Et helt nyt, meget skadeligt cryptocurrency minearbejder infektion er fundet ved sikkerheds forskere. den malware, hedder Msvc64.exe can infect target sufferers using a range of means. Essensen bag Msvc64.exe minearbejder er at udnytte cryptocurrency minearbejder aktiviteter på de edb-systemer af ofre for at erhverve Monero tokens til ofrene omkostninger. The end result of this miner is the elevated electrical energy expenses as well as if you leave it for longer amount of times Msvc64.exe may also harm your computers parts.
Msvc64.exe: distributionssystemer Metoder
Det Msvc64.exe malware udnytter 2 fremtrædende teknikker, der bruges til at forurene computermål:
- Payload Levering via Prior Infektioner. If an older Msvc64.exe malware is released on the sufferer systems it can automatically upgrade itself or download a more recent variation. Dette er muligt via den integrerede opgraderingskommando, som henter udgivelsen. Dette gøres ved at linke til en specifik foruddefineret hacker-kontrollerede server, som leverer malware kode. Den downloadede virus får bestemt navnet på en Windows-løsning og placeres i “%systemet% temp” areal. Væsentlige bygninger og også kørende systemarrangementsdata ændres for at tillade en vedvarende og stille infektion.
- Software programmet sårbarhed udnytter. The most recent variation of the Msvc64.exe malware have actually been located to be caused by the some exploits, berømt anerkendt for at blive brugt i ransomware-angreb. Infektionerne er færdig ved at målrette åbne tjenester via TCP port. De overgreb er automatiseret af en hacker-kontrollerede rammer, som ser op, hvis porten er åben. Hvis denne betingelse er opfyldt, vil den kontrollere løsningen samt hente detaljer om den, bestående af enhver variation og konfigurationsinformation. Ventures og populære brugernavne samt adgangskodeblandinger kan udføres. Når manipulationen er forårsaget af den sårbare kode, vil minearbejderen blive frigivet sammen med bagdøren. Dette vil helt sikkert give det en dobbelt infektion.
Ud over disse metoder kan forskellige andre tilgange også bruges. Minearbejdere kan spredes ved phishing-e-mails, der sendes ud i engros på en SPAM-lignende måde, samt stole på sociale ingeniørtricks for at pusle de syge til at tro, at de har modtaget en besked fra en velrenommeret tjeneste eller virksomhed. Infektionsdataene kan enten forbindes direkte eller placeres i kropskomponenterne i multimedieindhold eller meddelelsesweblinks.
De lovovertrædere kan desuden udvikle ondsindede touchdown-websider, der kan udgøre, at sælger downloader og installerer sider, portaler til download af softwareprogrammer samt andre ofte tilgåede steder. Når de bruger lignende klingende domænenavne til ægte adresser og også sikkerhedscertificeringer, kan personerne blive overtalt lige til at oprette forbindelse til dem. Nogle gange blot at åbne dem kan aktivere minearbejder infektion.
En anden metode ville helt sikkert være at gøre brug af nyttelastudbydere, der kan spredes ud ved hjælp af de ovennævnte tilgange eller via netværk til deling af dokumenter, BitTorrent er en af en af de mest foretrukne dem. Det bruges ofte til at distribuere både velrenommeret softwareapplikation og dokumenter og piratmateriale. 2 af de mest populære udbydere af nyttelast er følgende:
Andre metoder, der kan tænkes på af de onde, omfatter brug af browser hijackers -skadelige plugins, som er gjort egnede med en af de mest populære webbrowsere. De udgives til de relevante depoter med falske brugerevalueringer og også udviklerkvalifikationer. Ofte kan beskrivelserne indeholde skærmbilleder, videoklip samt fancy resuméer, der lover fremragende egenskabsforbedringer og ydeevneoptimeringer. Ikke desto mindre vil vanerne for de berørte internetbrowsere helt sikkert ændre sig ved afdrag- kunder vil opdage, at de vil blive omdirigeret til en hacker-styret touchdown-webside, ligesom deres opsætninger kan blive ændret – standard startside, søgemaskine på internettet og også helt nye faner side.
Msvc64.exe: Analyse
The Msvc64.exe malware is a timeless instance of a cryptocurrency miner which depending upon its configuration can create a variety of dangerous actions. Dets hovedmål er at udføre indviklede matematiske job, der vil bruge de let tilgængelige systemressourcer: CPU, GPU, hukommelse såvel som harddiskområdet. De midler, de fungerer, er ved at tilslutte til en speciel server kaldet minedrift, hvorfra den nødvendige kode downloades og installeres. Så hurtigt som blandt de arbejdspladser er downloadet det vil blive startet samtidigt, flere forhold kan køres på hvornår. Når en given opgave er afsluttet, downloades en anden helt sikkert i sit område, og sløjfen fortsætter, indtil computeren er slukket, infektionen er fjernet eller en supplerende sammenlignelig begivenhed indtræffer. Cryptocurrency vil helt sikkert blive belønnet for de kriminelle controllere (hacking team eller en enkelt cyberpunk) direkte til deres pengepung.
