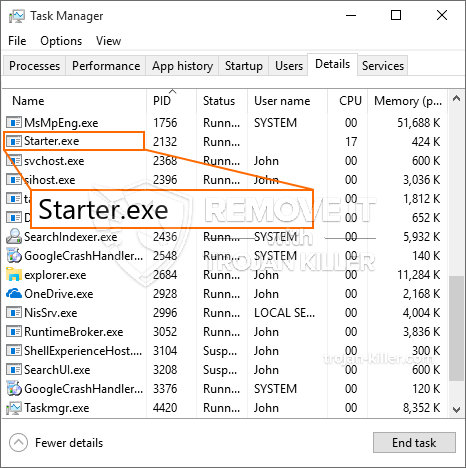
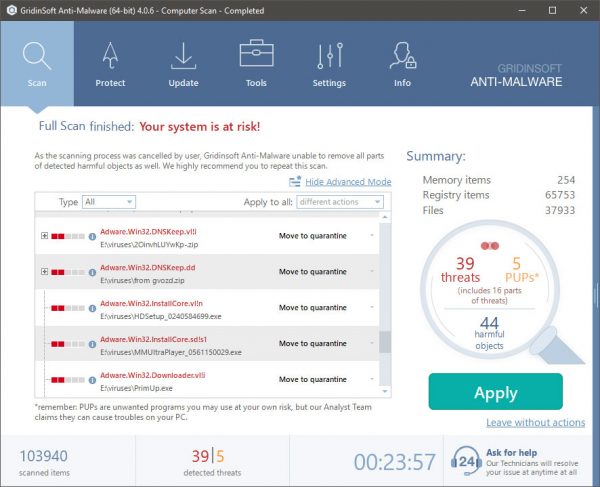
En ny, ekstremt farlig kryptokurrency minearbejde er fundet af beskyttelsesforskere. den malware, hedder Starter.exe kan inficere målsyge på en række måder. Essensen bag Starter.exe-minearbejderen er at bruge cryptocurrency-minearbejder på ofres computersystemer for at opnå Monero-tokens til måludgifter. The outcome of this miner is the elevated power expenses and also if you leave it for longer time periods Starter.exe may even harm your computers elements.
Starter.exe: distributionssystemer Metoder
Det Starter.exe malware udnytter 2 populære teknikker, som bruges til at inficere edb-system mål:
- Payload Levering via Prior Infektioner. If an older Starter.exe malware is deployed on the sufferer systems it can automatically upgrade itself or download a more recent variation. This is feasible by means of the built-in upgrade command which gets the release. This is done by attaching to a certain predefined hacker-controlled web server which provides the malware code. The downloaded and install virus will acquire the name of a Windows service as well as be put in the “%systemet% temp” placere. Important properties and also operating system configuration files are transformed in order to allow a persistent and also quiet infection.
- Software programmet sårbarhed udnytter. The most recent variation of the Starter.exe malware have been found to be caused by the some exploits, bredt anerkendt for at blive brugt i ransomware-angrebene. Infektionerne er færdig ved at målrette åbne løsninger via TCP port. Overgrebene er automatiseret af en hacker-kontrolleret ramme som søger efter hvis porten er åben. If this problem is satisfied it will certainly scan the service and recover details about it, including any variation as well as configuration information. Exploits and also popular username and also password mixes may be done. When the exploit is set off against the prone code the miner will certainly be deployed in addition to the backdoor. Dette vil præsentere en dobbelt infektion.
In addition to these approaches other strategies can be used as well. Miners can be distributed by phishing emails that are sent wholesale in a SPAM-like manner and depend upon social engineering methods in order to perplex the victims into thinking that they have received a message from a legit solution or business. The virus data can be either straight attached or put in the body materials in multimedia content or message web links.
The crooks can also develop harmful landing web pages that can impersonate vendor download pages, software application download websites and other regularly accessed places. When they make use of similar seeming domain names to reputable addresses and safety certifications the customers might be pushed right into engaging with them. Undertiden blot åbne dem kan udløse minearbejder infektion.
One more technique would certainly be to make use of payload service providers that can be spread out utilizing the above-mentioned techniques or via data sharing networks, BitTorrent er blandt de mest foretrukne dem. It is often used to distribute both legit software as well as files as well as pirate material. 2 af de mest populære udbydere af nyttelast er følgende:
Other approaches that can be thought about by the bad guys consist of using browser hijackers -hazardous plugins which are made suitable with one of the most preferred web browsers. They are submitted to the pertinent databases with fake user reviews and designer credentials. I de fleste tilfælde beskrivelserne kan omfatte skærmbilleder, videos and fancy descriptions encouraging excellent feature enhancements and also efficiency optimizations. Men ved afbetaling vil vanerne for de påvirkede webbrowsere ændre sig- customers will certainly find that they will certainly be rerouted to a hacker-controlled landing web page and their setups might be changed – standard startside, online søgemaskine og også helt nye faner webside.
