
Sixgill, an Israeli B2B cyber intelligence company that analyzes and monitors the deep web and dark web for threat intelligence, on its company’s blog shared their recent research into the depths of the Telegram criminal community. According to the specialists, Telegram, a freeware, cross-platform, cloud-based instant messaging (JEG ER) service became the real “ choice of the year” for various kinds of cybercriminal enterprises. In a four part series they will cover the most popular trends in criminal communities on Telegram.
Cyberkriminelle flyttede deres virksomhed til Telegram
For ikke længe siden var den vigtigste markedsplads for cyberkriminelle "mørke websteder" med en .onion-udvidelse. Men i dag bevæger tendensen sig i retning af noget som Telegram. Fordi du skal lægge nogle kræfter i vedligeholdelse og arbejde på et traditionelt "dark web"-forum, mens Telegram tilbyder dig en hurtigere og nemmere måde at etablere forbindelse til potentielle kunder. cyberkriminelle skal kun oprette en kanal, og markedspladsen er klar til at passe kundernes behov. Selvom sådanne kanaler ikke lever for længe, de bliver hurtigt forbudt for at overtræde servicevilkårene.
Sikkerhedsforskere besluttede at dykke ned i dybet af det nye cyberkriminel favorit hub og se, hvilke trends der går der. De undersøgte emnerne for kompromitterede finansielle konti, ulovlige genstande til salg og malware; emner, der er de mest populære blandt det cyberkriminelle samfund.
Første del af forskningen fokuserer på finansiel cyberkriminalitet og hvilke tendenser, der foregår her. Om dette emne specialister afslører en interessant kendsgerning, at på trods af den betydelige vækst i e-handel i tider med COVID-19-pandemi, forbrydelserne forbundet med kompromitterede kreditkort, banklogfiler (kompromitterede konti) og pengeoverførsler (hvidvaskning) faldet bemærkelsesværdigt lavt 2021, aftagende nær 60% fra sin 2020 sats. Men på trods af dette, i perioden mellem august 2020 til december 2021 det samlede antal mistænkelige omtaler om disse emner har stået stabilt rundt 3,500.
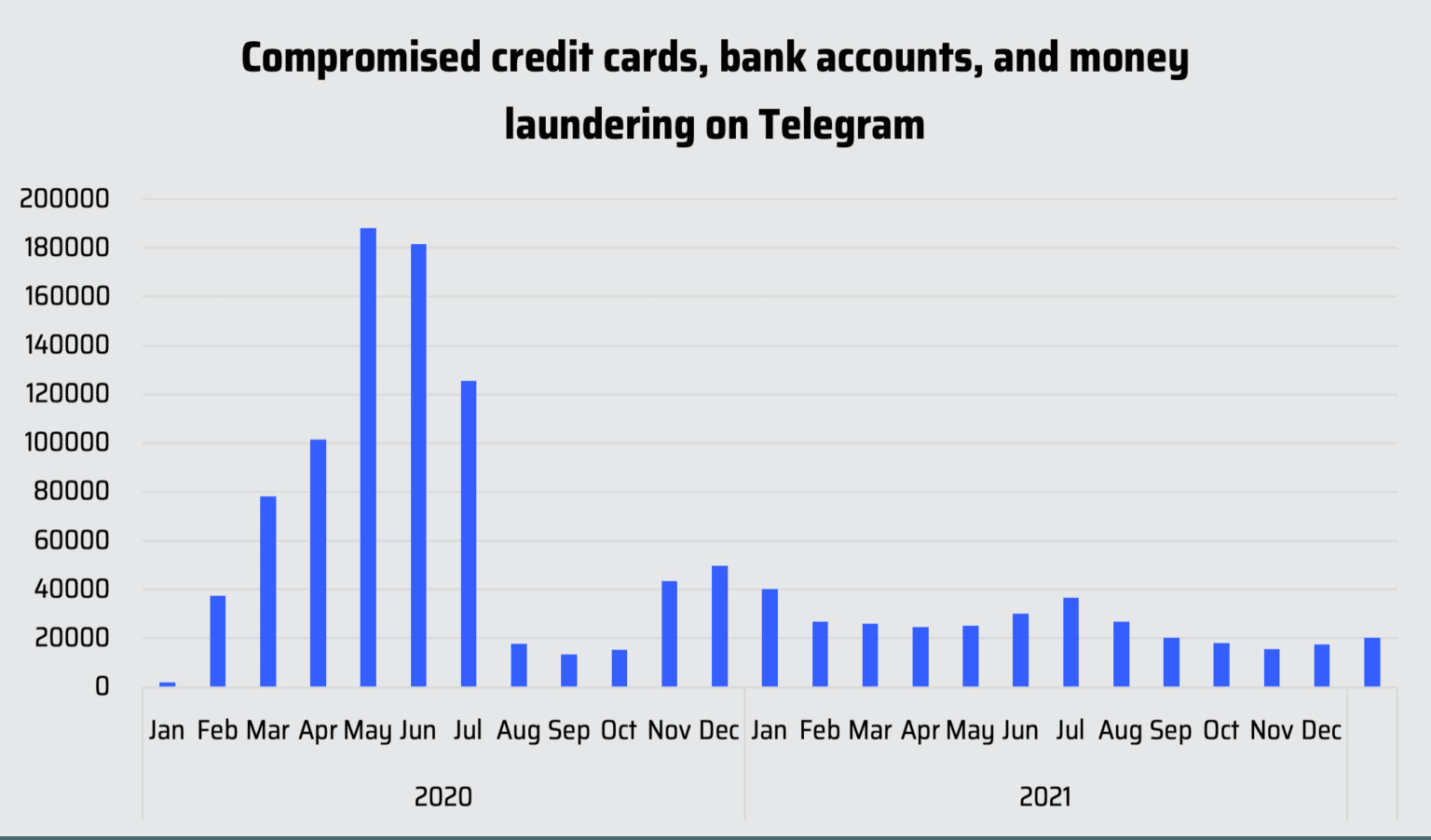
Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode. Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode 2021 Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode ( Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode). Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode, Specialisterne tilføjer, at selvom statistikken kan være overraskende, opdagede de de samme tendenser med salg af kompromitterede kreditkort solgt på underjordiske markeder i samme periode. It might also be the reason that ransomware (one the most evolved kind of cybercrime today) has proved itself quite a lucrative field in the past years and with everything steadily moving to the internet it promises more.
“You gotta keep working to keep money flowing”
So what’s in an agenda today among financial cybercriminals? The illicit activities in this field usually involve money transferring services, bank logs and compromised credit cards. They are the most popular and just by typing in for example “ bank logs” in the Telegram search bar you can find channels with up to thousands subscribers on it. Scrolling down some of them I thought but where’s these sort of the “guaranties” on the deal? Cyber security specialists definitely should try to run an experiment on the question.
You know what money transferring services are. Users use them to move funds from one account and deposit them into another. The same with cybercriminals, using these services allows them to obfuscate the origin of stolen funds, launder them and successfully move them across the world. In Telegram criminal channels you can find the right service for the right price. som regel criminals use the most popular one money transferring services like PayPal, Cash App, og andre.
“Experienced” cybercriminals know very well that law enforcements may not yet knock on their door but they watching them. The thing is simple: if one cryptocurrency wallet was suspected in an illegal money flow activity then it can be “direct shot in the head” to use it again. The service is more popular with ransomware criminals especially if it`s some big groups of hackers with their affiliates. Money transfering service allows in such a case to quietly dissipate the stolen funds.
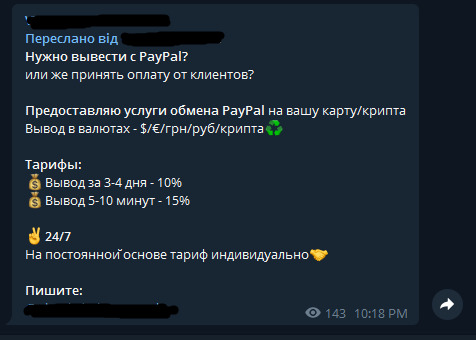
The screenshot below says in Russian: “ Need a cashout with PayPal? Or you need to receive the payment from clients? I offer the PayPal exchange service to your account/cryptocurrency wallet. Currency cashout: $/€/ hryvnias/rubles/cryptocurrency. Price: cashout in 3-4 days — 10%. Cashout in 5-10 minutes — 15%. 24/7. Prices for long term partnership are individual. Write to.”
