
especialistas de ESET descubiertos en el arsenal Turla nuevo instrumento poderoso que los hackers lograron ocultarse durante cinco años, al menos desde 2014.
segundoackdoor llamado Neurona de luz compromete los servidores de correo de Microsoft y funciona como agente de transferencia de correo, (MTA) que no es típico de este tipo de malware.Los investigadores señalan, ese, según sus datos, LightNeuron es un backdoor fisrt que está especialmente orientado en Microsoft Exchange. Turla aplicó anteriormente el malware Neuron (también conocido como DarkNeuron), que no tiene nada similar con LightNeuron y fue desarrollado con el foco en Microsoft Exchange.
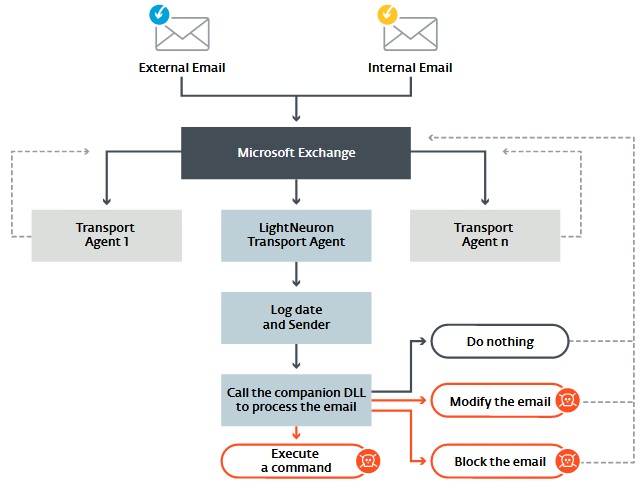
LightNeuron no solo permite a los atacantes rastrear eventos en el servidor de correo, pero para integrar en su trabajo y controlar prácticamente cualquier cosa.
"En la arquitectura del servidor de correo, La puerta trasera puede funcionar con el mismo nivel de confianza., como productos de seguridad, como filtros de spam. Por consiguiente, este malware da a los ciberdelincuentes un control total sobre el servidor de correo, y, Por esto, en todas las letras ", – explicar a los especialistas de ESET.
Los piratas informáticos pueden interceptar y redirigir todos los correos, editar el contenido de los mensajes enviados y de la bandeja de entrada o bloquear la recepción de algunos correos para los usuarios. Todas estas oportunidades hacen de LigthNeuron una de las herramientas más poderosas del arsenal del grupo..
Adicionalmente, puerta trasera difiere en que utiliza un peculiar do&Mecanismo C. El caso es que los atacantes nunca conectaron los servidores de Microsoft directamente.
En lugar, usan esteganografía y mails con archivos PDF y JPG adjuntos. Dentro de estas letras, los piratas informáticos del equipo de LightNeuron ocultan los comandos para LightnNeuron que el malware abre y ejecuta. Esta forma de comunicación con malware complica significativamente su detección, ya que los comandos para la puerta trasera pueden venir con spam común al que nadie presta atención y no rastrea, ya que los filtros lo eliminan.

Como se informó, LightNeuron se usa para ataques hasta ahora. Los expertos de ESET ya han identificado tres organizaciones que lo padecieron. Los analistas no revelan sus nombres, pero informa que son algunas de las estructuras brasileñas, Ministerio de Asuntos Exteriores de Europa del Este y una organización diplomática regional sobre Oriente Medio.
Fuente: https://www.welivesecurity.com
