
IGBlade is a marketing and business tool for in-depth analytics of social media platforms. It exposed over 2.6 million records of social user accounts. It sums up to approximately 3.6+GB of leaked data. Specialists from Safety Detectives with researcher Anurag Sen at the head came upon the vulnerable ElasticSearch server.
IGBlade server leak: over 2.6 million accounts exposed
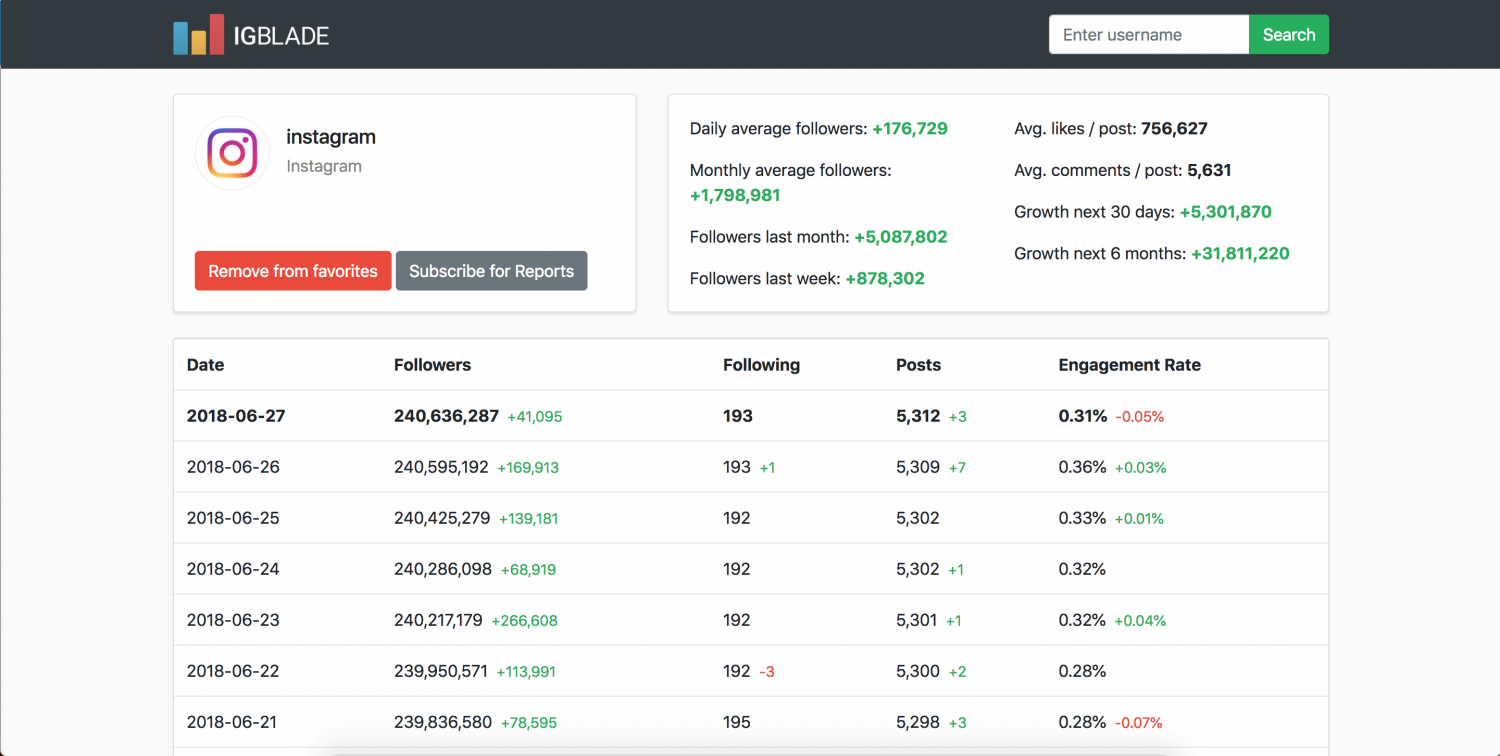
IGBlade’s Instagram and TikTok analytics tool presents data from millions of social media. It accounts for almost 30 data metrics. This platform presents the information in practically applicable results like engagement rate, account history and follower growth. You must have an account there to see detailed data. It includes demographics stats (visitors by country, for example), account reports and data visualizations. IGBlade’s ElasticSearch server was publicly exposed without any encryption in place. Such data storing goes against GDPR rules, however, nobody took care of it earlier.
Which data is exposed?
The server was online and got updates at the time when specialists came across it. The size of the breach indicates more than 2 million social media users could be affected. Those affected include famous influencers, like celebrities, social media influencers and food bloggers. Among them, big verified celebrity accounts, such as Ariana Grande, Kim Kardashian, Kylie Jenner. The big luck is that this data was not reached by cybercriminals, like in the case of Acer Corporation. Tech giant suffered two attacks per last week, and hackers explain it… with the same “poor data protection mechanisms”1.
Precisely, IGBlade’s server contained separate types of personal data of social account users:
A full breakdown of the location scale and size of the IGBlade data breach presents below.
Data scraping is legal data collection
Simply to say, the only method IGBlade works is through scraping the data. On most social platforms such actions fall under the ban. For example, Instagram’s terms of service state: “You must not crawl, scrape, or otherwise cache any content from Instagram including but not limited to user profiles and photos.” But according to the general rule data scraping of the information that is public does not correspond to illegal actions. And data scrapers do not face legal sanctions, which are supposed for going against the data protection rules.
If you have concerns over your safety though stick to the simple rules. Check your privacy settings on social media. Limit the information you post to your account. And block/delete unknown users.Screen new follower/friend requests.Social media data scraping do not usually considered a typical data exposure. In most cases it is unavoidable.2
- About the first attack on Acer Corporation.
- Report about this data breach from the researchers – Safety Detectives.
