Researchers discovered new version of Dharma Ransomware that uses legal antivirus tools for victims’ attention redirection while all types of files on PC encrypted at the background mode.
DHarma ransomware is famous since 2016, but it still moves through the Internet and chases organizations worldwide. Famous Dharma’s action took place in November 2018, when extorters infected hospital in Texas and encrypted files from its network. Heldigvis, hospital managed to restore them without paying buyout.It seems that such attacks should be well-studied and their consequences neutralized, derimot, Trendmicro recently discovered new species of Dharma extortions. I tillegg, malware acquired new tactics.
Attack begins with an email, For eksempel, from Microsoft.
According to the message that user receives, his computer is allegedly under threat, and it is necessary immediately install antivirus software. For doing so, users had to download proposed file. This file usually contains extortionists’ software and legal and well-known to users ESET AV Remover, a antivirus tool from ESET Company for removal installed antivirus scans from computer.
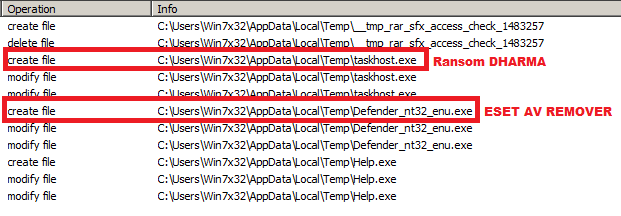
Regardless if users will complete installation of AV Remover or not, extortionist encrypts all files’ types at the background. Endelig, users will have to pay for decryption of files.
“Cybercriminals have history of abuse with authentic instruments. And this recent practice of installer exploitation as a distraction is one more method they experiment with” – says Rafael Senteno from antivirus company TrendMicro.
ESET company was informed about exploitation of their products for Dharma Ransomware promotion and their representatives found necessary to argue:
“The case describes the well-known practice for malware to be bundled with legitimate application(S). In the specific case Trend Micro is documenting, an official and unmodified ESET AV Remover was used. derimot, any other application could be used this way. The main reason is to distract the user, this application is used as a decoy application. ESET threat detection engineers have seen several cases of ransomware packed in self-extract package together with some clean files or hack/keygen/crack recently. So this is nothing new.”
Trendmicro gives recommendations on the protection from similar things.
- Secure email gateways to thwart threats via spam and avoid opening suspicious emails.
- Regularly back up files.
- Keep systems and applications updated, or use virtual patching for legacy or unpatchable systems and software.
- Enforce the principle of least privilege: Secure system administrations tools that attackers could abuse;
- Implement network segmentation and data categorization to minimize further exposure of mission-critical and sensitive data; and disable third-party or outdated components that could be used as entry points.
- Implement defense in depth: Additional layers of security like application control and behavior monitoring helps thwart unwanted modifications to the system or execution of anomalous files.
- Foster a culture of security in the workplace
Kilde: https://blog.trendmicro.com
