Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine

LegionLocker is a dual-purpose ransomware and screen locker that deploys multiple persistence mechanisms while encrypting files and locking access to the system. This malware communicates through Telegram, requiring victims to contact the operators via the @xexeza handle to negotiate ransom payments. First identified in early 2025, LegionLocker appears to originate from Russia and employs both file encryption and screen locking techniques to maximize pressure on victims. This analysis examines its technical characteristics, persistence methods, and provides protection strategies to defend against this emerging threat.
LegionLocker emerged in early 2025 as a combined screen locker and file encryptor targeting primarily Windows systems. What distinguishes this ransomware is its hybrid approach – not only encrypting files but also locking users out of their systems by forcibly terminating Explorer.exe and displaying a Russian-language ransom interface with a blue background.
The malware claims to be operated by the “Legion hacker group” – a previously unknown threat actor that appears to be of Russian origin based on language analysis and infrastructure connections. The operators provide only a Telegram contact handle (@xexeza) for communication, avoiding the more complex payment portal systems used by larger ransomware operations.
LegionLocker applies aggressive persistence techniques, including multiple startup registry keys, Winlogon shell modifications, and hidden files, making it particularly difficult to remove once a system is infected. The combination of screen locking and file encryption creates a sense of urgency and makes recovery without paying the ransom especially challenging for victims without proper backups.
LegionLocker employs several technical features that enhance its effectiveness and complicate removal:
The combination of these features indicates a ransomware operation designed for maximum impact and persistence, making it difficult for victims to regain control of their systems without restoring from backups or formatting their systems.
Source: Analysis of LegionLocker ransomware infection process, 2025
Based on analysis of similar ransomware operations and the identified samples, LegionLocker likely spreads through:
The relatively small size of the executable (193KB) suggests it may be designed to be easily distributed through multiple vectors rather than containing complex functionality within a large package. This could indicate the operators are targeting a higher volume of smaller victims rather than conducting highly targeted attacks against specific large organizations.
The malware has been observed deployed as “lc.exe” but likely uses other generic names to avoid detection, potentially impersonating legitimate Windows system files or common utilities to remain inconspicuous until execution.
LegionLocker employs an unusually comprehensive set of persistence mechanisms to ensure it continues running after system restarts:
The ransomware creates multiple Run and RunOnce registry keys, including:
# Windows Current User Run KeysHKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_1 = "AWindowsService.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_2 = "taskhost.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_3 = "windowsx-c.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_4 = "System.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_5 = "_default64.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_6 = "native.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_7 = "ux-cryptor.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_8 = "crypt0rsx.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WindowsInstaller = "C:\Users\[username]\AppData\Local\Temp\lc.exe -startup"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\MSEdgeUpdateX = "C:\Users\[username]\AppData\Local\Temp\lc.exe"# Windows Current User RunOnce KeysHKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\System3264Wow = "C:\Users\[username]\AppData\Local\Temp\lc.exe --init"HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\OneDrive10293 = "C:\Users\[username]\AppData\Local\Temp\lc.exe /setup"HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\WINDOWS = "C:\Users\[username]\AppData\Local\Temp\lc.exe --wininit" |
The malware modifies the Winlogon shell key to execute itself upon user login:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell = "C:\Users\[username]\AppData\Local\Temp\lc.exe" |
LegionLocker uses attrib.exe to set hidden, system, and read-only attributes on files in multiple directories:
attrib +h +s +r +i /D |
This makes it difficult for users to locate and remove malicious files, as they won’t appear in standard directory listings without specifically configuring Explorer to show hidden and system files.
The combination of these persistence mechanisms demonstrates a thorough approach designed to make removal difficult and ensure the malware remains active even after attempted cleanup.
LegionLocker uses a text-based ransom note and screen locker interface to communicate with victims:
The ransomware drops “info-Locker.txt” files in multiple locations including:
The ransom note (translated from Russian) contains a brief message:
[RANDOM_NUMBER] Ooops! Your files are encrypted by the Legion hacker group! Telegram for contact: @xexeza |
The inclusion of a random number may be an attempt to create unique identifiers for each victim, though it’s considerably less sophisticated than the UUID systems used by more advanced ransomware operations.
