En ny, virkelig farligt cryptocurrency minearbejder virus er blevet opdaget af sikkerhedsmæssige forskere. den malware, hedder Wuacul8.exe kan forurene målsyge ved brug af en række midler. Hovedidéen bag den Wuacul8.exe minearbejder er at bruge cryptocurrency minearbejder opgaver på edb-systemerne i syge for at erhverve Monero tokens på mål omkostninger. The result of this miner is the raised electrical power bills as well as if you leave it for longer periods of time Wuacul8.exe may even harm your computers components.
Wuacul8.exe: distributionssystemer Metoder
Det Wuacul8.exe malware gør brug af 2 popular approaches which are made use of to infect computer system targets:
- Payload Levering hjælp Prior Infektioner. If an older Wuacul8.exe malware is released on the victim systems it can automatically update itself or download a more recent variation. Dette er muligt ved hjælp af den integrerede opdatering kommando, som får lanceringen. Dette gøres ved at linke til en bestemt foruddefineret hacker-kontrollerede webserver, der tilvejebringer den Malwarekoden. The downloaded and install infection will certainly acquire the name of a Windows service and also be placed in the “%systemet% temp” areal. Vital residential properties and running system setup documents are transformed in order to allow a consistent and silent infection.
- Software sårbarhed udnytter. The latest version of the Wuacul8.exe malware have actually been discovered to be triggered by the some ventures, almindeligt kendt for at blive brugt i ransomware-angrebene. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Angrebene er automatiseret af en hacker-kontrollerede rammer, der søger ud af, om porten er åben. If this condition is fulfilled it will scan the solution and also get details concerning it, herunder enhver form for variation og også konfigurationsoplysninger. Exploits and preferred username and also password mixes may be done. When the manipulate is set off versus the at risk code the miner will certainly be released together with the backdoor. Dette vil helt sikkert give det en dobbelt infektion.
In addition to these techniques other approaches can be utilized as well. Miners can be dispersed by phishing e-mails that are sent out wholesale in a SPAM-like way as well as rely on social design tricks in order to perplex the targets into thinking that they have actually gotten a message from a legit service or company. The virus documents can be either straight affixed or placed in the body components in multimedia content or text links.
The bad guys can likewise develop harmful landing pages that can impersonate vendor download and install web pages, websteder til download af software og forskellige andre ofte tilgåede steder. When they make use of similar appearing domain names to genuine addresses and also protection certificates the customers might be persuaded into engaging with them. I nogle tilfælde blot at åbne dem kan forårsage minearbejder infektion.
An additional approach would be to make use of payload providers that can be spread making use of the above-mentioned methods or through data sharing networks, BitTorrent er en af en af de mest foretrukne dem. It is regularly made use of to distribute both legitimate software as well as documents as well as pirate content. 2 of the most prominent payload carriers are the following:
Other approaches that can be thought about by the criminals consist of the use of internet browser hijackers -hazardous plugins which are made compatible with the most prominent internet browsers. They are posted to the appropriate databases with fake customer testimonials as well as designer credentials. I mange tilfælde resuméerne kan bestå af screenshots, video clips and also fancy descriptions promising terrific attribute enhancements as well as efficiency optimizations. Nonetheless upon setup the behavior of the affected internet browsers will certainly change- users will certainly discover that they will certainly be rerouted to a hacker-controlled landing page as well as their setups could be changed – standard startside, søgemaskine samt nye faner side.
Wuacul8.exe: Analyse
The Wuacul8.exe malware is a timeless instance of a cryptocurrency miner which relying on its arrangement can create a wide variety of dangerous actions. Its major goal is to carry out intricate mathematical jobs that will make use of the offered system resources: CPU, GPU, hukommelse og også plads på harddisken. The method they operate is by connecting to an unique web server called mining pool where the called for code is downloaded. Så hurtigt som blandt opgaverne bliver downloadet det vil blive påbegyndt samtidigt, adskillige omstændigheder kan køres på én gang. When a provided task is finished another one will certainly be downloaded and install in its area as well as the loop will certainly proceed until the computer is powered off, the infection is eliminated or another similar event occurs. Cryptocurrency vil helt sikkert blive belønnet for de kriminelle controllere (hacking team eller en enkelt cyberpunk) lige til deres budgetter.
A harmful attribute of this classification of malware is that examples similar to this one can take all system sources as well as practically make the sufferer computer system pointless until the danger has been completely eliminated. Most of them feature a relentless installment that makes them actually difficult to remove. Disse kommandoer vil helt sikkert foretage ændringer også muligheder, configuration data and also Windows Registry values that will make the Wuacul8.exe malware start immediately once the computer is powered on. Access to recuperation menus and also choices might be obstructed which renders many manual removal guides virtually useless.
