
especialistas Cybereason estudiaron el malware Phoenix, que llegó este verano y presenta un híbrido de un keylogger y un Infostealer. Los investigadores han encontrado que Phoenix puede desactivar más de 80 productos de seguridad.
Tque el malware se propaga según la malla modelo (“Malware como un servicio”) y ya es responsable de 10,000 infecciones.Desde Phoenix se vende como un producto de suscripción, los precios van desde $14.99 un mes a $78.99 para una suscripción de por vida. Cybereason analistas escriben que Phoenix es un desarrollo de un autor experimentado el malware. Aparentemente, el autor del malware Alfa Keylogger, quien murió a principios de este año, fue originalmente detrás de su creación.
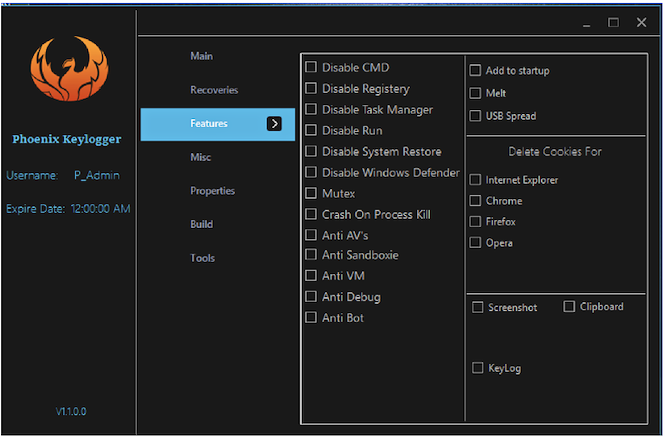
“Phoenix es algo más que un keylogger, que tiene amplias capacidades de información de robo y mecanismos de autodefensa, que incluyen un módulo de anti-AV que los intentos para hacer una parada 80 productos de seguridad, y la capacidad de exfiltrate datos a través de telegrama”, - escribir especialistas Cybereason.
En efecto, en los últimos meses, Phoenix ha evolucionado desde un simple keylogger en un troyano multifuncional diseñado para robar información (Infostealer). Si en la primera versión fue proporcionada la versión maliciosa sólo por la capacidad de pulsaciones de teclas de intercepción, a continuación, las nuevas versiones del programa malicioso roban las contraseñas de casi veinte diferentes navegadores, cuatro clientes de correo electrónico, clientes FTP y mensajería instantánea. Adicionalmente, el programa malicioso puede robar datos desde el portapapeles, tomar capturas de pantalla y descargar malware adicional.
Información robada de las víctimas se transmite a los operadores de malware a través de SMTP, FTP o Telegrama.
leer también: Los criminales dan enlaces a troyanos RAT en WebEx invitaciones
Phoenix también adquirió módulos agresivos contra anti-virus y las máquinas virtuales que tratan de evitar la detección y análisis de malware. Ambos módulos funcionan de la misma manera: tratan de cerrar una serie de procesos antes de que el malware se sigue trabajando, para esto, en referencia a una lista predefinida de nombres. Esta lista incluye los nombres de más de 80 productos de seguridad y máquinas virtuales conocida, que se utilizan a menudo para la ingeniería inversa y el análisis de malware.
Los analistas dicen que Phoenix podría utilizar sus capacidades para lograr una presencia permanente en el sistema, pero sus operadores tienen poco interés en ella. Según los investigadores, con más frecuencia el malware se utiliza como una solución única para el robo de datos y no se utiliza para el seguimiento a largo plazo de las víctimas. Unos segundos después de la infección, Phoenix roba todos los datos confidenciales necesarios, y en esta función sus acabados. Los criminales más a menudo información de la venta robados de esta manera en la red oscura.