Starter.exe: Analyse
The Starter.exe malware is a classic situation of a cryptocurrency miner which depending on its configuration can trigger a wide range of dangerous activities. Its primary objective is to perform complicated mathematical tasks that will certainly capitalize on the readily available system resources: CPU, GPU, hukommelse og harddisk plads. The method they work is by connecting to a special server called mining pool from where the needed code is downloaded. As soon as among the tasks is downloaded it will certainly be started at the same time, flere omstændigheder kan udføres på en gang. When a given job is completed one more one will certainly be downloaded and install in its location and also the loophole will certainly continue till the computer is powered off, the infection is eliminated or an additional similar occasion happens. Cryptocurrency vil blive belønnet for de kriminelle controllere (hacking gruppe eller en ensom cyberpunk) lige til deres budgetter.
A dangerous characteristic of this group of malware is that examples such as this one can take all system sources and also practically make the victim computer unusable till the risk has actually been entirely removed. Most of them include a persistent installment which makes them actually challenging to eliminate. Disse kommandoer vil foretage ændringer til at starte alternativer, setup data as well as Windows Registry values that will make the Starter.exe malware beginning immediately once the computer is powered on. Access to recuperation food selections and alternatives might be blocked which renders lots of manual removal overviews virtually ineffective.
Denne særlige infektion vil sætte en Windows-løsning for sig selv, adhering to the carried out security evaluation ther following actions have been observed:
. During the miner operations the connected malware can hook up to currently running Windows services as well as third-party set up applications. By doing so the system managers might not observe that the resource tons comes from a separate process.
| Navn | Starter.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Starter.exe |
id =”82070″ align =”aligncenter” width =”600″] Starter.exe
Starter.exe
Disse former for malware-infektioner er især pålidelige til at udføre innovative kommandoer, hvis de er konfigureret sådan. They are based on a modular framework allowing the criminal controllers to orchestrate all kinds of hazardous behavior. Et af de fremtrædende eksempler er ændringen af Windows-registreringsdatabasen – alterations strings connected by the os can trigger major performance interruptions and the inability to gain access to Windows services. Depending upon the scope of changes it can additionally make the computer system completely unusable. På den anden side regulering af Registry værdier, der tilhører enhver tredjepart monteret programmer kan sabotere dem. Some applications might fail to release altogether while others can unexpectedly quit working.
This particular miner in its current version is concentrated on mining the Monero cryptocurrency having a modified version of XMRig CPU mining engine. If the campaigns verify effective after that future variations of the Starter.exe can be launched in the future. Da malware udnytter sårbarheder i software til at inficere target værter, det kan være en del af en skadelig co-infektion med ransomware og også trojanske heste.
Elimination of Starter.exe is strongly advised, because you take the chance of not just a big electricity bill if it’s running on your PC, but the miner might also carry out various other unwanted tasks on it as well as also harm your PC completely.
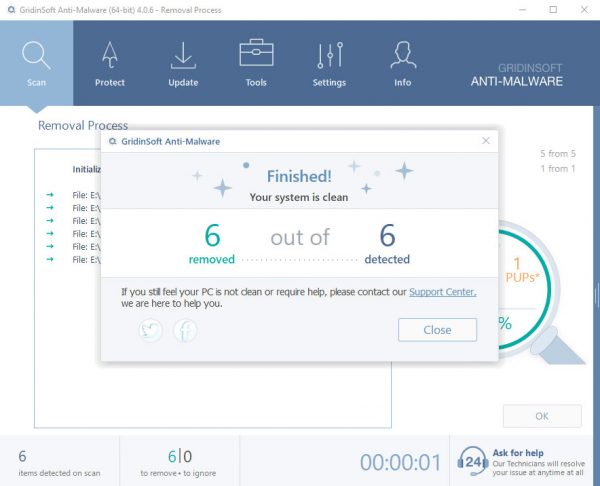
Starter.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
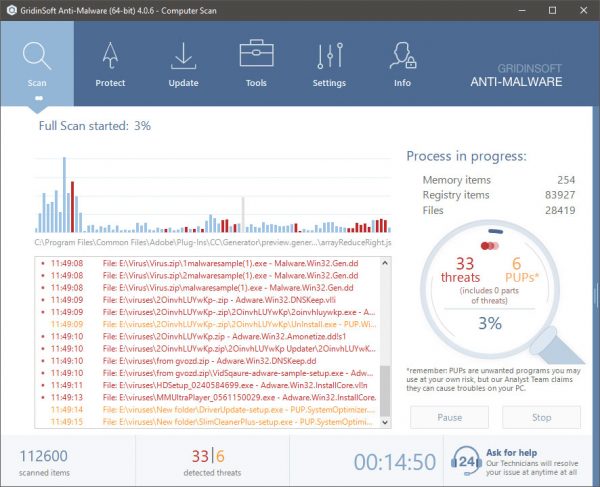
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Starter.exe
TRIN 5. Starter.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Starter.exe
Hvordan undgår din pc fra at blive inficeret med “Starter.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Starter.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Starter.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Starter.exe”.