
Los expertos de la compañía china KnownSec 404 que desarrolló el motor ZoomEye IO-búsqueda, descubierto peligrosa vulnerabilidad en Oracle WebLogic.
UNAde acuerdo a para hacer un zoom, en Internet se pueden encontrar más de 36 000 Servidores WebLogic disponibles que son vulnerables detrás del nuevo problema. La mayoría de ellos se encuentran en Estados Unidos y China.Los investigadores explican,ese error es peligroso para todos los servidores Oracle WebLogic con componentes en ejecución WLS9_ASYNC y WLS-WSAT. El primer componente es necesario para operaciones asincrónicas, mientras que el segundo es una solución protectora.. Como todavía no hay correcciones disponibles, los expertos no divulgan detalles técnicos, pero escriben que la vulnerabilidad está relacionada con la deserialización y permite que el pirata informático remoto ejecute cualquier comando sin autorización (con el uso de una solicitud HTTP especial).
Como medida preventiva se recomienda eliminar completamente los componentes problemáticos eliminándolos y reiniciando el servidor WebLogic, o cree reglas que prohíban las solicitudes a / _async / * y / wls-wsat / *.
Los expertos en seguridad de Internet de otras compañías confirman, esa vulnerabilidad está realmente bajo ataques (los hackers ya lo saben) aunque los piratas informáticos solo investigan porque sus ataques se limitan a escanear en partes vulnerables de los servidores de WebLogic y probar los intentos de explotar el error. Los intrusos no intentan colocar malware en sus servidores o usarlo para otras operaciones maliciosas.
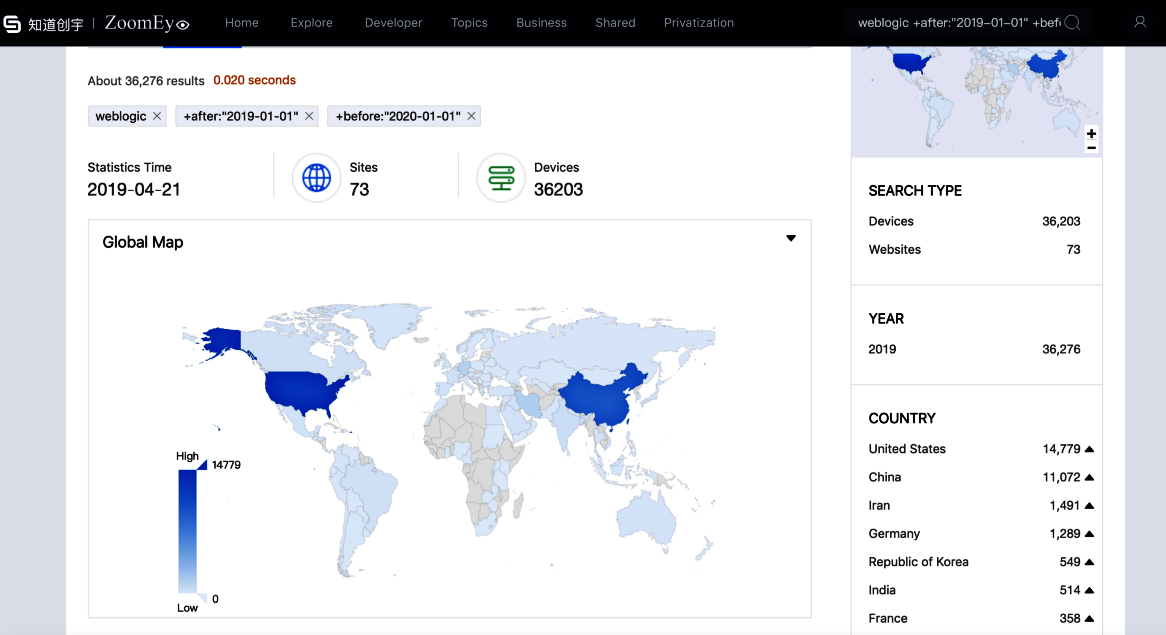
36 000 Servidores WebLogic disponibles que son vulnerables detrás del nuevo problema, De acuerdo con ZoomEye.
Desafortunadamente, esta situación no durará mucho tiempo, tan potentes y extremadamente populares en el entorno empresarial Los servidores Oracle WebLogic han sido una oración deseable por los intrusos durante mucho tiempo. Por ejemplo, en diciembre 2018 se corrigieron los casos en que la minería oculta en servidores Oracle WebLogic enriquecía a los tramposos de Internet por más de $226 000.
Aunque los productores han informado a los clientes sobre la vulnerabilidad, Oracle lanzó su conjunto de parches trimestrales solo la semana pasada, Asi que, parche para un nuevo error con llegada solo en varios meses.
Para cuando se emitió esta alerta, el oficial todavía no lanzó la corrección correspondiente, que es una vulnerabilidad de "0 días". Un atacante podría aprovechar esta vulnerabilidad para ejecutar comandos de forma remota sin autorización, - informó KnownSec 404 especialistas.
Identificador de error recibido CNVD-C-2019-48814.
