
Europol reported about success of cross-border operation on cessation of cybercriminal group activity that is responsible for creation and spread of bank Trojan malware GozNym.
As assessed, operators tried to steal with its help more than $100 million from 41 thousand of victims of infection, the bulk of which were legal entities.Criminals worked by the scheme “cybercrime as a service”: for a fee previded access to banker’s copies and created a series of services for convenience of their usage. Criminal group had own programmers, specialists in code obfuscation and spam sending, and also with a vast network of drops: clients receive technical service support.
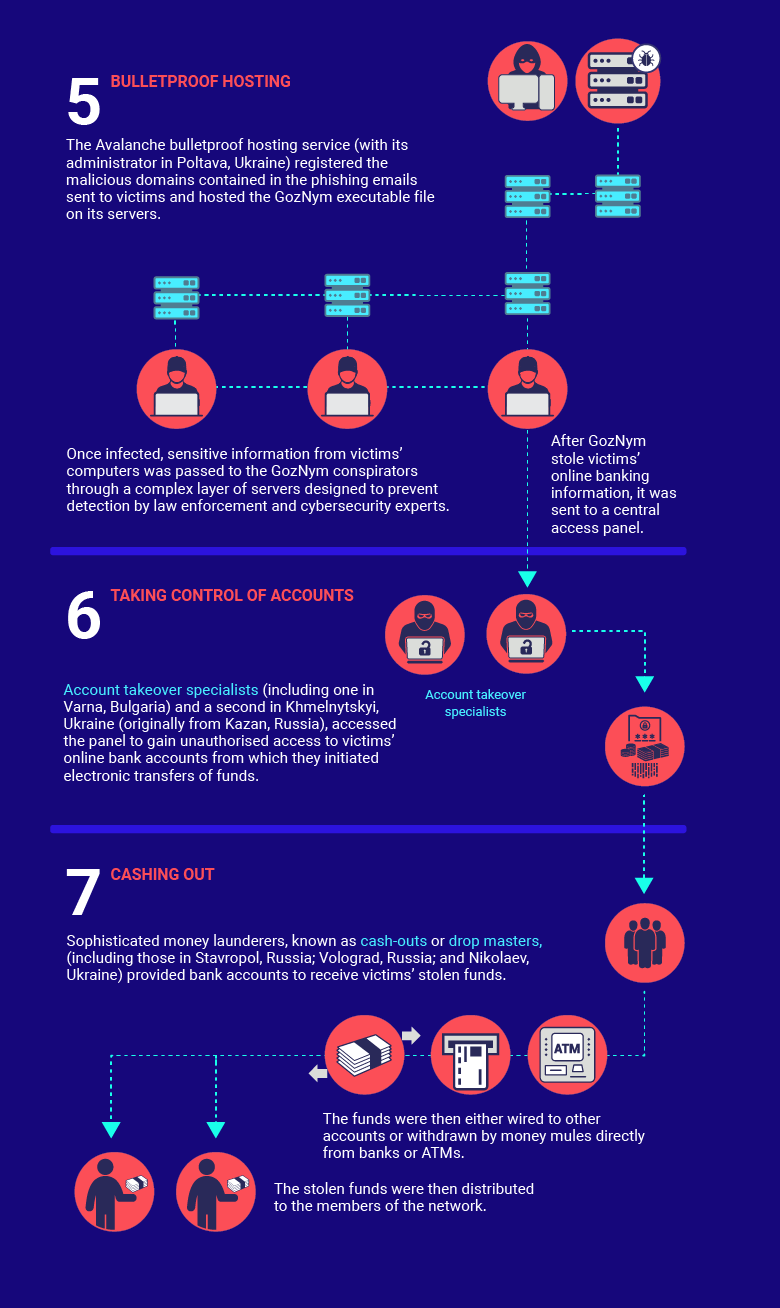
Servers for GozNym files accommodation and storage of stolen data criminals rented from another criminal group named Avalanche. Through them was performed domains’ registration that later arrived in spam-campaigns.
According to Europol, except for GozNym owners, Avalanche service used more than 200 cybercriminals that appreciated its “bulletproof” hosting. At the end of 2016 cooperated efforts of dozens of countries service was closed, and against its administrators was initiated a criminal case in Ukraine.
In GozNym liquidation participated law enforcement organizations of Bulgaria, Germany, Moldova and Ukraine, and FBI. Active support to the operation provided Europol and Eurojust.
“This operation showcases how an international effort to share evidence and initiate criminal prosecutions can lead to successful operations in multiple countries”, — argued in Europol.
A criminal Indictment returned by a federal grand jury in Pittsburgh, USA charges ten members of the GozNym criminal network with conspiracy to commit the following:
- infecting victims’ computers with GozNym malware designed to capture victims’ online banking login credentials;
- using the captured login credentials to fraudulently gain unauthorised access to victims’ online bank accounts;
- stealing money from victims’ bank accounts and laundering those funds using U.S. and foreign beneficiary bank accounts controlled by the defendants.
Five more suspects, including GozNym main developer, live in Russia and are not available for American justice.
“The GozNym network was formed when these individuals were recruited from the online forums by the GozNym leader who controlled more than 41 000 victim computers infected with GozNym malware”, — report Europol.
Bulgarian citizen Krasimir Nikolov that specialized on banks accounts hacking with the use of stolen credentials and withdrawn of funds from accounts, was arrested in his home country and extradited to US where he confessed in crimes. He will be sentenced on August 30.
Head of the cyberband Alexander Kononov and his first assistant Marat Kazandzhyan will be judged by place of residence in Tbilisi. Eduard Malanich that provided cryptor for GozNym, called to account in Moldova and also cannot appear before a US court now.
List of respondents in the United States also includes a 45-year-old resident of Ukraine, Alexander Van Hoof, who owns a set of bank accounts to which were transferred stolen money.
Source: https://www.europol.europa.eu
