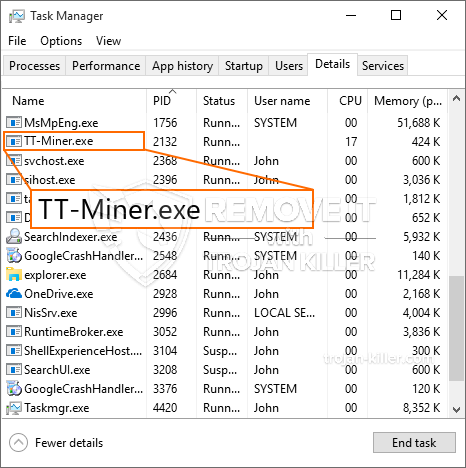
Ein neuer, wirklich schädlich Kryptowährung miner Infektion wurde von Schutz Wissenschaftler identifiziert. die Malware, namens TT-Miner.exe können eine Reihe von Möglichkeiten, Ziel Opfer verunreinigen mit. Die Hauptidee hinter dem TT-Miner.exe Miner besteht darin, Cryptocurrency Miner-Aufgaben auf den Computern von Betroffenen zu verwenden, um Monero-Token auf Kosten der Betroffenen zu erhalten. Das Endergebnis dieses Bergmanns sind die erhöhten Stromkosten, und auch wenn Sie ihn längere Zeit verlassen, kann TT-Miner.exe auch die Elemente Ihres Computers beschädigen.
TT-Miner.exe: Verteilungsmethoden
Das TT-Miner.exe Malware verwendet zwei gängige Ansätze, mit denen Computersystemziele kontaminiert werden:
- Payload Lieferung durch Vor-Infektionen. Wenn eine ältere TT-Miner.exe-Malware auf den Zielsystemen veröffentlicht wird, kann sie sich sofort selbst aktualisieren oder eine neuere Variante herunterladen. Dies ist über den integrierten Update-Befehl möglich, der die Version abruft. Dies wird durch das Anbringen an einen bestimmten vordefinierten Hacker gesteuerten Web-Server durchgeführt, die den Malware-Code bietet. Die heruntergeladene und installierte Infektion erhält sicherlich den Namen eines Windows-Dienstes und wird auch in das Feld eingefügt “%System% temp” Standort. Wesentliche Wohnimmobilien und auch laufende Systemkonfigurationsdaten werden transformiert, um eine anhaltende und auch leise Infektion zu ermöglichen.
- Software Application Vulnerability Exploits. Es wurde tatsächlich festgestellt, dass die aktuellste Version der TT-Miner.exe-Malware durch einige Exploits hervorgerufen wird, allgemein verstanden, die in den Ransomware Streiks genutzt wird. Die Infektionen werden durch Targeting offene Lösungen über den TCP-Port erfolgen. Die Angriffe sind von einem Hacker-gesteuerte Struktur automatisiert, die sucht, wenn der Port offen ist,. Wenn dieses Problem behoben ist, wird die Lösung gescannt und Informationen dazu abgerufen, einschließlich jeder Art von Version sowie Setup-Daten. Exploits und prominente Benutzernamen und Passwort auch Mischungen kann getan werden,. Wenn die Manipulation gegen den anfälligen Code ausgelöst wird, wird der Miner zusätzlich zur Hintertür bereitgestellt. Dies bietet sicherlich die eine doppelte Infektion.
Neben diesen Techniken können auch verschiedene andere Methoden verwendet werden. Bergleute können durch Phishing-E-Mails zerstreut werden, die SPAM-artig in großen Mengen verschickt werden und auf Tricks des sozialen Designs angewiesen sind, um die Opfer zu rätseln, dass sie eine Nachricht von einem legitimen Dienst oder Unternehmen erhalten haben. Die Infektionsdateien können entweder direkt verbunden oder in Multimedia-Inhalten oder Text-Weblinks in die Körperkomponenten eingefügt werden.
Die Täter können zusätzlich böswillige Landing-Webseiten erstellen, die das Herunterladen und Installieren von Seiten durch Lieferanten ermöglichen, Software-Download-Sites und verschiedene andere Bereiche, auf die häufig zugegriffen wird. Wenn sie ähnliche scheinbare Domainnamen wie echte Adressen sowie Sicherheitszertifizierungen verwenden, werden die Benutzer möglicherweise dazu gedrängt, sich mit ihnen zu verbinden. Manchmal nur öffnen sie die Bergmann-Infektion kann dazu führen,.
