Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine

Krypt Ransomware employs double extortion tactics by both encrypting files and claiming to steal sensitive data. This malware establishes communication through multiple channels including a TOR-based chat interface, email, and Telegram. First observed in early 2025, Krypt targets organizations and individuals by encrypting data, changing desktop wallpapers, and dropping ransom notes that guide victims to communication channels. This analysis examines its technical characteristics, distribution methods, and provides protection strategies to defend against this threat.
Krypt ransomware emerged in early 2025, combining file encryption with data theft tactics to increase pressure on victims. This malware follows the “double extortion” approach, where attackers encrypt the victim’s files and claim to have stolen sensitive data, threatening to publish it if the ransom isn’t paid.
What distinguishes Krypt from other ransomware families is its multi-channel communication strategy. The actors behind Krypt provide victims with three different ways to establish contact: a TOR-based chat interface with a unique victim ID, email addresses, and a Telegram account. This redundancy ensures that victims can reach the attackers, increasing the likelihood of ransom payment.
The ransomware includes anti-analysis techniques, including UPX packing and the ability to disable security features like Windows Defender real-time protection and System Restore points. These capabilities make it difficult for security tools to detect and for victims to recover without paying the ransom.
Krypt ransomware employs several technical features that maximize impact and minimize the chance of detection or recovery:
The combination of these techniques makes Krypt effective, as it encrypts files and makes recovery without paying the ransom difficult. The implementation suggests that the actors behind Krypt have experience in ransomware development or have adapted code from other established ransomware families.
Source: Analysis of Krypt ransomware attack methodology, 2025
Based on analysis of Krypt ransomware incidents and similar threats, this malware is distributed through several common vectors:
Unlike some ransomware that targets specific industries or regions, Krypt appears to be opportunistic, with a wide range of potential victims. However, the presence of geographic location checking in the code suggests the operators may avoid encrypting systems in certain countries, possibly to evade legal consequences or to prevent targeting their own region.
After initial access is gained, the ransomware executes its payload, disables security features, and begins the encryption process. The initial access techniques suggest that Krypt may be deployed by threat actors who have established methods for compromising target networks.
Source: Analysis of Krypt and similar ransomware distribution vectors, 2025
Krypt ransomware employs an approach to impact victims through both encryption and data theft:
The ransom note explicitly states: “All your files are encrypted and stolen.” This double extortion tactic has become common among ransomware operators, as it provides additional leverage to pressure victims into paying. Even if victims have proper backups and could restore their encrypted files, the threat of sensitive data being leaked creates an incentive to pay the ransom.
While the actual data exfiltration capabilities of Krypt have not been conclusively verified in technical analysis, the threat should be considered. Modern ransomware operations frequently include data theft components, and the ransom note’s claims align with this trend.
The ransomware appears to target a wide range of file types across the system, focusing particularly on:
Like most ransomware, Krypt avoids encrypting certain system files to ensure the computer remains operational enough for the victim to be able to contact the attackers and potentially pay the ransom.
Krypt ransomware employs a multi-channel communication strategy to ensure victims can reach the attackers, with detailed instructions provided in the ransom note:
The #HowToRecover.txt file contains several key elements:
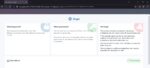
The chat interface accessible via TOR provides a sleek, professional appearance with a skull logo branded as “Krypt.” The interface includes sections explaining what happened, what guarantees the attackers offer, and warnings against using recovery companies.
While the ransom note does not specify exact payment amounts, the attackers likely negotiate different ransom amounts based on the perceived ability of the victim to pay. This targeted approach is common in modern ransomware operations, with payments typically demanded in cryptocurrency (likely Bitcoin or Monero).
