
Attention to everyone! Some good news arrived. Every user who has fallen victim to Diavol ransomware now can get their files recovered with a free decryption tool.
How to use the free decryption tool?
Before using the tool consider the next. It’s important for the successful usage of the decryption solution. Make sure to quarantine the malware so it won’t come back when you’re done with recovering your files.
Also cybersecurity experts advise if your system got compromised via the Windows Remote Desktop feature you should immediately change the passwords of all users that have access and check the local user accounts where attackers might have added additional accounts.
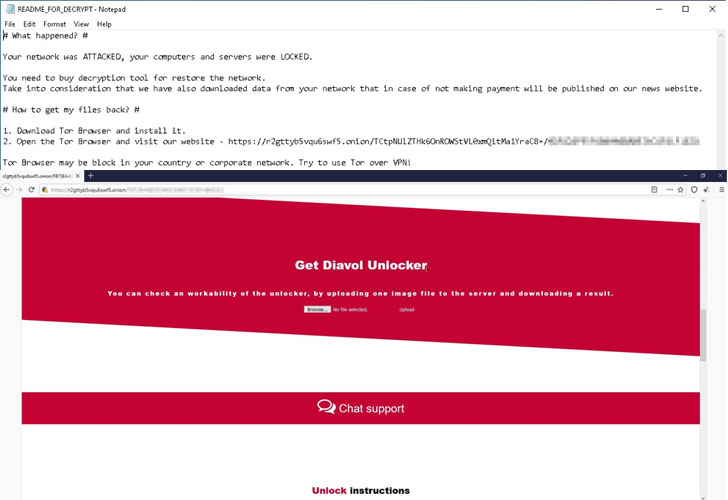
The advice would also be not to change the files names of the original and encrypted files. The decryptor will perform the file name comparisons to pick the correct file extension that was used for encryption.
The decryption tool will ask you for access to a file pair that should consist of one encrypted file and the original one, an unencrypted version of the encrypted file. That is needed to reconstruct the encryption keys in order to decrypt the rest of your data. The file must be near 20 kb in size or larger.
To read an instruction on how to use the decryption tool please proceed to the link.
What is Diavol ransomware?
First detected by cybersecurity specialists in July 2021 this ransomware family showed that it has double extortion functionality. This means that this malware not only encrypts the files but also as the creators of it claims can exfiltrate the data.
Wizard Spider, a cybercrime group who is behind Conti and Ryuk ransomware familie and also operates Trickbot botnet, operates the Diavol ransomware as well.
This ransomware family uses RSA encryption and specifically focuses on files types listed by the operators. The malware designates each file “.lock64” extension subsequently dropping a ransom note with instructions.
The ransomware generates for each victim’s computer a unique identifier and then attempts to connect to a hard coded command and control (C&C) server.
According to the FBI investigation the ransom demands of the Diavol goes up to $500,000 with the lowest sum of $10,000.
TrickBot gang operates Diavol ransomware
The word “Diavol” comes from Romanian and means Devil. The cybersecurity researchers saw it together with Conti ransomware getting deployed in early June 2021 on a network in the same ransomware attack.
The researchers analyzed the two ransomware samples. The found similarities among all included almost identical command-line parameters for the same functionality and the use of asynchronous I/O operations for file encryption queuing. But there was not enough evidence to formally link the two operations.
Months later, researchers from IBM X-Force also detected a strong connection between TrickBot, Anchor and Diavol ransomware. All being the products developed by the TrickBot Gang, aka Wizard Spider.
In January 2022 FBI formally announced that the Diavol ransomware has direct connection to the TrickBot gang sharing in new advisory indicators of compromise that were seen in previous attacks. In addition, the FBI has not confirmed the claims of cybercriminals leaking victims data despite the ransomware notes threatening to do so.
The analysis of Diavol ransomware
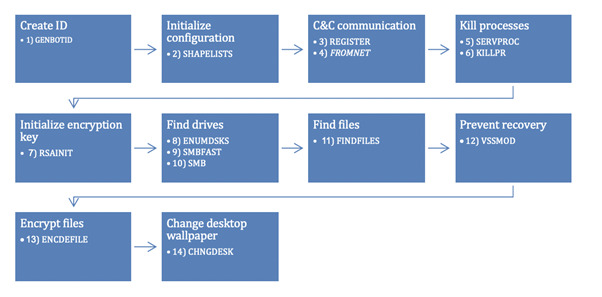
During an execution on a compromised machine the ransomware takes out the code from the images’ PE resource section. It then loads the code from within a buffer with execution permissions.
Extracted code amounts to 14 different routines that gets executed in the following order:
- Creates an identifier for the victim;
- Initializes configuration ;
- Changes the desktop wallpaper;
- Conducts encryption;
- Prevents recovery by deleting shadow copies;
- Finds files to encrypt;
- Finds all drives to encrypt;
- Initializes encryption key;
- Stops services and processes;
- Registers with the C&C server and updates the configuration.
When everything is neatly done the Diavol ransomware changes each encrypted Windows device’s background to a black wallpaper with the next message: “All your files are encrypted! For more information see README-FOR-DECRYPT.txt”
The Diavol ransomware lacks any obfuscation because it doesn’t use any anti disassemble tricks or packing. Though it makes the analysis harder by storing the main routines within bitmap images.
Talking about its encryption procedure the ransomware uses user-mode Asynchronous Procedure Calls (APCs) with an asymmetric encryption algorithm.
That’s what sets apart this ransomware family from the others as other ransomware families use symmetric algorithms that significantly speeds up the encryption process.
Recommended mitigations against Diavol ransomware
User can apply the following mitigations to reduce the risk of ransomware attack:
- Focusing on cybersecurity awareness and training. It’s more for the employers to provide the information for their employees on new emerging threats and what to do in case of an attack;
- Using only private secure networks and avoiding the public ones. You may also consider installing and using a VPN;
- Using multi factor authentication where it can be possible;
- Disabling hyperlinks in emails;
- Installing and regularly updating an antivirus software on all hosts also enabling real time detection;
- Installing updates as soon as they are released;
- Regularly backing up data. Also enable password protection via backup copies offline. In addition making sure the back up data are not accessible for any unauthorized modifications;
- Implementing network segmentation and keeping the offline backup of the data.
Not knowing where the ransomware surprise might come from, it’s always better to have some guarantees in case of the real attack.
To say the last many cybersecurity specialists say the ransomware criminal ecosystem becomes ever more growing particularly with everything rapidly moving to digital existence. They express worries on whether the cybersecurity community keeps up with the pace. To say for sure is hard but those last summer articles and subsequent articles on arresting many ransomware operators show the effort of the cybersecurity community.
