Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine
Physical Address
Lesya Kurbasa 7B
03194 Kyiv, Kyivska obl, Ukraine

Cybersecurity researchers have identified a sophisticated new scam campaign that combines social engineering with technical exploits. Dubbed “FakeCaptcha,” this attack leverages URL manipulation tactics to trick users into running malicious code by exploiting the userinfo portion of web addresses and legitimate domain names to establish false credibility.
According to security analysts, the scam has been actively targeting users since early March 2025, primarily focusing on individuals seeking to verify they are “not a robot” through what appears to be familiar CAPTCHA systems:
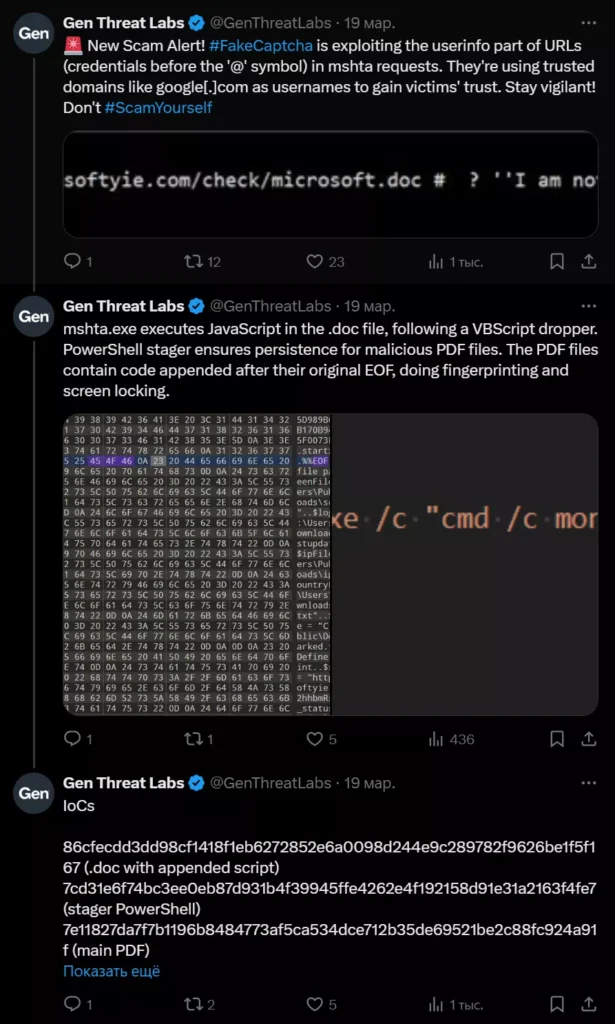
The attack chain begins with a deceptive URL that includes a trusted domain like “google.com” placed in the userinfo section of the address (before the ‘@’ symbol), making the link appear legitimate at first glance. For example, a URL might appear as:
https[:]//google.com@help.macosoftyie[.]com/check/microsoft.doc
While many users might assume this leads to Google, the URL actually directs to “macosoftyie.com” — the attacker’s domain. This manipulated URL serves as the initial entry point for the attack sequence, which unfolds in several stages:
What makes this attack particularly concerning is that the malicious PDF files contain code appended after their original EOF (End of File) marker. This technique allows the attackers to bypass certain security measures while performing system fingerprinting and potentially locking the user’s screen to demand payment or further interaction.
Source: Analysis of FakeCaptcha attack method by Trojan Killer Security Research Team, March 2025
Security researchers have identified several indicators of compromise (IoCs) associated with this campaign:
These malicious elements bear similarities to techniques observed in previous Emotet campaigns, where attackers use multiple stages to establish persistence and deploy additional payloads. The screen locking component also resembles techniques employed by ransomware operators, suggesting possible connections to more sophisticated threat actors.
This attack can have several serious consequences for victims:
Organizations with compromised systems may face operational disruptions, data breaches, financial losses, and reputational damage. Individual users risk identity theft, financial fraud, and loss of personal data.
To protect against this and similar threats, security experts recommend implementing the following measures:
Organizations should also consider implementing DMARC, SPF, and DKIM email authentication protocols to reduce the risk of spoofed emails reaching their users.
The techniques employed in the FakeCaptcha campaign have been observed in other malware operations, including Zeus variants and Altruistic Trojan. The multi-stage approach with document-based initial infection, followed by PowerShell persistence and payload retrieval, is becoming increasingly common among sophisticated threat actors.
This attack also demonstrates similarities to URL manipulation techniques seen in phishing campaigns like the Chase Transfer phishing scam, where attackers create convincing replicas of legitimate services to harvest credentials and deploy malware.
By combining several effective tactics — URL manipulation, trusted domain impersonation, multi-stage execution, and PDF exploitation — this campaign represents an evolution in attack sophistication that requires enhanced vigilance from both users and security professionals.
The FakeCaptcha scam demonstrates the continuing evolution of cyber threats that blend social engineering with technical exploitation. By understanding how these attacks work and implementing appropriate countermeasures, organizations and individuals can reduce their risk of compromise.
As this threat continues to develop, security researchers will monitor for new variants and techniques. Staying informed about emerging threats remains one of the most effective ways to maintain strong cybersecurity posture in today’s rapidly evolving threat landscape.