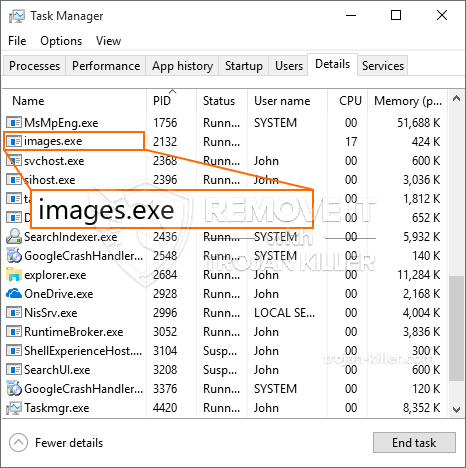
Een gloednieuw, extreem schadelijk cryptocurrency miner virus is eigenlijk ontdekt door veiligheids- en beveiligingsonderzoekers. de malware, riep Afbeeldingen.exe kan doelwitpatiënten infecteren door gebruik te maken van een selectie van methoden. De essentie achter de Images.exe-mijnwerker is om cryptocurrency-mijnwerkeractiviteiten in te zetten op de computersystemen van slachtoffers om Monero-symbolen te verkrijgen tegen de kosten van de slachtoffers. Het resultaat van deze mijnwerker is de verhoogde elektriciteitsrekening en als u het voor langere tijd verlaat, kan Images.exe zelfs uw computeronderdelen beschadigen.
Afbeeldingen.exe: distributiemethoden
De Afbeeldingen.exe malware toepassingen 2 voorkeursmethoden die worden gebruikt voor het computersysteem doelen verontreinigen:
- Payload Levering door middel van Prior Infecties. Als een oudere Images.exe-malware wordt vrijgegeven op de getroffen systemen, kan deze zichzelf onmiddellijk bijwerken of een nieuwere versie downloaden en installeren. Dit is mogelijk via de ingebouwde update-commando dat de release verkrijgt. Dit wordt gedaan door verbinding te maken met een specifieke, vooraf gedefinieerde, door een hacker bestuurde webserver die de malwarecode aanbiedt. De gedownloade infectie zal zeker de naam van een Windows-service krijgen en ook in de “%systeem% temp” plaats. Belangrijke huizen en configuratiebestanden van het besturingssysteem worden gewijzigd om een meedogenloze en stille infectie mogelijk te maken.
- Software Vulnerability Exploits. Er is ontdekt dat de nieuwste variant van de Images.exe-malware wordt veroorzaakt door enkele exploits, algemeen begrepen te worden gebruikt in de ransomware aanslagen. De infecties worden gedaan door zich te richten geopend diensten met behulp van de TCP-poort. De aanslagen worden geautomatiseerd door een hacker bestuurde structuur die opgezocht als de poort open. Als aan deze voorwaarde is voldaan, zal het de oplossing scannen en er informatie over krijgen, bestaande uit elk type variatie en arrangementgegevens. Exploits en populaire gebruikersnaam en wachtwoordmixen kunnen worden gedaan. Wanneer het gebruik wordt afgezet tegen de kwetsbare code, zal de mijnwerker zeker samen met de achterdeur worden vrijgegeven. Dit zal zeker presenteren een dubbele infectie.
Naast deze technieken kunnen ook andere strategieën worden gebruikt. Mijnwerkers kunnen worden verspreid door phishing-e-mails die in bulk op een SPAM-achtige manier worden verzonden en vertrouwen op social engineering-technieken om de slachtoffers in de war te brengen door te denken dat ze een bericht hebben ontvangen van een echte dienst of bedrijf. De virusbestanden kunnen rechtstreeks worden verbonden of in de inhoud van het lichaam worden geplaatst in multimediamateriaal of weblinks naar berichten.
