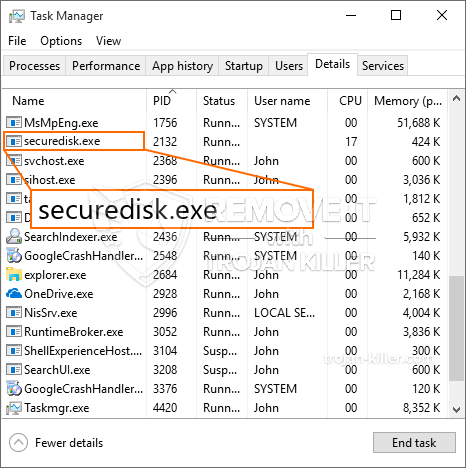
Un completamente nuevo, extremadamente peligrosa infección criptomoneda minero en realidad ha sido descubierto por los investigadores de seguridad y protección. el software malicioso, llamado Securedisk.exe pueden contaminar las víctimas de destino que utilizan una variedad de medios. La esencia detrás de la minera es Securedisk.exe a las actividades minero empleo criptomoneda en los equipos de los enfermos con el fin de adquirir fichas de Moneo en el gasto enfermos. The result of this miner is the raised electricity costs and also if you leave it for longer amount of times Securedisk.exe may even damage your computer systems parts.
Securedisk.exe: Métodos de distribución de
los Securedisk.exe malware utilizes two prominent approaches which are utilized to contaminate computer system targets:
- Entrega de carga útil a través de infecciones previas. If an older Securedisk.exe malware is released on the sufferer systems it can automatically update itself or download a more recent variation. Esto es factible a través del comando de actualización incorporado que obtiene el lanzamiento. Esto se hace mediante la unión a un servidor web predefinido pirata informático controlado específica que ofrece el código de malware. La infección descargado e instalar sin duda adquirir el nombre de una solución de Windows y puede poner en el “%sistema% temp” zona. Essential buildings as well as operating system configuration files are altered in order to allow a persistent as well as quiet infection.
- El aprovechamiento de vulnerabilidades de software Programa. The latest version of the Securedisk.exe malware have actually been found to be triggered by the some ventures, entendido popularmente para ser utilizado en los ataques ransomware. Las infecciones se llevan a cabo por la orientación soluciones abiertas a través del puerto TCP. Los asaltos son automatizados por un marco Hacker-controlada que mira hacia arriba si el puerto está abierto. If this condition is fulfilled it will certainly check the solution and get information about it, que consiste en cualquier tipo de variación y también datos de disposición. Empresas y también nombre de usuario prominente, así como combinaciones de contraseñas se pueden hacer. When the make use of is triggered versus the at risk code the miner will be deployed along with the backdoor. Esto sin duda ofrecer la doble infección.
Apart from these techniques various other approaches can be used too. Miners can be distributed by phishing emails that are sent in bulk in a SPAM-like way as well as depend on social engineering methods in order to perplex the sufferers into believing that they have received a message from a genuine solution or firm. The virus documents can be either directly connected or placed in the body materials in multimedia material or message links.
The crooks can likewise produce harmful touchdown web pages that can impersonate vendor download pages, software download sites and also various other frequently accessed places. When they make use of comparable sounding domain names to legitimate addresses and also safety certifications the users may be coerced right into engaging with them. En muchos casos simplemente abrirlos puede desencadenar la infección minero.
Another strategy would certainly be to make use of haul service providers that can be spread out making use of those methods or by means of documents sharing networks, BitTorrent es sólo una de una de las más preferidas. It is often utilized to distribute both reputable software application and also documents and pirate web content. 2 de uno de los portadores de carga útil más preferidos son los siguientes:
Various other approaches that can be taken into consideration by the bad guys include the use of browser hijackers -harmful plugins which are made compatible with one of the most preferred internet browsers. They are published to the appropriate repositories with phony user evaluations and also designer credentials. Muchas veces los descripciones pueden incluir capturas de pantalla, videos and elaborate summaries encouraging wonderful function improvements and efficiency optimizations. Nonetheless upon setup the behavior of the affected web browsers will certainly alter- individuals will find that they will be rerouted to a hacker-controlled landing web page and also their setups may be changed – la página web por defecto, motor de búsqueda en Internet y también la página web de pestañas nuevo.