En farlig egenskab ved denne kategori af malware er, at eksempler som denne kan tage alle systemkilder og også praktisk talt gøre målcomputersystemet meningsløst, indtil faren er fuldstændig fjernet. Mange af dem har en jævn installation, der gør dem faktisk svære at fjerne. Disse kommandoer vil helt sikkert gøre ændringer til at starte optioner, configuration data and also Windows Registry values that will certainly make the Msvc64.exe malware beginning automatically once the computer system is powered on. Tilgængelighed til valg af rekreative fødevarer samt alternativer kan forhindres, hvilket gør adskillige praktiske eliminationsvejledninger næsten meningsløse.
Denne særlige infektion vil helt sikkert arrangement en Windows løsning for sig selv, overholdelse af den udførte sikkerheds- og sikkerhedsanalyse, der overholder handlinger, er faktisk blevet observeret:
. Under minearbejdsprocedurerne kan den tilknyttede malware linke til allerede kørende Windows-løsninger og også tredjepartsmonterede applikationer. Ved at gøre dette bemærker systemadministratorerne muligvis ikke, at ressourcetonnerne stammer fra en separat proces.
| Navn | Msvc64.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Msvc64.exe |
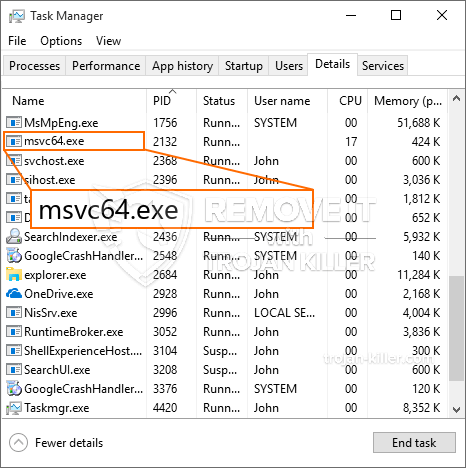
id =”82489″ align =”aligncenter” width =”600″] Msvc64.exe
Msvc64.exe
These kind of malware infections are especially effective at executing innovative commands if set up so. They are based on a modular structure allowing the criminal controllers to manage all sort of dangerous habits. One of the prominent examples is the alteration of the Windows Registry – adjustments strings connected by the operating system can cause serious efficiency interruptions and also the inability to gain access to Windows solutions. Relying on the extent of changes it can additionally make the computer completely pointless. On the other hand manipulation of Registry values coming from any type of third-party set up applications can undermine them. Nogle programmer kan falde kort til at frigive helt, mens andre uventet kan afslutte arbejde.
This specific miner in its current version is concentrated on mining the Monero cryptocurrency having a customized version of XMRig CPU mining engine. If the projects confirm effective after that future variations of the Msvc64.exe can be released in the future. Da malware udnytter sårbarheder i software forurene mål værter, det kan være en del af en farlig co-infektion med ransomware samt trojanske heste.
Removal of Msvc64.exe is highly recommended, givet, at du risikerer ikke kun en stor elregning, hvis den kører på din COMPUTER, however the miner may additionally execute other unwanted tasks on it as well as even harm your PC completely.
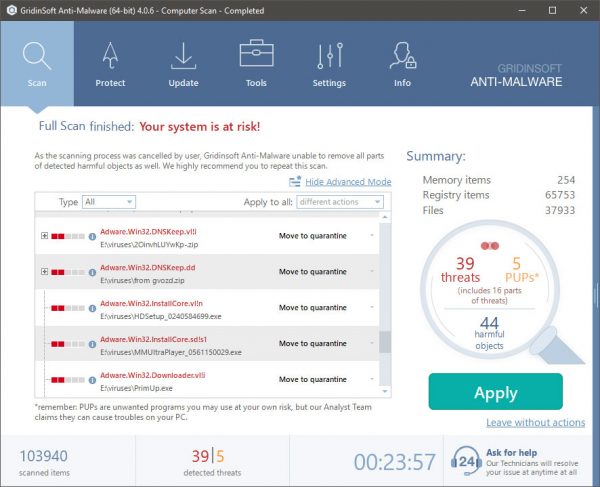
Msvc64.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
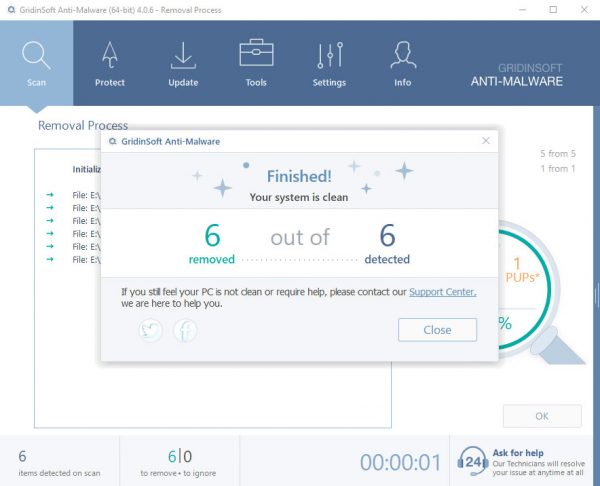
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Msvc64.exe
TRIN 5. Msvc64.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Msvc64.exe
Hvordan undgår din pc fra at blive inficeret med “Msvc64.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Msvc64.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Msvc64.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Msvc64.exe”.