
ESET specialists discovered in the Turla arsenal new powerful instrument that hackers managed to hide for five years, at least since 2014.
Backdoor named LightNeuron compromises Microsoft mailing servers and functions as mail transfer agent, (MTA) that is not typical for such malware.Researchers note, that, according to their data, LightNeuron is a fisrt backdoor that is specially orientated on Microsoft Exchange. Earlier Turla applied Neuron malware (aka DarkNeuron), that has nothing similar with LightNeuron and was developed with the focus on Microsoft Exchange.
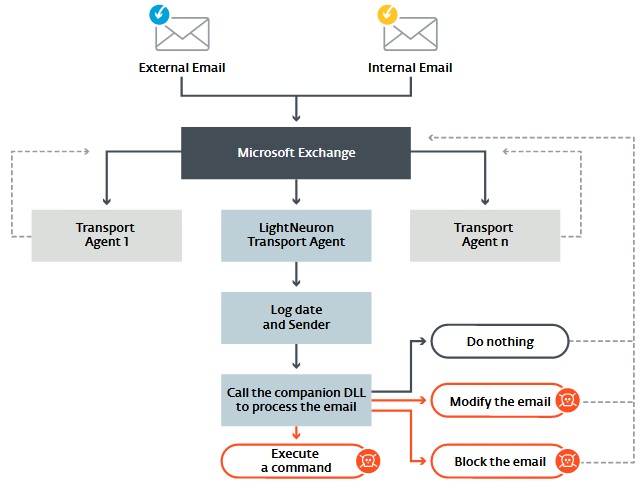
LightNeuron not just allows attackers to trace events on mailing server, but to integrate in its work and control virtually anything.
“In architecture of mailing server, backdoor can work on same level of trust, as security products, as spam filters. Consequently, this malware gives cybercriminals full control over mailing server, and, by this, on all letters”, – explain ESET specialists.
Hackers can intercept and redirect all mails, edit content of sent and inbox messages or block receiving some mails for users. All these opportunities make LigthNeuron one of the most powerful tools in group’s arsenal.
In addition, backdoor differs as it uses one peculiar C&C mechanism. The case is that attackers never connected Microsoft servers directly.
Instead, they use steganography and mails with attached PDF and JPG files. Inside these letters hackers from LightNeuron team hide commands for LightnNeuron that malware opens and performs. This way of communication with malware significantly complicates its detection, as commands for backdoor might come with ordinary spam that no one pays attention to and does not trace as filters weed it out.

As reported, LightNeuron is used for attacks until now. ESET experts have already identified three organizations that suffered from it. Analysts not disclose their names, but report that it is some of the Brazilian structures, Ministry of Foreign Affair from Easter Europe and one regional diplomatic organization on the Middle East.
Source: https://www.welivesecurity.com
