
Eksperter av kinesisk selskap KnownSec 404 som utviklet IOT-søk motor ZoomEye, oppdaget farlig sårbarhet i Oracle WebLogic.
ENccording to ZoomEye, på Internett kan finnes mer enn 36 000 tilgjengelige WebLogic Server som er sårbare bak nytt problem. Flertallet av dem ligger i USA og Kina.forskere forklare,that bug is dangerous for all servers Oracle WebLogic with running components WLS9_ASYNC and WLS-WSAT. First component is necessary for asynchronous operations while second is a protective solution. As there is no corrections available yet, experts do not disclose technical details but write that vulnerability is connected with deserialization and enable remote hacker achieving execution of any commands without authorization (with the use of special HTTP-request).
As a preventative measure is recommended either fully eliminate problematic components by deleting them and restarting WebLogic server, or create rules that prohibit requests to /_async/* and /wls-wsat/*.
Internet-security experts from other companies confirm, that vulnerability is really under attacks (hackers are already aware about it) though hackers only investigating as their attacks are limited to scanning in vulnerable parts of WebLogic servers and testing attempts to exploit the bug. Intruders do not try to place malware on their servers or use it for other malicious operations.
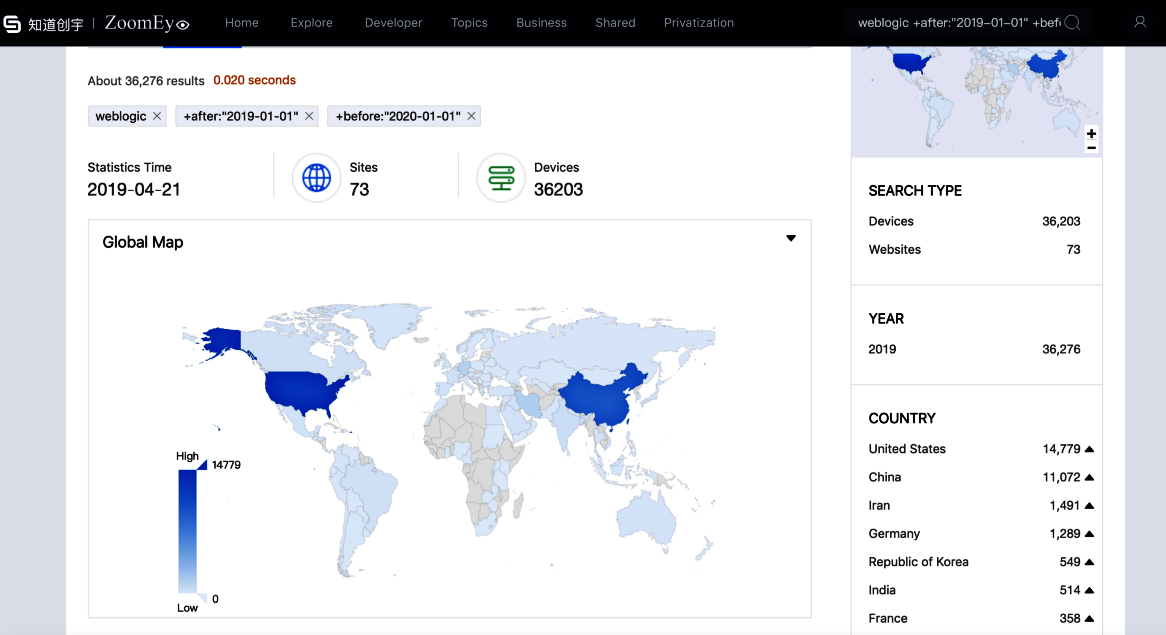
36 000 tilgjengelige WebLogic Server som er sårbare bak nytt problem, Ifølge ZoomEye.
dessverre, this situation will not last for a long time, as powerful and extremely popular in enterprise’s environment Oracle WebLogic servers have been a desirable pray for intruders for a long time. For eksempel, I desember 2018 were fixed cases when hidden mining on Oracle WebLogic servers enriched internet-cheaters for more than $226 000.
Though producers have informed customers about vulnerability, Oracle launched its quarterly patch set only last week, Så, patch for a new bug with arrive only in several months.
By the time this alert was issued, the official still did not release the corresponding fix, which is a “0day” vulnerability. An attacker could exploit this vulnerability to remotely execute commands without authorization, — reported KnownSec 404 spesialister.
Bug received identifier CNVD-C-2019-48814.