Organizations and individuals should monitor for the following indicators that may suggest a Krypt ransomware infection or attack in progress:
# Ransomware executable MD5: a410448d110e6cfaa07cc22ff9942d2cSHA1: a0e9242ec69eb2259a7bde94ccc2a71cfde0e1fbSHA256: cb97e89541d61de376a4e041b66f80181811dfadb4b4d6c094a42632017604c2# Ransom noteC:\PerfLogs\#HowToRecover.txtC:\#HowToRecover.txt[Various directories]\#HowToRecover.txt# Modified desktop backgroundCustom wallpaper with ransom message |
# Desktop wallpaper changeHKCU\Control Panel\Desktop\Wallpaper# Disable Windows DefenderHKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableRealtimeMonitoringHKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware# Disable System RestoreRegistry modifications to disable System Restore functionality |
# Potential C2 communicationUnexpected outbound connections from normally non-internet-facing processesPossible data exfiltration to unknown external servers# TOR communicationConnections to TOR network (if the ransomware includes a built-in TOR client)# Contact pointshttp://decryptjhpol6zezc72xb2mofmi6o7xlvacnrpbuiczz2sz5ljurg4id.onion/chat/[VICTIM_ID]http://decryptrrx2fojgfcof3aesrklj5obq7nmizyokq7ohzqxtwfcvtmwad.onion/chat/[VICTIM_ID] |
Based on analysis, Krypt ransomware employs the following MITRE ATT&CK techniques:
Protecting against Krypt ransomware and similar threats requires a defense-in-depth approach. Organizations and individuals should implement the following protective measures:
Organizations should also develop and test incident response plans specifically addressing ransomware scenarios. As noted in our comprehensive malware removal guide, having established protocols in place before an attack occurs reduces recovery time and potential damage.
Krypt ransomware shares similarities with several other ransomware families, particularly Proton Ransomware, while also exhibiting unique characteristics:
Multi-Channel Communication: Like Proton, Krypt provides multiple ways for victims to contact the attackers, including TOR-based chat interfaces and email addresses. This approach maximizes the chances of victims establishing communication.
Professional Interface: Both Krypt and Proton feature polished, professional-looking communication interfaces that mimic legitimate business applications. This level of presentation helps build “trust” with victims.
Double Extortion: Both ransomware families employ the increasingly common tactic of combining encryption with data theft threats to increase pressure on victims to pay.
Targeted Defense Evasion: Similar to Proton, Krypt actively disables specific security features like Windows Defender and System Restore to prevent detection and recovery.
UPX Packing: Like many ransomware families including Maximsru Ransomware, Krypt uses UPX packing to obfuscate code and evade detection.
Visual Notifications: The desktop wallpaper change is a common tactic also seen in ransomware like Jeffery Ransomware, creating immediate psychological impact on victims.
Distribution Methods: Similar to LockBit 4.0, Krypt appears to use a combination of phishing, exposed RDP, and compromised credentials as primary infection vectors.
Telegram Contact Option: While many ransomware operations offer email and TOR communication, the explicit Telegram contact option is less common and potentially provides a more responsive communication channel.
Warnings Against Recovery Companies: Krypt’s ransom note specifically warns against using third-party recovery companies, even suggesting that victims can observe these companies negotiating with the attackers through the chat links.
Geographic Awareness: The presence of location checking in the code suggests Krypt may be calibrating its targeting based on geographic regions, either to avoid certain countries or to adjust ransom demands based on location.
Krypt represents the evolution of ransomware toward more professional, service-oriented operations. The communication interfaces, multiple contact channels, and stated guarantees (offering to decrypt a small file as proof) reflect the trend of ransomware operators attempting to establish themselves as “reliable business partners” despite their criminal activities.
The similarities to Proton Ransomware suggest that Krypt may either be:
This evolution shows the professionalization of the ransomware ecosystem, with operators adopting business practices alongside technical advancements.
Krypt ransomware is a threat in the current cybersecurity landscape, combining encryption capabilities with double extortion tactics and multi-channel communication strategies. Its approach to victim communication and presentation indicate a well-organized operation rather than an amateur effort.
Key characteristics that define Krypt include:
Organizations and individuals can protect themselves by implementing security measures with emphasis on email security, secure remote access, regular system updates, controlled user privileges, and offline backup strategies. The multi-faceted nature of modern ransomware threats like Krypt necessitates a defense-in-depth approach rather than relying on any single security control.
As ransomware continues to evolve in both technical capabilities and business models, maintaining a proactive security posture and preparing for potential incidents becomes important. By combining technical controls with user education, proper backup procedures, and incident response planning, organizations can reduce both the likelihood and impact of ransomware attacks like Krypt.