Eine andere Methode wäre sicherlich die Verwendung von Transportdienstleistern, die unter Verwendung der oben genannten Techniken oder mittels Filesharing-Netzwerken verbreitet werden können, BitTorrent ist zu einem der beliebtesten. Es wird häufig verwendet, um sowohl seriöse Software und Dokumente als auch Pirateninhalte zu verbreiten. Zwei der prominentesten Payload-Anbieter sind die folgenden:
Andere Techniken, über die die Übeltäter nachdenken können, bestehen darin, Browser-Hijacker zu verwenden - gefährliche Plugins, die mit den gängigsten Webbrowsern kompatibel gemacht werden. Sie werden mit falschen Kundenbewertungen sowie Designer-Anmeldeinformationen in den entsprechenden Repositories veröffentlicht. In vielen Fällen können die Zusammenfassungen von Screenshots aus, Videos sowie ausgefallene Zusammenfassungen, die zu hervorragenden Funktionsverbesserungen und Leistungsoptimierungen anregen. Bei der Installation werden sich jedoch die Gewohnheiten der betroffenen Webbrowser sicherlich ändern- Kunden werden sicherlich feststellen, dass sie auf eine von Hackern kontrollierte Zielseite weitergeleitet werden und auch ihre Einstellungen geändert werden können – die Standard-Startseite, Online-Suchmaschine sowie brandneue Registerkarten Seite.

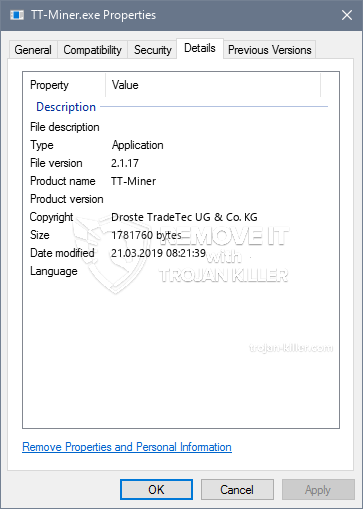
TT-Miner.exe: Analyse
Die Malware TT-Miner.exe ist eine zeitlose Situation eines Cryptocurrency Miner, die je nach Anordnung eine Vielzahl schädlicher Aktionen verursachen kann. Hauptziel ist es, komplizierte mathematische Aufgaben auszuführen, die sicherlich von den verfügbaren Systemquellen profitieren: Zentralprozessor, GPU, Speicher und Festplattenspeicher. Die Methode, mit der sie arbeiten, besteht darin, eine Verbindung zu einem speziellen Webserver namens Mining Pool herzustellen, von dem der angeforderte Code heruntergeladen wird. So schnell, wie bei den Aufgaben heruntergeladen wird, wird es auf einmal begonnen, Es können mehrere Umstände durchgeführt werden, sobald. Wenn eine bestimmte Aufgabe erledigt ist, wird sicherlich eine weitere heruntergeladen und an ihrer Stelle installiert, und die Schleife wird fortgesetzt, bis das Computersystem ausgeschaltet wird, die Infektion entfernt wird oder ein ähnlicher Anlass findet statt. Kryptowährung werden zu den kriminellen Controller kompensiert werden (Hacker-Gruppe oder ein einsamer Hacker) direkt an ihren Geldbeutel.
Ein gefährliches Merkmal dieser Klassifizierung von Malware ist, dass Beispiele wie dieses alle Systemressourcen beanspruchen und das Computersystem des Opfers praktisch sinnlos machen können, bis die Gefahr vollständig beseitigt ist. Die meisten von ihnen enthalten ein konsistentes Setup, das es wirklich schwierig macht, sie loszuwerden. Diese Befehle werden sicherlich Änderungen Boot Alternativen machen, Setup-Daten und auch Windows-Registrierungswerte, mit denen die Malware TT-Miner.exe beim Einschalten des Computers automatisch gestartet wird. Der Zugriff auf Heilungsmenüs sowie Optionen ist möglicherweise blockiert, was viele manuelle Entfernungsanleitungen nahezu unwirksam macht.
