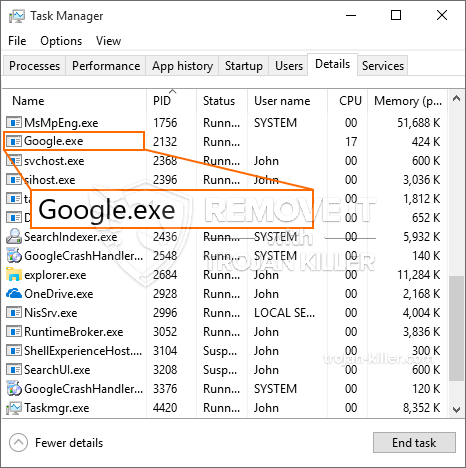
Een gloednieuw, extreem gevaarlijke cryptocurrency miner-infectie is daadwerkelijk gedetecteerd door veiligheids- en beveiligingsonderzoekers. de malware, riep Google.exe kan doelwitslachtoffers infecteren op verschillende manieren. Het belangrijkste punt achter de Google.exe-mijnwerker is om cryptocurrency-mijnwerkerstaken op de computers van patiënten te gebruiken om Monero-symbolen te krijgen op kosten van de patiënt. Het resultaat van deze mijnwerker is de verhoogde stroomkosten en als u het voor langere tijd verlaat, kan Google.exe zelfs uw computersysteemonderdelen beschadigen.
Google.exe: distributiemethoden
De Google.exe malware maakt gebruik van twee voorkeursbenaderingen die worden gebruikt om computersysteemdoelen te infecteren:
- Payload bezorging via Prior Infecties. Als een oudere Google.exe-malware wordt vrijgegeven op de getroffen systemen, kan deze zichzelf onmiddellijk upgraden of een nieuwere versie downloaden. Dit is mogelijk door de geïntegreerde upgrade commando dat de lancering krijgt. Dit gebeurt door aan een bepaalde vooraf vastgestelde-hacker gecontroleerde server die de malware code biedt. Het gedownloade virus krijgt de naam van een Windows-oplossing en wordt ook in de “%systeem% temp” plaats. Vitale woningen en actieve systeemconfiguratiebestanden worden gewijzigd om een meedogenloze en ook stille infectie mogelijk te maken.
- Software programma Kwetsbaarheid Exploits. De nieuwste variant van de Google.exe-malware bleek te worden geactiveerd door sommige ondernemingen, bekend voor toepassing in de ransomware strikes. De infecties worden gedaan door zich te richten geopend oplossingen via de TCP-poort. De aanvallen worden geautomatiseerd door een hacker bestuurde structuur die zoekt uit of de poort open. Als dit probleem is opgelost, wordt de service gecontroleerd en wordt er informatie over hersteld, inclusief alle soorten variatie- en arrangementinformatie. Ventures en ook geprefereerde gebruikersnaam- en wachtwoordmixen kunnen worden gedaan. Wanneer het manipuleren wordt afgezet tegen de risicocode, wordt de mijnwerker samen met de achterdeur ingezet. Dit zal zeker presenteren een dubbele infectie.
Naast deze benaderingen kunnen ook andere technieken worden gebruikt. Mijnwerkers kunnen worden verspreid door phishing-e-mails die in bulk op een SPAM-achtige manier worden verzonden en die afhankelijk zijn van sociale ontwerptrucs om de doelen te verwarren door te geloven dat ze een bericht van een legitieme oplossing of bedrijf hebben gekregen. De virusbestanden kunnen rechtstreeks worden toegevoegd of in de inhoud van de hoofdtekst worden geplaatst in multimedia-inhoud of tekstweblinks.
De wetsovertreders kunnen bovendien kwaadaardige touchdown-webpagina's produceren die webpagina's van leveranciers kunnen downloaden, softwaretoepassing download sites en ook diverse andere vaak benaderd locaties. Wanneer ze vergelijkbare domeinnamen gebruiken als gerenommeerde adressen en ook veiligheids- en beveiligingscertificeringen gebruiken, kunnen de klanten worden overgehaald om contact met hen op te nemen. In sommige gevallen alleen het openen van hen kan verrekenen de mijnwerker infectie.
Een andere methode zou zeker zijn om gebruik te maken van payload-carriers die kunnen worden verspreid met behulp van die methoden of via netwerken voor het delen van gegevens, BitTorrent is slechts een van een van de meest geprefereerde. Er wordt regelmatig gebruik van gemaakt om zowel legitieme softwareprogramma's en gegevens als illegale inhoud te verspreiden. Twee van de meest populaire aanbieders van transportdiensten zijn de volgende:
Andere benaderingen die door de slechteriken kunnen worden overwogen, zijn onder meer het gebruik van browserkapers - onveilige plug-ins die compatibel zijn gemaakt met een van de meest prominente internetbrowsers. Ze worden in de juiste databases geplaatst met valse gebruikersrecensies en ontwerperkwalificaties. Vaak de beschrijvingen kunnen screenshots omvatten, video's en ook mooie samenvattingen aantrekkelijke uitstekende eigenschappenverbeteringen en ook efficiëntie-optimalisaties. Desalniettemin zullen bij de installatie de acties van de beïnvloede browsers veranderen- individuen zullen ontdekken dat ze zeker zullen worden doorgestuurd naar een door een hacker gecontroleerde touchdown-webpagina en dat hun instellingen kunnen worden gewijzigd – de standaard webpagina, internet zoekmachine en ook nieuwe tabbladen webpagina.

