Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine

Encountering a “Trojan.Malware.300983.Susgen” detection from MaxSecure can be alarming, but this generic detection often flags legitimate software as malicious. Our guide explains what this detection means, why it frequently leads to false positives, and provides clear steps to distinguish between genuine threats and harmless files. Learn expert methods to verify detections and properly respond to both real threats and false alarms.
| Detection Name | Trojan.Malware.300983.Susgen (MaxSecure) |
| Detection Type | Generic/Suspicious Behavior Heuristic |
| False Positive Rate | Very High (particularly with custom and developer software) |
| Common False Positives | Software installers, utilities with registry access, networking tools |
| Impact | Legitimate software quarantine, installation interruption, workflow disruption |
| Resolution Methods | Verification through multiple scanners, whitelist creation, source examination |
The “Trojan.Malware.300983.Susgen” detection from MaxSecure is a generic identification that follows a specific naming pattern:
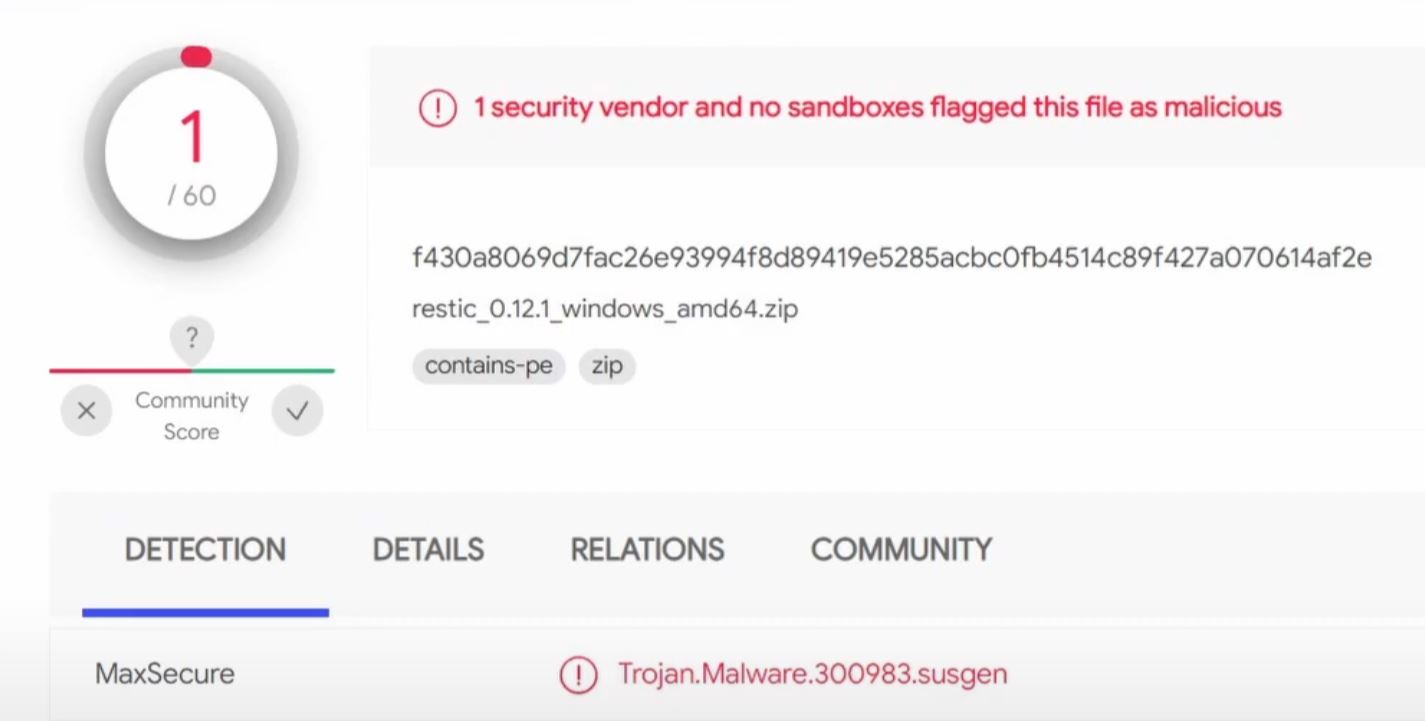
This detection is triggered when MaxSecure’s heuristic engine identifies behavior patterns that might be associated with malicious software, but cannot match the sample to a known specific threat. It represents a “suspicion” rather than a confirmed identification, with the detection engine essentially saying: “This looks suspicious based on our behavioral analysis, but we’re not certain enough to assign a specific malware name.”
