Onbekende indringers kregen toegang tot gegevens van 's werelds grootste bibliotheek met afbeeldingen voor containers die meer dan lekken veroorzaakten 190 inloggegevens van duizenden gebruikers.
Dbode Hub ontwikkelaars ontdekten dat derden ongeoorloofde toegang kregen tot een van de projectdatabases waarin gegevens van niet-financiële gebruikers werden opgeslagen.“Op donderdag, 25 april, 2019, we ontdekten ongeoorloofde toegang tot een enkele Hub-database waarin een subset van niet-financiële gebruikersgegevens was opgeslagen,” zei Kent Lam, Directeur van Docker-ondersteuning.
Zoals benadrukt, indringers bleven relatief kort in het systeem, Echter, volgens vooronderzoek, dat was genoeg om een compromis te sluiten 190 000 rekeningen dat bestaat bijna 5% van alle Docker Hub-gebruikers.
Bij de aanval werden de namen van gebruikers gecompromitteerd, hashes van wachtwoorden, en tokens voor GitHub- en Bitbucket-opslagplaatsen die werden gebruikt voor geautomatiseerde Docker-assemblages.
Bovengenoemde tokens die zijn opgeslagen in Docker Hub, stelt ontwikkelaars in staat om codes van hun projecten aan te passen en automatisch afbeeldingen te maken op Docker Hub. Als de indringer tokens krijgt, het zal hem toegang geven tot privé-repository's en deze wijzigen afhankelijk van de toegewezen tokenmachtigingen. Afbeelding compromitteren en code wijzigen, hacker zal de toeleveringsketen ernstig beschadigen, omdat Docker Hub-images vaak worden gebruikt in server- en applicatieconfiguraties.
Het Docker Hub-team stelde gebruikers op de hoogte en reset wachtwoorden van gecompromitteerde accounts.
“Voor gebruikers met autobuilds die mogelijk zijn getroffen, we hebben GitHub-tokens en toegangssleutels ingetrokken, en vraag om opnieuw verbinding te maken met uw opslagplaatsen en beveiligingslogboeken te controleren om te zien of er onverwachte acties hebben plaatsgevonden,” Lamb zei in de e-mail die het bedrijf klanten stuurde.
Het team van Docker heeft alle gecompromitteerde tokens en toegangssleutels al ingetrokken, Echter, alle ontwikkelaars die geautomatiseerde Docker Hub-constructors gebruiken, wordt ten zeerste aanbevolen om alle projecten te controleren op ongeoorloofde toegang.
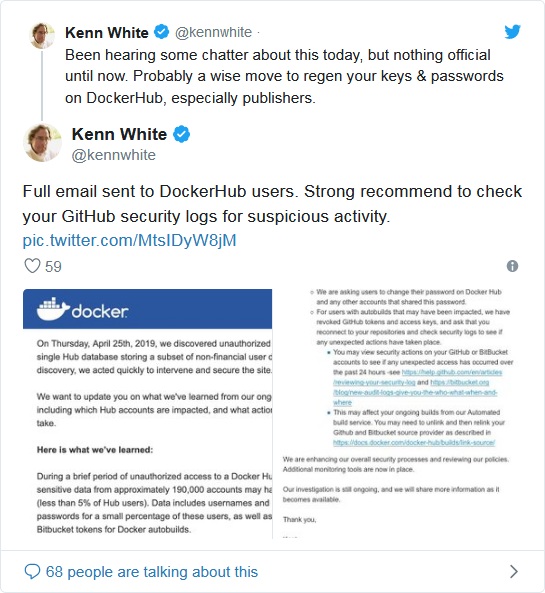
Experts delen op internet een brief van Docker Hub
Hoewel hacker toegang tot 5% van de accounts van gebruikers lijkt geen kritiek probleem te zijn, het spectrum van vertakkingen kan breed zijn. Aangezien de meeste Docker Hub-gebruikers werknemers zijn van grote bedrijven, ze zouden hun accounts kunnen gebruiken voor het maken van containers die later worden toegepast in echte bedrijfsomgevingen. Na aanval, hackers kunnen malwarecode in IT-systemen van grote bedrijven wereldwijd introduceren.
Onderzoek naar incident en beoordeling van mogelijke schade gaat door.
Bron: https://www.zdnet.com
