
Cybercriminals attacked embassies of European countries in Italia, Liberia, Kenia and other countries after sending its employees fishing letters.
EENs report Check Point researchers, malware letters contained Microsoft Excel documents with headings «Military Financing Program» and “top secret” mark.After activation of malware’s macros from the document were extracted two files. Met name, on the attacked system was downloaded malware library TeamViewer DLL (TV.DLL).
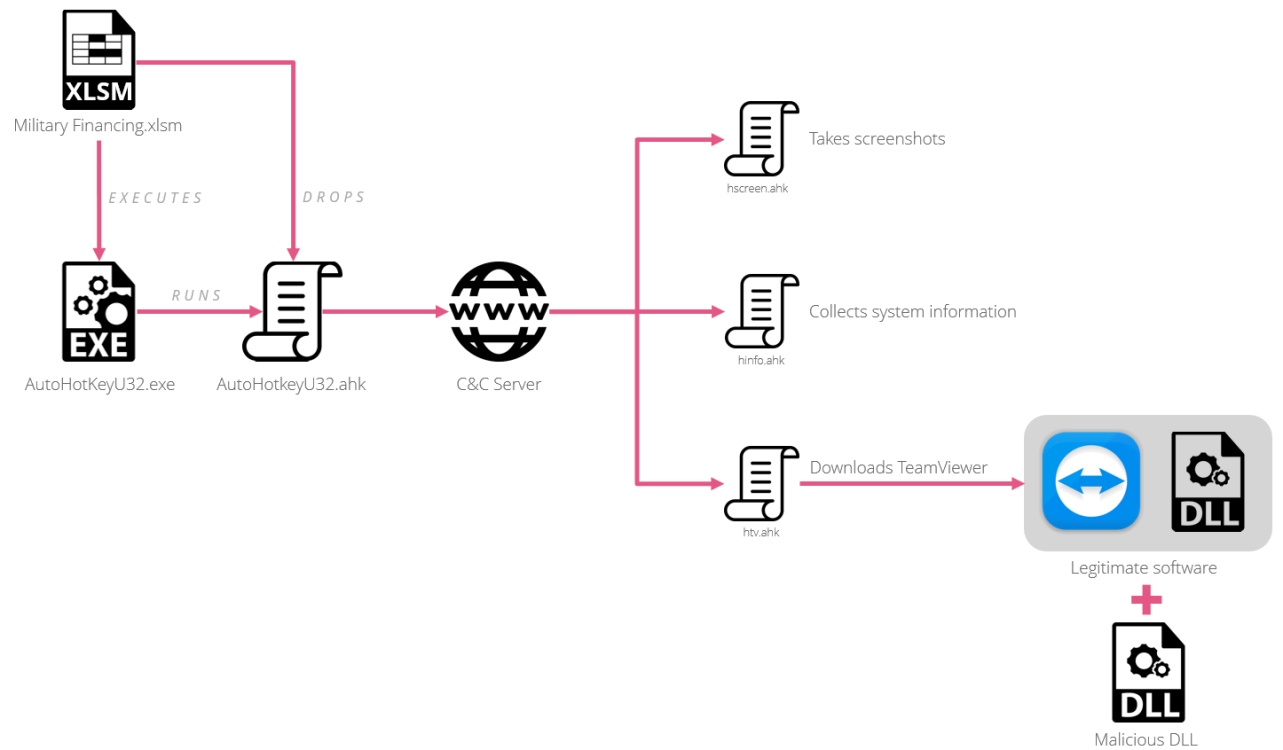
De infectie chain
Intruders are supposedly Russians or at least Russian-speakers, this is obvious from accidentally left Cyrillic alphabet symbols and even whole documents on Russian.
Echter, it is unlikely that they pursue political motives and are “not political hackers”, consider Check Point specialists.
“It is hard to tell if there are geopolitical motives behind this campaign by looking solely at the list of countries it was targeting. Since it was not after a specific region and the victims came from different places in the world.”, — the Check Point press release says.
Government finance officials were among victims of these attacks, and CheckPoint consider this is not a co-incidence.
“They all appear to be handpicked government officials from several revenue authorities,” – reported experts of Check Point.
Specialists even managed to trace one of the criminals; he is famous on the Internet under the name EvaPiks and registered on several hackers’ and carders’ forums.
EvaPiks published instruction on committing described above attacks and even consulted on them. Considering involvement of intruders to carders’ society, researchers suggest they pursue financial interest.
Bron: www.theverge.com
