
Im Rahmen des „Tuesday-Updates“ Mais, Microsoft reparierte die kritische Sicherheitslücke CVE-2019-0708 (auch als BlueKeep bekannt) für den Betrieb von Remote Desktop Service im Zusammenhang (RDS) und RDP.
EINObwohl die technischen Details des Problems aufgrund seiner hohen Bedrohung nicht bekannt gegeben wurden, Es ist bekannt, dass Angreifer mit Hilfe dieses Fehlers beliebigen Code ohne Autorisierung ausführen und ihre Malware wie einen Wurm verbreiten können, wie, Zum Beispiel, es war berühmt WannaCry und NotPetya Malware.Das Problem ist gefährlich für Windows Server 2008, Windows 7, Windows 2003 und Windows XP, für diese Versionen wurden veröffentlicht Sicherheitsupdates.
Microsoft-Experten haben bereits zweimal vor diesem Problem gewarnt, und Experten mehrerer Informationssicherheitsunternehmen (einschließlich Zerodium, McAfee, Check Point und Kaspersky Lab) und unabhängige Forscher haben einen Beweis für das Exploit-Konzept für BlueKeep erstellt.
Der Code für diese Exploits wurde aufgrund eines hohen Risikos nicht öffentlich zugänglich gemacht. In Ergänzung, Für die Sicherheitslücke wurde bereits ein Modul erstellt Metasploit (auch nicht öffentlich zugänglich).
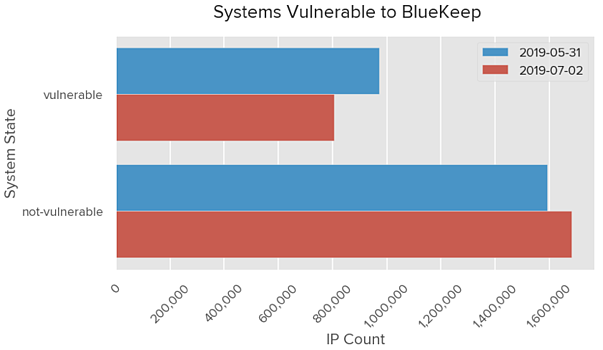
Letzte Woche, BitSight Fachwelt veröffentlicht eine weitere deprimierende Statistik: entsprechend ihrer Daten, Über 800,000 Geräte sind weiterhin anfällig für BlueKeep. Offenbar, Benutzer dieser Geräte sollten so schnell wie möglich über die Installation von Patches nachdenken, seit gestern auf gitHub war veröffentlichte eine Präsentation Detaillierte Beschreibung der Verwendung der Sicherheitsanfälligkeit und Erstellung eines Exploits.
Folien dieser Präsentation sind fast ausschließlich in Chinesisch verfasst. Auf ihnen erwähnt 2019 Security Development Conference und Name des berühmten chinesischen Unternehmens Tencent KeenLab. Die beiden Folien enthalten auch das Wort “Demo”.
ArsTechnica Journalisten fragte Spezialisten für Informationssicherheit über die Präsentation, Befragung eines unabhängigen Experten Marcus Hutchins und Rendition Infosec Mitbegründer und ehemaliger Entwickler von Exploits für die NSA, Jake Williams.
"Eines der wenigen Dinge, die realen Angriffen im Wege stehen, ist das Know-how, das erforderlich ist, um Exploits zu schreiben, die Code aus der Ferne ausführen, ohne zuerst den Computer zum Absturz zu bringen.", - sagte Marcus Hutchins.
Im Algemeinen, Beide Spezialisten sind sich einig, dass die Situation sehr ernst ist, Da die Veröffentlichung einer detaillierten Präsentation die Chancen für die Erstellung von RCE-Exploits für BlueKeep erheblich verringert. Tatsache ist, dass die Folien detailliert zeigen, wie Heap-Sprühen implementiert wird, Das ist, nach der Präsentation, ist eine der schwierigsten Aufgaben bei der Erstellung eines Exploits.
“Es ist die detaillierteste öffentlich verfügbare technische Dokumentation, die wir bisher gesehen haben. ", - erklärte Jake Williams.
Er schlug auch vor, dass Tencent KeenLab-Experten offensichtlich auf der Konferenz einen RCE-Exploit für BlueKeep erstellten und demonstrierten, obwohl der PoC selbst nicht veröffentlicht wurde.
lesen Sie auch: Teilnehmer des Metasploit-Projekt erstellt ein Arbeitsmodul für die BlueKeep Verwundbarkeit ausnutzen
Vorher, Sicherheitsexperten gingen davon aus, dass die Exploits von BlueKeep ab Mitte August allgemein verfügbar sein würden, nach dem Ende von Schwarzer Hut und Defcon Konferenzen in Las Vegas. jedoch, Jetzt neigen sie dazu anzunehmen, dass dies früher geschehen wird.
