
Los expertos en seguridad han hablado mucho sobre la reducción de la actividad de explotación de los kits, muchos de ellos todavía permanecen “en servicio”, seguir para mejorar y cambiar la carga útil.
lane of these long-known players’ los investigadores es el RIG explotar kit.Recientemente, expertos notaron que RIG comenzó a distribuir Eris encrypter, por primera vez en de mayo de 2019. investigador Michael Gillespie was first to discovere an extortionist, when the malware appeared on the ID Ransomware.
Now an independent information security specialist, known under the pseudonym nao_sec, noticed that the new campaign of RIG uses Eris as the payload.
“A malvertising campaign using the popcash ad network is redirecting users to the RIG exploit kit. The kit will attempt to exploit a Shockwave (SWF) vulnerability in the browser. If successful, it will automatically download and install the ERIS Ransomware on to the computer”, — reported nao_sec.
The extortionist encrypts files of his victims, changing their extensions to .ERIS.
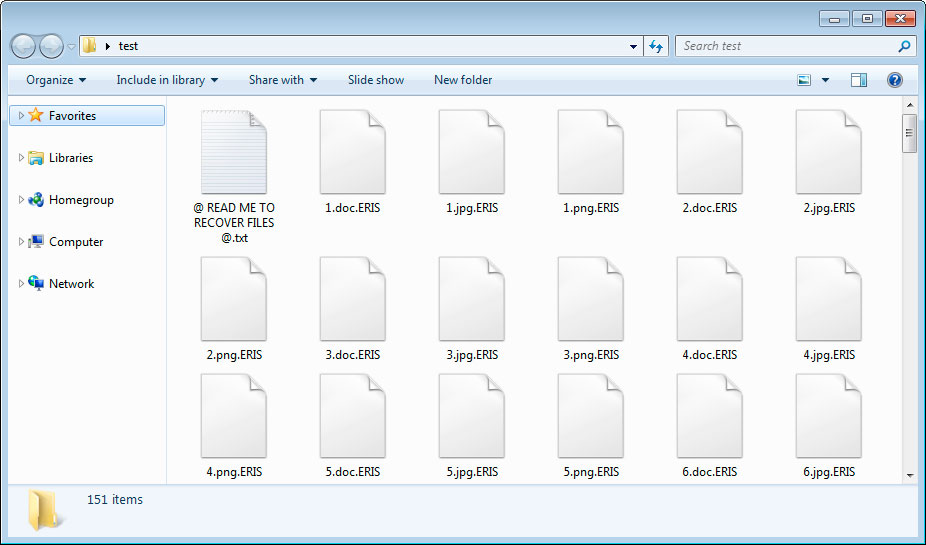
In each folder that was scanned, the extortionist also creates a redemption note with the name @ READ ME TO RECOVER FILES @ .txt, which instructs the victim to contact Limaooo@cock.li for payment instructions. A unique identifier is included in this ransom note, which the victim must send to the ransomware developer so that he can perform a free test transcript of a single file.
los investigadores señalan que, Desafortunadamente, there is no way to decrypt the files affected by Eris, without paying the ransom to the attackers.
