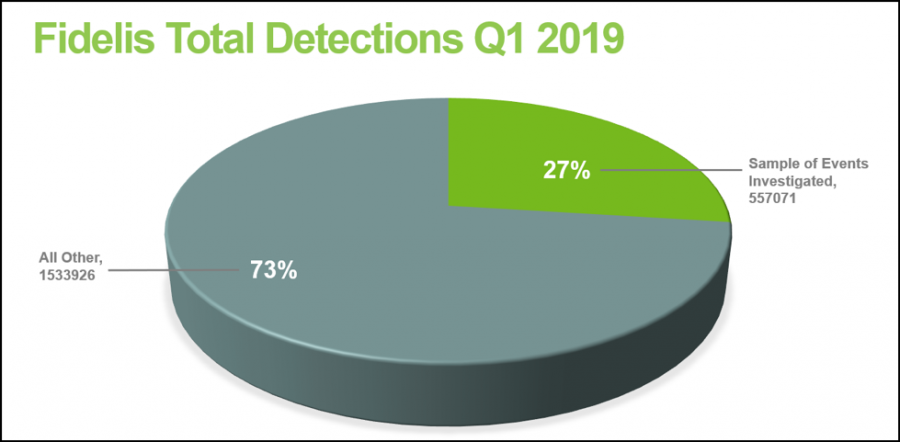
Além disso, analistas contabilizaram que sobre 27% de tentativas de compromisso (Mais que 550 000 incidentes investigados) foram ligados a vulnerabilidades, detectado em 2017 e anteriores.
“Agentes de ameaças e campanhas não são apenas capazes de se ajustar às tendências atuais e atualizar recursos, mas também destaca o foco contínuo em vulnerabilidades pré-existentes e táticas recorrentes para realizar suas campanhas e atividades”, - enfatizar em Fidelis Cybersecurity.
como um resultado, Os 5 problemas antigos mais populares têm esta aparência:
- CVE-2017-8570— Moniker Composto do bug RCE, exploit está publicamente disponível;
- CVE-2017-0143– problema que envolve SMBv1, exploit é publicado por ShadowBrokers (Sinergia eterna) Grupo;
- CVE-2018-11776 - vulnerabilidade RCE no Apache Struts, exploit está publicamente disponível;
- CVE-2017-11882— Vulnerabilidade RCE no Microsoft Office, exploit está publicamente disponível;
- CVE-2009-3129– Vulnerabilidade RCE no Microsoft Excel / Word, foi usado na operação Outubro Vermelho, exploit está publicamente disponível.
Fonte: www.fidelissecurity.com
