
Microsoft publicó detalles de los ataques administrados por Windows a computadoras en compañías de medios que tuvieron lugar en marzo.
yon the attacks, Los delincuentes utilizaron la famosa vulnerabilidad WinRAR que ganó popularidad dentro de los grupos criminales en los últimos meses.. Los piratas informáticos se armaron con él inmediatamente después de la publicación por parte de la empresa Check Point., en febrero 20. That time researchers demonstrated how through this vulnerability code with the help of a file with special configuration (compressed files format) may be applied random code.New improved WinRAR version was issued month before Check Point publication, but even in March Microsoft still watched attacks with CVE-2018-20250.
In the March campaign, hackers sent fishing letters allegedly from Afghanistan Home Office. Methods of social engineering that they applied were carefully planned to ensure full remote system discredit in the frameworks of WinRAR limited vulnerability.
Fishing letters contained Microsoft Word file with the link on other OneDrive document. It did not contain any malware macro to prevent attack detection. sin embargo, OneDrive document contained malware macro and after their activation victim’s system received new hacker’s software.
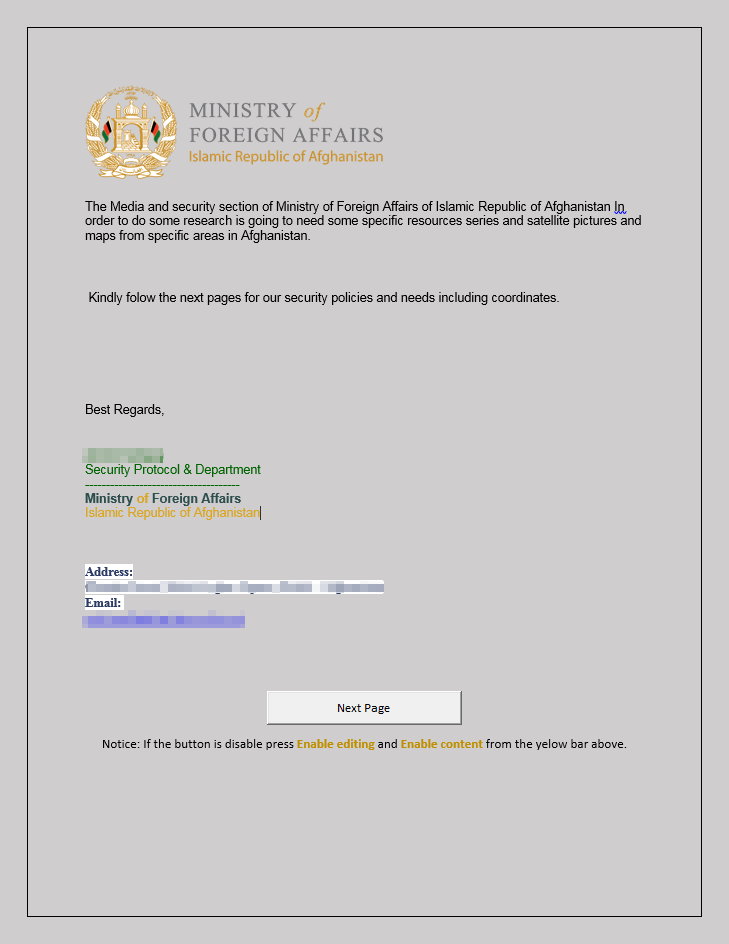
Downloaded document with malicious macro
Document also contained “Next page” button that contained fake notification about absence of necessary file DLD and necessity of computer restart. This trick was necessary as vulnerability enables malware programs to download files in a certain folder but not to start them at once. Considering this, ideal solution was putting program in the “Startup” folder. Files from this folder started at once after restarting computer.
After restart in the infected system started backdoor PowerShell that opens hackers full access to it. Use of this backdoor and other features pointed that cyber-band MuddyWater is responsible for the attacks.
“This PowerShell script is similar to a script that has been used in past MuddyWater campaigns”, – confirmed Microsoft experts.