Securedisk.exe: Análisis
The Securedisk.exe malware is a traditional situation of a cryptocurrency miner which depending on its setup can trigger a variety of hazardous activities. Su principal objetivo es llevar a cabo las tareas matemáticas complejas que sin duda beneficiarán de las fuentes del sistema fácilmente disponibles: UPC, GPU, la memoria y el área del disco duro. La forma de operar es mediante la unión a un servidor llamado bloque especial de minería web desde donde el código necesario se descarga e instala. Tan rápidamente como una de las tareas que se descarga se iniciará simultáneamente, numerosos casos se pueden realizar en cuando. Cuando se termina una tarea ofreció una adicional se descargará en su lugar y también continuará la laguna hasta que el ordenador esté apagado, la infección se elimina u otra ocasión similar sucede. Criptomoneda ciertamente será compensado a los controladores criminales (grupo de hackers o un solo usuario remoto) directamente a sus bolsillos.
Una característica nociva de esta categoría de malware es que ejemplos como éste puede tomar todas las fuentes del sistema, así como casi hacer que el equipo sufre inutilizable hasta que el riesgo ha sido efectivamente eliminado por completo. La mayoría de ellos incluyen una instalación implacable que les hace muy difícil deshacerse de. Estos comandos sin duda hará ajustes a las alternativas de arranque, arrangement data as well as Windows Registry values that will make the Securedisk.exe malware beginning immediately as soon as the computer is powered on. El acceso a los menús de curación, así como las alternativas pueden ser bloqueados que hace muchos Guías Prácticas prácticamente sin valor eliminación.
Esta infección específica será sin duda disposición un servicio de Windows por sí mismo, cumpliendo con el llevado a cabo allí la seguridad y la evaluación de seguridad cumpliendo con las acciones se han observado:
Durante las operaciones minero el malware relacionado se puede unir a la ejecución de los servicios actualmente en Windows y las aplicaciones de terceros también instalados. Al hacerlo los administradores del sistema pueden no notar que los lotes de origen proviene de un proceso diferente.
| Nombre | Securedisk.exe |
|---|---|
| Categoría | Trojan |
| Subcategoría | criptomoneda Miner |
| peligros | alto uso de CPU, reducción de la velocidad de Internet, PC se bloquea y se congela y etc.. |
| Propósito principal | Para ganar dinero para los criminales cibernéticos |
| Distribución | torrentes, Juegos gratuitos, Aplicaciones Cracked, Email, los sitios web cuestionables, exploits |
| Eliminación | Instalar GridinSoft Anti-Malware to detect and remove Securedisk.exe |

These type of malware infections are particularly efficient at performing advanced commands if set up so. They are based upon a modular framework enabling the criminal controllers to orchestrate all kinds of unsafe habits. Uno de los ejemplos populares es el ajuste del registro de Windows – adjustments strings connected by the operating system can trigger severe efficiency disruptions as well as the inability to accessibility Windows solutions. Basándose en la serie de modificaciones que asimismo puede hacer que el equipo del todo inútil. On the various other hand adjustment of Registry worths coming from any type of third-party installed applications can sabotage them. Algunas aplicaciones pueden dejar de funcionar para introducirse por completo, mientras que otras pueden dejar de funcionar repentinamente..
This certain miner in its existing version is concentrated on mining the Monero cryptocurrency having a changed variation of XMRig CPU mining engine. If the campaigns verify effective after that future variations of the Securedisk.exe can be introduced in the future. A medida que el malware utiliza vulnerabilidades de las aplicaciones de software para infectar a los hosts de destino, que puede ser parte de una coinfección con ransomware perjudiciales y troyanos.
Removal of Securedisk.exe is highly recommended, since you take the chance of not just a huge electrical power expense if it is operating on your PC, however the miner might additionally do various other undesirable tasks on it as well as even harm your COMPUTER permanently.
Securedisk.exe removal process
PASO 1. Ante todo, es necesario descargar e instalar GridinSoft Anti-Malware.
PASO 2. Entonces usted debe elegir “Análisis rápido” o “Análisis completo”.
PASO 3. Corre a escanear su ordenador
PASO 4. Después de terminar el análisis, es necesario hacer clic en “Aplicar” button to remove Securedisk.exe
PASO 5. Securedisk.exe Removed!
Guía de vídeo: How to use GridinSoft Anti-Malware for remove Securedisk.exe
Cómo evitar que su PC de reinfección con “Securedisk.exe” en el futuro.
Una potente solución antivirus capaz de detectar el malware y el bloque sin archivo es lo que necesita! Las soluciones tradicionales de detectar malware basado en las definiciones de virus, y por lo tanto a menudo no pueden detectar “Securedisk.exe”. GridinSoft Anti-Malware ofrece protección contra todo tipo de malware incluyendo malware sin archivo como “Securedisk.exe”. GridinSoft Anti-Malware ofrece analizador de comportamiento basado en la nube para bloquear todos los archivos desconocidos, incluyendo malware de día cero. Dicha tecnología puede detectar y eliminar por completo “Securedisk.exe”.