LegionLocker also creates a blue-screen interface with a more detailed ransom message. The interface informs victims:
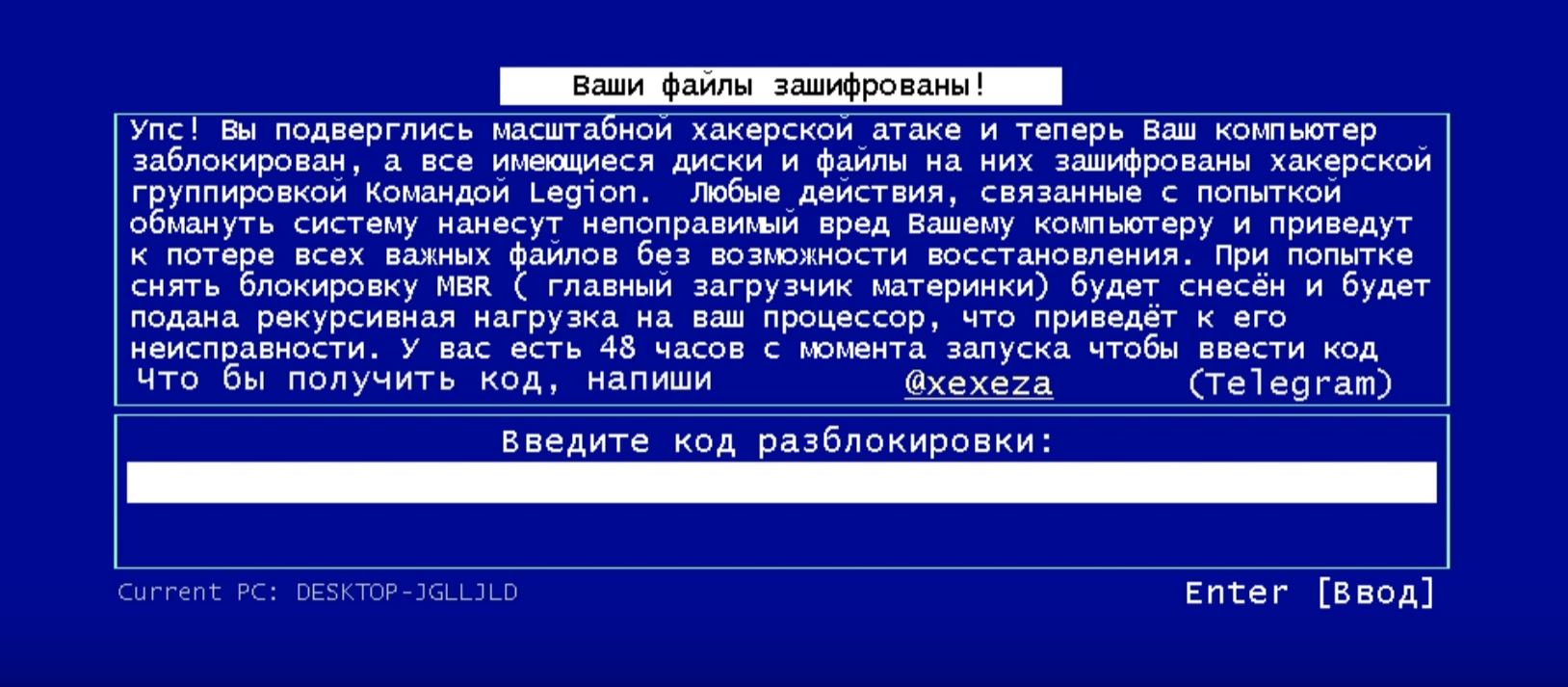
LegionLocker ransom interface displayed after the malware terminates Explorer.exe. The screen has a distinctive blue background with Russian text that reads “Your files are encrypted!” and instructions to contact the attackers via Telegram.
The screen locker component forcibly terminates Explorer.exe using the taskkill command:
taskkill.exe /im Explorer.exe /f |
This prevents normal interaction with the Windows desktop until the ransom is paid or the malware is removed.
Unlike more sophisticated ransomware operations that use TOR-based payment portals or secure messaging systems, LegionLocker simply directs victims to contact the operators through Telegram using the handle @xexeza. This simpler approach suggests the operation may be smaller and less established than major ransomware groups.