Google.exe: Analyse
De Google.exe-malware is een traditionele situatie van een cryptocurrency-mijnwerker die, afhankelijk van de opstelling, een verscheidenheid aan onveilige activiteiten kan veroorzaken. Het belangrijkste doel is om complexe wiskundige taken uit te voeren die het meeste uit de beschikbare systeembronnen halen: processor, GPU, geheugen en ook de harde schijf ruimte. De manier waarop ze werken is door verbinding te maken met een speciale webserver genaamd mining swimming pool waar de vereiste code wordt gedownload en geïnstalleerd. Zodra een van de taken is gedownload, wordt deze meteen gestart, meerdere exemplaren kan zo snel worden uitgevoerd bij. Wanneer een bepaalde taak is voltooid, zal er zeker een andere worden gedownload en geïnstalleerd in zijn gebied en de lus zal doorgaan totdat het computersysteem wordt uitgeschakeld, de infectie is geëlimineerd of andere vergelijkbare gebeurtenis plaatsvindt. Cryptogeld zal worden toegekend aan de criminele controllers (hacken team of een enkele cyberpunk) direct naar hun portemonnee.
Een onveilige eigenschap van deze categorie malware is dat monsters die vergelijkbaar zijn met deze alle systeembronnen kunnen nemen en het computersysteem van de patiënt virtueel onbruikbaar kunnen maken totdat het risico volledig is weggenomen. De meerderheid van hen bevat een meedogenloze installatie waardoor ze echt moeilijk te verwijderen zijn. Deze commando's zullen zeker aanpassingen aan laarsopties maken, installatiegegevens en ook Windows-registerwaarden die ervoor zorgen dat de Google.exe-malware automatisch start zodra de computer wordt ingeschakeld. Toegankelijkheid tot herstel voedselselecties en alternatieven kunnen worden belemmerd, waardoor talloze praktische verwijderingsoverzichten vrijwel zinloos zijn.
Dit bepaalde infectie zal een Windows-service configuratie voor zichzelf, het naleven van de uitgevoerde veiligheidsevaluatie of het naleven van de activiteiten is waargenomen:
. Tijdens de miner-procedures kan de bijbehorende malware aansluiten op reeds actieve Windows-oplossingen en ook op geïnstalleerde applicaties van derden. Hierdoor ontdekken de systeembeheerders mogelijk niet dat de brontonnen afkomstig zijn uit een andere procedure.
| Naam | Google.exe |
|---|---|
| Categorie | Trojaans |
| Sub-categorie | cryptogeld Miner |
| gevaren | Hoog CPU-gebruik, Internet snelheidsreductie, PC crashes en bevriest en etc. |
| Hoofddoel | Om geld te verdienen voor cybercriminelen |
| Distributie | torrents, Gratis spellen, Cracked Apps, E-mail, dubieuze websites, exploits |
| Verwijdering | Installeren GridinSoft Anti-Malware om Google.exe te detecteren en te verwijderen |

Dit soort malware-infecties zijn vooral effectief in het uitvoeren van geavanceerde opdrachten als ze zo zijn geconfigureerd. Ze zijn gebaseerd op een modulair raamwerk waardoor de criminele controllers allerlei onveilige acties kunnen orkestreren. Onder de populaire gevallen is de wijziging van het Windows-register – aanpassingenreeksen gerelateerd aan het besturingssysteem kunnen grote efficiëntieonderbrekingen veroorzaken, evenals het niet openen van Windows-oplossingen. Afhankelijk van de omvang van de wijzigingen kan het de computer ook totaal onbruikbaar maken. Aan de andere kant kan de controle van registerwaarden die afkomstig zijn van elke vorm van door derden ingestelde applicaties, deze ondermijnen. Sommige toepassingen worden mogelijk niet volledig geïntroduceerd, terwijl andere plotseling niet meer werken.
Deze specifieke miner in zijn bestaande variant is gericht op het minen van de Monero-cryptocurrency, bestaande uit een aangepaste variant van de XMRig CPU-mining-engine. Als de campagnes daarna effectief blijken te zijn, kunnen toekomstige versies van Google.exe in de toekomst worden vrijgegeven. Als de malware maakt gebruik van software kwetsbaarheden te misbruiken doelhosts infecteren, het kan een deel van een gevaarlijke co-infectie met ransomware zijn evenals Trojans.
Verwijdering van Google.exe wordt ten zeerste aanbevolen, gezien het feit dat u niet alleen hoge elektriciteitskosten riskeert als het op uw COMPUTER werkt, maar de mijnwerker kan er ook andere ongewenste taken op uitvoeren en zelfs uw COMPUTER volledig beschadigen.
Google.exe verwijderingsproces
STAP 1. Allereerst, je moet downloaden en te installeren GridinSoft Anti-Malware.
STAP 2. Dan moet je kiezen “Snelle scan” of “Volledige scan”.
STAP 3. Ren naar uw computer te scannen
STAP 4. Nadat de scan is voltooid, je nodig hebt om te klikken op “Van toepassing zijn” knop om Google.exe te verwijderen
STAP 5. Google.exe verwijderd!
video Guide: Hoe GridinSoft Anti-Malware te gebruiken voor het verwijderen van Google.exe
Hoe te voorkomen dat uw pc wordt geïnfecteerd met “Google.exe” in de toekomst.
Een krachtige antivirus oplossing die kan detecteren en blokkeren fileless malware is wat je nodig hebt! Traditionele oplossingen voor het detecteren van malware op basis van virusdefinities, en vandaar dat zij vaak niet kunnen detecteren “Google.exe”. GridinSoft Anti-Malware biedt bescherming tegen alle vormen van malware, waaronder fileless malware zoals “Google.exe”. GridinSoft Anti-Malware biedt cloud-gebaseerde gedrag analyzer om alle onbekende bestanden met inbegrip van zero-day malware te blokkeren. Deze technologie kan detecteren en volledig te verwijderen “Google.exe”.







