
DNSpionage 운영을 담당하는 사이버 범죄자 그룹은 피해자를 선택하는 데있어 더욱 선택적이되었으며 사이버 공격의 효과를 높이기 위해 새로운 악성 코드 Karkoff로 무장했습니다..
에이cFireEye에 따름, 4 월 말 DNSpionage 캠핑 시작 2017 이란 정부의 이익을 위해 행동하는 책임있는 사이버 범죄자.이전 공격에서, 가짜 웹 사이트 및 DNS 브레이크 사용, 침입자가 합법적 인 도메인의 트래픽을 악성 코드 도메인으로 리디렉션, 후자는 무료 디지털 인증서를 사용했습니다. 암호화하자.
이제 C와의 연결을 지원하는 원격 관리 용 새 도구로 무장 한 그룹&HTTP 및 DNS를 통한 C 서버, 연구원 시스코 탈로스.
Cisco Talos의 출시 이후 DNSpionage에 대한 첫 번째 보고서 2018, 사이버 범죄자들은 그들의 전술을 강화했습니다.
“배우에 대한 몇 가지 변화를 발견했습니다.’ 전술, 기술 및 절차 (TTPs), 멀웨어로 감염시킬 대상을 선택적으로 선택하는 새로운 정찰 단계의 사용을 포함합니다. ", – Cisco Talos 연구원들은.
스파이 방법의 도움으로, 범죄자는 보호를 우회하고 공격하는 시스템의 디지털 지문을 생성합니다..
범죄자들은 희생자를 매우 신중하게 선택하고 표적 낚시를 사용하여 공격합니다.. 악성 코드 매크로가 포함 된 Microsoft Word 및 Excel 문서를 첨부하여 피해자에게 이메일을 보냅니다.. 공격 중, 매크로를 통해 악성 프로그램은«taskwin32.exe»계획된 작업 생성«onedrive 업데이터 v10.12.5»멀웨어가 시스템에서 지속되도록하기 위해.
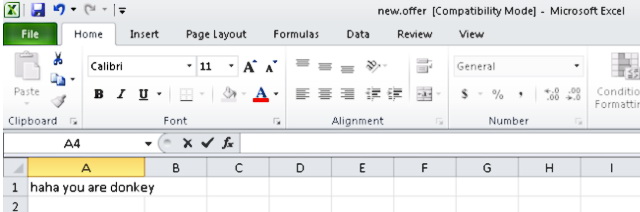
DNS 스파이 활동, Excel 문서를 열 때, 사용자는 모욕으로 맞이합니다., “하하 넌 당나귀 야 [sic].” 깨진 영어는 배우가 영어 원어민이 아닐 가능성이 있음을 나타냅니다..
이번 달 연구원들은 .Net의 그룹 멀웨어 프로그램에서 이름으로 처음 발견되었습니다. 카르코프. 그들은 악성 코드가 "경량화"되어 있으며 C를 통한 원격 수행이 필요하다고 말합니다.&C 서버.
그렇지만, Karkoff는 한 가지 흥미로운 기능을 가지고 있습니다.. 맬웨어는 수행 된 모든 명령을 시간 표시와 함께 저장하는 저널 파일을 생성합니다.. 그래서, 이 저널을 사용하여 Karkoff 피해자는 특정 사건이 언제 어떻게 발생했는지 확인할 수 있습니다..