The use of Telegram provides the attackers with relatively secure, end-to-end encrypted communications while being more accessible to average users than TOR or specialized communication platforms like those used by larger ransomware operations.
Organizations should monitor for the following indicators that may suggest a LegionLocker infection:
# Ransomware executable File: lc.exeSize: 193 KBMD5: 98609581725d9cf7f5200dbb02266cd6SHA1: 5f8a127fb69172947c6212b3a466279794b702a4SHA256: 01b57b7ab116a353b5d7d778b62c1a99f7f9f10e6af3a524aa13b9e3a588d751SSDEEP: 6144:pS4OgfnRtcCUsnzUCpM69/KImQi/6ebl:srg/jcy# Ransom noteinfo-Locker.txt (multiple locations)MD5: a127062880baf206adf8231a696fa34f# File locationsC:\Users\[username]\AppData\Local\Temp\lc.exeC:\Users\[username]\Desktop\info-Locker.txtC:\Users\[username]\Documents\info-Locker.txtC:\Users\[username]\Downloads\info-Locker.txtC:\Users\Public\Desktop\info-Locker.txt |
# Registry modificationsHKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell = "C:\Users\[username]\AppData\Local\Temp\lc.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_1 = "AWindowsService.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_2 = "taskhost.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_3 = "windowsx-c.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_4 = "System.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_5 = "_default64.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_6 = "native.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_7 = "ux-cryptor.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WIN32_8 = "crypt0rsx.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WindowsInstaller = "C:\Users\[username]\AppData\Local\Temp\lc.exe -startup"HKCU\Software\Microsoft\Windows\CurrentVersion\Run\MSEdgeUpdateX = "C:\Users\[username]\AppData\Local\Temp\lc.exe"HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\System3264Wow = "C:\Users\[username]\AppData\Local\Temp\lc.exe --init"HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\OneDrive10293 = "C:\Users\[username]\AppData\Local\Temp\lc.exe /setup"HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\WINDOWS = "C:\Users\[username]\AppData\Local\Temp\lc.exe --wininit" |
Source: LegionLocker ransomware capabilities assessment based on technical analysis, 2025
Protecting against LegionLocker requires comprehensive defense measures. Organizations should implement the following protective approaches:
Organizations should also develop specific incident response plans for screen locker ransomware like LegionLocker. As noted in our comprehensive malware removal guide, having established protocols in place before an attack occurs significantly reduces recovery time and potential damage.
If a system has been infected with LegionLocker, follow these steps to remove the malware:
For a more thorough cleanup, Trojan Killer can automatically detect and remove all components of LegionLocker in a single scan, including hidden registry entries and files with modified attributes.

LegionLocker differs from other ransomware families in several key aspects:
Compared to NBA Ransomware: While NBA Ransomware uses sophisticated components like Cobalt Strike and communicates through qTox, LegionLocker employs simpler techniques but focuses more on system locking in addition to encryption. NBA targets corporate networks with more advanced evasion mechanisms, while LegionLocker appears to target individual users with more aggressive screen locking.
Compared to Maximsru Ransomware: Both ransomware families communicate through direct messaging channels (Telegram for LegionLocker, email for Maximsru), but LegionLocker employs significantly more persistence mechanisms and adds screen locking functionality not present in Maximsru.
Compared to lockscreen ransomware: Unlike traditional screen lockers that only restrict access without file encryption, LegionLocker combines both approaches for maximum impact. This hybrid approach increases pressure on victims who not only lose access to their systems but also face data loss.
LegionLocker represents a concerning evolution in ransomware design, combining multiple attack vectors (screen locking and file encryption) with aggressive persistence mechanisms. While it lacks some of the more sophisticated features of enterprise-targeting ransomware like NBA or Krypt, its hybrid approach makes it particularly disruptive for home users and small businesses.
Key characteristics that define LegionLocker include:
The emergence of LegionLocker highlights the ongoing evolution of ransomware threats toward multi-faceted approaches that increase the pressure on victims to pay. Organizations and individuals should focus on preventive measures including robust backup strategies, email filtering, and endpoint protection solutions to reduce the risk of infection.
With proper security measures in place and regular system backups, the impact of LegionLocker and similar ransomware threats can be significantly mitigated, reducing the incentive for attackers to continue using these tactics.