Denne særlige infektion vil arrangement en Windows-tjeneste for sig selv, following the carried out safety analysis ther adhering to activities have actually been observed:
. During the miner procedures the linked malware can attach to already running Windows services as well as third-party mounted applications. By doing so the system managers might not see that the resource tons originates from a separate process.
| Navn | Wuacul8.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Wuacul8.exe |
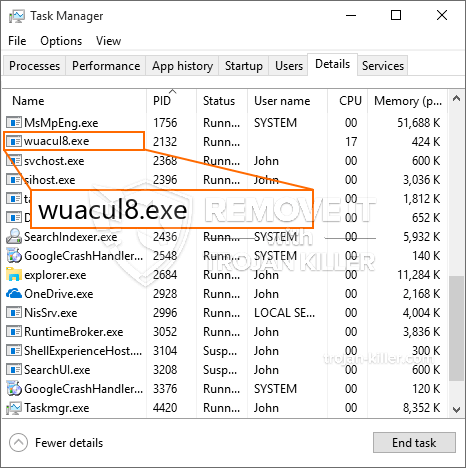
id =”81521″ align =”aligncenter” width =”600″] Wuacul8.exe
Wuacul8.exe
Disse slags malwareinfektioner er særligt effektive til udførelse sofistikerede kommandoer, hvis konfigureret således. De er baseret på en modulær ramme, der tillader de kriminelle kontroller at håndtere alle slags farlige vaner. Et af de fremtrædende tilfælde er ændringen af Windows-registreringsdatabasen – ændringsstrenge forbundet med operativsystemet kan skabe betydelige ydeevneforstyrrelser og også manglen på mulighed for at få adgang til Windows-tjenester. Under henvisning til omfanget af forandringer, det kan desuden gøre computersystemet helt meningsløst. På den anden side kontrol af Registry worths kommer fra en hvilken som helst form for tredjepart monteret programmer kan underminere dem. Nogle programmer kan stoppe med at arbejde for at indføre helt, mens andre uventet kan stoppe med at arbejde.
Denne bestemte minearbejder i sin eksisterende variation er koncentreret om at udvinde Monero-kryptovalutaen med en modificeret version af XMRig CPU-minemotoren. If the projects show effective then future versions of the Wuacul8.exe can be released in the future. Da malware udnytter software program susceptabilities at inficere target værter, det kan være en del af en skadelig co-infektion med ransomware samt trojanske heste.
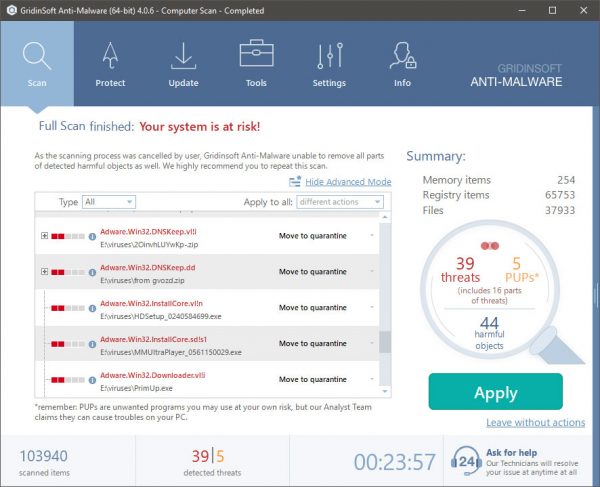
Removal of Wuacul8.exe is highly suggested, i betragtning af, at du risikerer ikke bare en stor elregning, hvis den virker på din COMPUTER, alligevel kan minearbejderen også udføre andre uønskede aktiviteter på den og endda skade din pc permanent.
Wuacul8.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
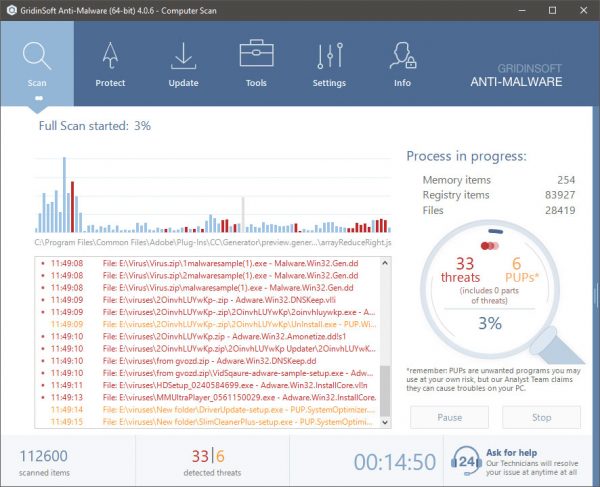
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
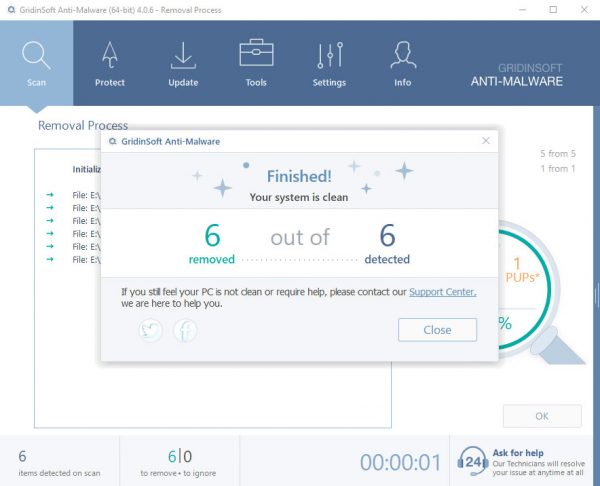
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Wuacul8.exe
TRIN 5. Wuacul8.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Wuacul8.exe
Hvordan undgår din pc fra at blive inficeret med “Wuacul8.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Wuacul8.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Wuacul8.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Wuacul8.exe”.