De overtreders kunnen bovendien destructieve touchdown-pagina's maken die zich kunnen voordoen als download- en installatiepagina's van leveranciers, softwaredownloadsites en andere veelgebruikte gebieden. Wanneer ze een vergelijkbaar klinkend domein gebruiken om legitieme adressen en beveiligingscertificeringen te gebruiken, kunnen de gebruikers worden gedwongen om met hen te communiceren. In sommige gevallen alleen het openen van hen kan de mijnwerker infectie veroorzaken.
Een andere strategie zou zeker zijn om gebruik te maken van payload-serviceproviders die kunnen worden verspreid met behulp van de bovengenoemde methoden of via netwerken voor het delen van gegevens., BitTorrent behoort tot een van de meest populaire. Het wordt regelmatig gebruikt om zowel legitieme softwareapplicaties als bestanden en illegale webinhoud te verspreiden. 2 van één van de meest geprefereerde haul service providers zijn de volgende:
Andere technieken die door de oplichters kunnen worden overwogen, zijn onder meer het gebruik van webbrowserkapers - schadelijke plug-ins die geschikt zijn gemaakt voor een van de meest geprefereerde internetbrowsers. Ze worden geüpload naar de juiste repositories met valse gebruikersevaluaties en ontwikkelaarskwalificaties. In de meeste gevallen kunnen de samenvattingen uit schermafbeeldingen, videoclips en ook ingewikkelde samenvattingen die geweldige functieverbeteringen en efficiëntie-optimalisaties aanspreken. Desalniettemin zal na installatie het gedrag van de getroffen webbrowsers zeker veranderen- individuen zullen ontdekken dat ze zeker zullen worden omgeleid naar een door een hacker gecontroleerde touchdown-pagina en dat hun instellingen kunnen worden gewijzigd – de standaard startpagina, zoekmachine evenals nieuwe tabbladen webpagina.

Afbeeldingen.exe: Analyse
De Images.exe-malware is een traditioneel geval van een cryptocurrency-mijnwerker die, afhankelijk van de configuratie, een breed scala aan schadelijke activiteiten kan activeren. Het belangrijkste doel is om ingewikkelde wiskundige taken uit te voeren die gebruik zullen maken van de aangeboden systeembronnen: processor, GPU, geheugen en harde schijf area. De methode die ze gebruiken is door verbinding te maken met een unieke webserver genaamd mining pool van waaruit de gevraagde code wordt gedownload en geïnstalleerd. Zodra een van de taken is gedownload, wordt deze zeker meteen gestart, meerdere omstandigheden kunnen worden uitgevoerd op zodra. Wanneer een opgegeven taak is voltooid, wordt er een andere in zijn gebied gedownload en gaat de maas in de wet door totdat het computersysteem wordt uitgeschakeld, de infectie is verdwenen of er vindt nog een vergelijkbare gelegenheid plaats. Cryptogeld zal zeker worden gecompenseerd naar de correctionele controllers (hacken groep of een enkele cyberpunk) direct naar hun portemonnee.
Een gevaarlijke eigenschap van deze categorie malware is dat voorbeelden zoals deze alle systeembronnen kunnen gebruiken en de doelcomputer vrijwel zinloos kunnen maken totdat het gevaar daadwerkelijk volledig is verwijderd.. Veel van hen bevatten een aanhoudende aflevering waardoor ze erg moeilijk te verwijderen zijn. Deze commando's zullen zeker veranderingen om keuzes te starten maken, configuratiedocumenten en Windows-registerwaarden die ervoor zorgen dat de Images.exe-malware onmiddellijk begint zodra het computersysteem wordt ingeschakeld. De toegang tot herstelmenu's en ook alternatieven kan worden belemmerd, waardoor verschillende handmatige verwijderingsoverzichten bijna waardeloos zijn.