MaxSecure’s generic Susgen detections are particularly prone to false positives due to several underlying factors:
| Factor | Explanation | Impact on False Positive Rate |
|---|---|---|
| Behavior-Based Detection | Triggers on suspicious activities rather than malware signatures | Very High – Many legitimate programs flagged |
| Aggressive Heuristics | Low threshold for “suspicious” behavior classification | High – Higher detection rates but increased false positives |
| Limited Allowlisting | Insufficient whitelisting of legitimate software behavior patterns | High – Common utilities and tools frequently misidentified |
| Contextual Limitations | Unable to distinguish between similar actions based on context | Medium – Can’t differentiate legitimate admin tasks from malicious ones |
| Update Frequency | Definitions may not keep pace with legitimate software changes | High – Newly updated legitimate software often flagged |
Based on user reports and analysis, these categories of legitimate software are most frequently misidentified by this detection:
Source: Analysis of user-reported MaxSecure false positives, 2025
These specific legitimate software actions commonly trigger the detection:
When you encounter this generic detection, follow this systematic verification process:
Source: Security analysis methodology for generic detections, 2025
A second opinion scan is essential for verifying ambiguous detections like “Trojan.Malware.300983.Susgen”. Trojan Killer provides reliable verification with lower false positive rates:

Trojan Killer’s specialized scanning engine is particularly effective for verifying these detections because:
When two independent security solutions agree on a threat classification, it significantly increases confidence in the detection’s legitimacy. Conversely, if Trojan Killer verifies a file as clean, it strongly suggests the MaxSecure detection is a false positive.
These documented cases illustrate common false positive scenarios:
| Software | Behavior Triggering Detection | Verification Method |
|---|---|---|
| Custom software installer | Writes to multiple system locations and modifies registry | Publisher verification, controlled installation testing |
| System optimization tool | Registry cleaning functionality and startup modification | Digital signature validation, alternative scanner verification |
| Network monitoring utility | Packet inspection and network driver installation | Source verification, behavior analysis in isolated environment |
| Game modification tool | Memory manipulation and dynamic code generation | Community verification, sandbox testing |
| Development compiler output | Unusual executable structure and code patterns | Comparison with known-good builds, function analysis |
Understanding how different security solutions handle generic detections helps contextualize MaxSecure’s approach:
| Security Solution | Handling of Generic Detections | False Positive Rate | User Experience |
|---|---|---|---|
| MaxSecure | Aggressive flagging of suspicious behavior patterns | High – Many legitimate tools flagged | Frequent alerts requiring user judgment |
| Microsoft Defender | Cloud-based intelligence with reputation scoring | Moderate – Balanced approach | Fewer alerts, more contextual information |
| Typical Enterprise EDR | Behavioral analysis with environmental context | Moderate – Organizational baselines help | Detailed alerts with contextual information |
| Trojan Killer | Precision-focused with minimal generic categorization | Low – Emphasis on reducing false positives | Clearer threat classifications with explanations |
The Microsoft Security Intelligence approach to generic detections demonstrates the value of cloud-based verification and prevalence data in reducing false positives while maintaining effective protection.
While many of these detections are false positives, some represent genuine threats. Consider these risk factors:
For cases where you’re uncertain, consult our guide on the potential risks of unaddressed malware to make an informed decision.
Implement these strategies to minimize disruptive false positive detections:
MaxSecure’s “Trojan.Malware.300983.Susgen” detection exemplifies the constant balancing act in cybersecurity between comprehensive threat detection and minimizing false positives. While these generic detections help identify potential threats that don’t match known signatures, they inevitably result in legitimate software being flagged.
By following the verification procedures outlined in this guide, you can confidently distinguish between false positives and genuine threats, addressing each appropriately. Remember that no security solution is infallible, and a layered approach using multiple tools alongside MaxSecure provides the most robust protection.
Ultimately, understanding how these detections work empowers you to make informed security decisions, maintaining both system protection and software functionality without unnecessary disruption to your workflow.
No. While this detection has a high false positive rate, it can identify genuine threats. Each detection requires verification through the methods described in this guide before dismissal.
These generic detections allow MaxSecure to flag potentially malicious files based on behavioral patterns when they can’t match them to known malware signatures. This approach catches more potential threats but generates more false positives.
Adding specific, carefully verified exceptions for legitimate software should not significantly impact security. The key is to be precise with exclusions—only exclude specific files you’ve thoroughly verified rather than entire folders or file types.
Before uninstalling, try updating the software and creating appropriate exclusions for verified false positives. If problems persist, consider complementing or replacing it with solutions like specialized anti-malware tools that have lower false positive rates.
Yes. Machine learning detection systems improve as they receive more training data, including feedback on false positives. This is why reporting false positives is important – it helps the system learn and reduce similar false detections in future updates.
Yes, many antivirus products generate false positives with different naming conventions. Our guides on BKAV Pro false positives and Trapmine’s “Suspicious.low.ml.score” detection provide information on other common false positive scenarios.