Diese spezifische Infektion wird sicherlich Setup eine Windows-Lösung für sich, Die Einhaltung der durchgeführten Sicherheitsbewertung, die den Aktivitäten entspricht, wurde beobachtet:
Während des Miner-Vorgangs kann die verknüpfte Malware eine Verbindung zu bereits ausgeführten Windows-Lösungen und installierten Anwendungen von Drittanbietern herstellen. Auf diese Weise stellen die Systemadministratoren möglicherweise nicht fest, dass die Quelltonnen aus einem separaten Prozess stammen.
| Name | TT-Miner.exe |
|---|---|
| Kategorie | Trojan |
| Unterkategorie | Kryptowährung Miner |
| Gefahren | Hohe CPU-Auslastung, Internet Geschwindigkeitsreduzierung, PC stürzt ab und gefriert und etc. |
| Hauptzweck | Um Geld für Cyber-Kriminelle zu machen |
| Verteilung | Torrents, Gratis Spiele, Cracked Apps, Email, fragwürdige Websites, Abenteuer |
| Entfernung | Installieren GridinSoft Anti-Malware um TT-Miner.exe zu erkennen und zu entfernen |
Diese Art von Malware-Infektionen ist besonders effizient bei der Ausführung erweiterter Befehle, wenn sie so eingerichtet sind. Sie basieren auf einem modularen Aufbau, der es den kriminellen Kontrolleuren ermöglicht, alle Arten gefährlicher Gewohnheiten zu verwalten. Eines der beliebtesten Beispiele ist die Änderung der Windows-Registrierung – Anpassungszeichenfolgen, die mit dem Betriebssystem verbunden sind, können schwerwiegende Effizienzunterbrechungen und auch die mangelnde Verfügbarkeit von Windows-Diensten auslösen. Je nach Umfang der Änderungen kann der Computer dadurch zusätzlich völlig unbrauchbar werden. Auf der anderen Seite Manipulation von worths Registry auf jede Art von Drittanbietern gehören, installierten Anwendungen können sie sabotieren. Einige Anwendungen können möglicherweise nicht vollständig gestartet werden, während andere plötzlich nicht mehr funktionieren.
Dieser spezielle Miner in seiner aktuellen Version konzentriert sich auf das Extrahieren der Monero-Kryptowährung mit einer modifizierten Version der XMRig-CPU-Mining-Engine. Wenn sich die Projekte danach als effektiv erweisen, können zukünftige Variationen von TT-Miner.exe in Zukunft veröffentlicht werden. Da die Malware nutzt Software-Schwachstellen Ziel-Hosts verunreinigen, es kann als Trojaner auch mit Ransomware-Komponente eines gefährlichen Koinfektion sein.
Die Eliminierung von TT-Miner.exe wird dringend empfohlen, vorausgesetzt, Sie nutzen die Chance, nicht nur einen hohen Stromverbrauch zu verursachen, wenn dieser auf Ihrem COMPUTER betrieben wird, Der Bergmann kann jedoch auch verschiedene andere unerwünschte Aktivitäten ausführen und Ihren PC vollständig beschädigen.
Prozess zum Entfernen von TT-Miner.exe
SCHRITT 1. Zuerst, Sie müssen GridinSoft Anti-Malware herunterladen und installieren.
SCHRITT 2. Dann sollten Sie wählen “Schneller Scan” oder “Kompletter Suchlauf”.
SCHRITT 3. Führen Sie Ihren Computer scannen
SCHRITT 4. Nachdem der Scan abgeschlossen, Sie müssen klicken Sie auf “Sich bewerben” Schaltfläche zum Entfernen von TT-Miner.exe
SCHRITT 5. TT-Miner.exe entfernt!
Video Guide: Verwendung von GridinSoft Anti-Malware zum Entfernen von TT-Miner.exe
Wie Sie Ihren PC vor einer reinfected mit verhindern “TT-Miner.exe” in der Zukunft.
Eine leistungsstarke Antivirus-Lösung, und Block dateilosen Malware erkennen kann, ist, was Sie brauchen! Herkömmliche Lösungen erkennen Malware auf Basis von Virendefinitionen, und daher können sie oft nicht erkennen, “TT-Miner.exe”. GridinSoft Anti-Malware bietet Schutz gegen alle Arten von Malware, einschließlich dateilosen Malware wie “TT-Miner.exe”. GridinSoft Anti-Malware bietet Cloud-basierten Verhaltensanalysators alle unbekannten Dateien einschließlich Zero-Day-Malware zu blockieren. Eine solche Technologie kann erkennen und vollständig entfernen “TT-Miner.exe”.