Deze specifieke infectie zal een Windows-oplossing voor zichzelf de configuratie, naar aanleiding van de uitgevoerde veiligheidsanalyse zijn de nagekomen acties geconstateerd:
. Tijdens de miner-procedures kan de aangesloten malware verbinding maken met momenteel actieve Windows-oplossingen en met geïnstalleerde applicaties van derden. Hierdoor ontdekken de systeembeheerders mogelijk niet dat de bronbelasting afkomstig is van een andere procedure.
| Naam | Afbeeldingen.exe |
|---|---|
| Categorie | Trojaans |
| Sub-categorie | cryptogeld Miner |
| gevaren | Hoog CPU-gebruik, Internet snelheidsreductie, PC crashes en bevriest en etc. |
| Hoofddoel | Om geld te verdienen voor cybercriminelen |
| Distributie | torrents, Gratis spellen, Cracked Apps, E-mail, dubieuze websites, exploits |
| Verwijdering | Installeren GridinSoft Anti-Malware om Images.exe te detecteren en te verwijderen |

Dit soort malware-infecties zijn vooral effectief bij het uitvoeren van innovatieve opdrachten als ze zo zijn ingesteld. Ze zijn gebaseerd op een modulaire structuur waardoor de criminele controllers allerlei soorten schadelijk gedrag kunnen beheren. Een van de geprefereerde voorbeelden is het aanpassen van het Windows register – wijzigingsreeksen die door het besturingssysteem zijn gekoppeld, kunnen ernstige efficiëntieverstoringen veroorzaken, evenals het onvermogen om toegang te krijgen tot Windows-oplossingen. Afhankelijk van de reeks wijzigingen kan het de computer ook totaal onbruikbaar maken. Aan de andere kant kan aanpassing van registerwaarden die afkomstig zijn van elke vorm van aangekoppelde applicaties van derden, deze ondermijnen. Sommige toepassingen worden mogelijk helemaal niet vrijgegeven, terwijl andere onverwacht kunnen stoppen met werken.
Deze specifieke miner in zijn huidige versie is gericht op het minen van de Monero-cryptocurrency, inclusief een aangepaste variant van de XMRig CPU-mining-engine. Als de campagnes daarna succesvol blijken, kunnen toekomstige varianten van de Images.exe in de toekomst worden geïntroduceerd. Als de malware maakt gebruik van softwareprogramma susceptabilities tot doel gastheren besmetten, het kan zijn onderdeel van een onveilige co-infectie met ransomware en Trojaanse paarden.
Eliminatie van Images.exe wordt ten zeerste aanbevolen, gezien het feit dat u niet alleen een enorme elektriciteitsrekening riskeert als het op uw pc werkt, de mijnwerker kan er echter ook verschillende andere ongewenste taken op uitvoeren en zelfs uw COMPUTER permanent beschadigen.
Verwijderingsproces van Images.exe
STAP 1. Allereerst, je moet downloaden en te installeren GridinSoft Anti-Malware.
STAP 2. Dan moet je kiezen “Snelle scan” of “Volledige scan”.
STAP 3. Ren naar uw computer te scannen
STAP 4. Nadat de scan is voltooid, je nodig hebt om te klikken op “Van toepassing zijn” knop om Images.exe te verwijderen
STAP 5. Afbeeldingen.exe verwijderd!
video Guide: Hoe GridinSoft Anti-Malware te gebruiken voor het verwijderen van Images.exe
Hoe te voorkomen dat uw pc wordt geïnfecteerd met “Afbeeldingen.exe” in de toekomst.
Een krachtige antivirus oplossing die kan detecteren en blokkeren fileless malware is wat je nodig hebt! Traditionele oplossingen voor het detecteren van malware op basis van virusdefinities, en vandaar dat zij vaak niet kunnen detecteren “Afbeeldingen.exe”. GridinSoft Anti-Malware biedt bescherming tegen alle vormen van malware, waaronder fileless malware zoals “Afbeeldingen.exe”. GridinSoft Anti-Malware biedt cloud-gebaseerde gedrag analyzer om alle onbekende bestanden met inbegrip van zero-day malware te blokkeren. Deze technologie kan detecteren en volledig te verwijderen “Afbeeldingen.exe”.