The next kind of activity concerns bank logs. On a dark web logs refer to compromised bank credentials. Usually this kind of info includes more than just the username and password needed to login in to compromised accounts. But often it has highly sensitive information such as the personal answers to security verification questions. The price depends on the balances of the compromised bank account in an offer. Generally cybercriminals sell or buy them to conduct cashouts which means to fully empty the account of the funds.
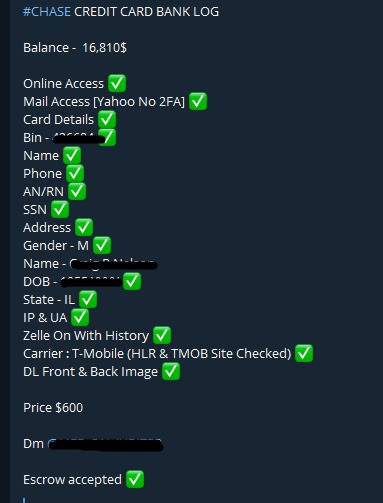
You may have noticed on both posts the interesting word “escrow”. No it`s not some kind of a code word for something criminal but instead this word means a normal legal term. And according to the investopedia.com “Escrow is a legal concept describing a financial instrument whereby an asset or escrow money is held by a third party on behalf of two other parties that are in the process of completing a transaction”. To explain it in the context of our topic it means when one criminal, For eksempel, buy something in another criminal but they are not sure the one that they will receive the money and other will receive their goods or service. The common ground in this case would be escrow. The seller gets money when the buyer gets service or goods or vice versa. That`s what this word here stands for

Compromised credit cards are another lucrative activity for cybercriminals. The compromised cards usually belong to the most widely used financial institutions like Mastercard, Visa, Western Union, Wells Fargo, the Bank of America and Chase Bank. The same as on the dark web markets you can buy cards`dumps or those including CVV/CVV2 information. Dumps mean the cards that contain segments of unencrypted data located on the magnetic strip of a card. The data includes account number, the cardholder’s name and other validating points that banks use to confirm the transaction. Criminals have to create the so-called physical clones of cards to use dumps.

With CVV/CVV2 ( used for remote transactions), På den anden side, everything is much more simple because it allows criminals to empty funds online without risking that much. According to researchers CVV/CVV2 cards are more convenient offering the much needed anonymity for criminals and therefore they are in higher demand with ratio ~60% CVV/CVV2 to ~40% dumps.
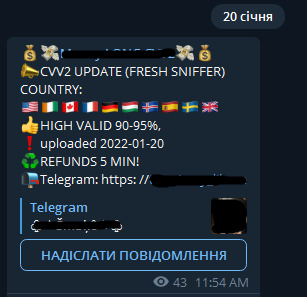
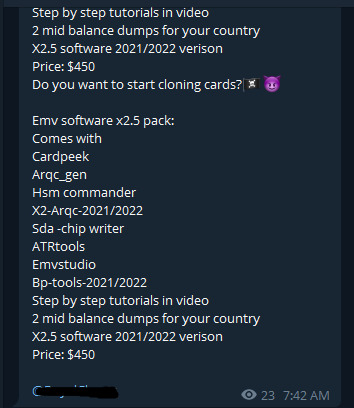
For law enforcement, the rising popularity of this messaging app among cybercriminals makes everything harder. When they just shut another channel another one will appear after a while. You can say it’s like that whack a mole game that the current cybercrime industry begins to look like. And it concerns not only financial kinds of crimes but the selling of illicit goods, Malware, etc. And that lone drug dealer on the street quickly became a thing of the past.
