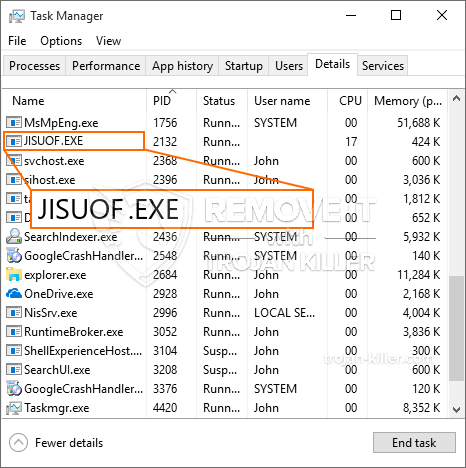
En ny, ekstremt skadelig kryptokurrency-minearbejdervirus er faktisk blevet opdaget af beskyttelsesforskere. den malware, hedder JISUOF.EXE kan inficere ofre mål at gøre brug af en række forskellige midler. The main point behind the JISUOF.EXE miner is to employ cryptocurrency miner tasks on the computer systems of targets in order to get Monero tokens at sufferers expenditure. The outcome of this miner is the elevated electrical energy costs and also if you leave it for longer amount of times JISUOF.EXE may even harm your computers elements.
JISUOF.EXE: distributionssystemer Metoder
Det JISUOF.EXE malware udnytter 2 fremtrædende tilgange, der bruges til at forurene computermål:
- Payload Levering via Prior Infektioner. If an older JISUOF.EXE malware is deployed on the victim systems it can immediately upgrade itself or download a newer variation. Dette er muligt ved hjælp af den integrerede opdatering kommando, som erhverver lanceringen. Dette gøres ved at binde sig til en bestemt foruddefineret hacker-kontrollerede webserver, der giver malware kode. The downloaded and install virus will certainly obtain the name of a Windows solution and be placed in the “%systemet% temp” placere. Vital homes as well as operating system arrangement data are altered in order to allow a persistent and quiet infection.
- Software sårbarhed udnytter. The most recent version of the JISUOF.EXE malware have actually been located to be triggered by the some exploits, bredt forstået for at blive udnyttet i de ransomware angreb. Infektionerne er færdig ved at målrette åbne løsninger via TCP port. Angrebene er automatiseret af en hacker-kontrolleret struktur, som opsøger hvis porten er åben. If this condition is fulfilled it will certainly check the service as well as recover details concerning it, including any version and configuration information. Exploits and prominent username and password mixes might be done. When the make use of is set off against the at risk code the miner will certainly be deployed in addition to the backdoor. Dette vil helt sikkert give det en dobbelt infektion.
Ud over disse teknikker andre tilgange kan gøres brug af for. Miners can be distributed by phishing emails that are sent out in bulk in a SPAM-like way and depend on social design tricks in order to puzzle the targets into thinking that they have actually gotten a message from a reputable solution or firm. The infection data can be either straight connected or placed in the body materials in multimedia content or text links.
The crooks can also create harmful landing web pages that can impersonate supplier download pages, software program download sites as well as other regularly accessed areas. When they use similar seeming domain to legitimate addresses and safety certifications the users may be coerced right into interacting with them. Nogle gange blot åbne dem kan aktivere minearbejder infektion.
An additional approach would certainly be to use haul carriers that can be spread out making use of the above-mentioned approaches or using documents sharing networks, BitTorrent er en af en af de mest foretrukne dem. It is frequently made use of to distribute both legitimate software as well as documents and also pirate material. 2 af en af de mest populære nyttelast udbydere er følgende:
Various other approaches that can be thought about by the offenders include the use of web browser hijackers -dangerous plugins which are made suitable with one of the most popular web browsers. They are uploaded to the relevant databases with phony customer evaluations and also programmer credentials. In many cases the summaries may consist of screenshots, video clips and sophisticated summaries promising fantastic attribute improvements and efficiency optimizations. Nonetheless upon installment the behavior of the affected web browsers will alter- customers will discover that they will certainly be redirected to a hacker-controlled landing page and their settings might be altered – standard webside, online søgemaskine og nye faner webside.

JISUOF.EXE: Analyse
The JISUOF.EXE malware is a traditional case of a cryptocurrency miner which depending upon its setup can create a wide range of unsafe activities. Its primary objective is to carry out complicated mathematical tasks that will certainly make use of the offered system sources: CPU, GPU, hukommelse og også harddisk område. The method they work is by connecting to an unique server called mining swimming pool from where the required code is downloaded. Så hurtigt som et af jobene er downloadet, vil det helt sikkert blive startet samtidigt, mange omstændigheder kan være væk, når. When a given job is finished an additional one will certainly be downloaded in its location and the loophole will continue up until the computer system is powered off, infektionen fået fjernet eller en mere sammenlignelige lejlighed sker. Cryptocurrency vil helt sikkert blive belønnet for de kriminelle controllere (hacking gruppe eller en ensom hacker) lige til deres budgetter.
A harmful attribute of this classification of malware is that samples such as this one can take all system sources and also practically make the target computer system unusable until the risk has been completely eliminated. The majority of them include a consistent setup which makes them actually challenging to eliminate. Disse kommandoer vil bestemt også ændre indstillingerne, setup data and also Windows Registry values that will certainly make the JISUOF.EXE malware start automatically when the computer system is powered on. Access to recovery food selections and also choices might be obstructed which provides many manual elimination overviews almost useless.
Denne vis infektion vil arrangementet en Windows-tjeneste for sig selv, complying with the performed safety analysis ther following actions have actually been observed:
Under minearbejder operationer den linkede malware kan linke til i øjeblikket kører Windows løsninger og tredjeparts installerede applikationer. By doing so the system administrators might not see that the resource lots originates from a separate process.
| Navn | JISUOF.EXE |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove JISUOF.EXE |
These sort of malware infections are particularly efficient at accomplishing advanced commands if set up so. De er baseret på en modulær ramme gør det muligt for kriminelle controllere at orkestrere alle former for farlig adfærd. Blandt de foretrukne eksempler er den ændring af Windows-registreringsdatabasen – modifications strings connected by the os can trigger severe efficiency disruptions and the lack of ability to access Windows solutions. Depending on the extent of changes it can additionally make the computer system entirely pointless. On the other hand adjustment of Registry values belonging to any third-party installed applications can sabotage them. Nogle applikationer stopper muligvis med at arbejde for at starte helt, mens andre pludselig kan stoppe med at arbejde.
This specific miner in its existing version is concentrated on extracting the Monero cryptocurrency consisting of a modified variation of XMRig CPU mining engine. If the projects show successful after that future versions of the JISUOF.EXE can be introduced in the future. Da malware udnytter software susceptabilities at inficere target værter, det kan være en del af en skadelig co-infektion med ransomware samt trojanske heste.
Removal of JISUOF.EXE is strongly advised, considering that you run the risk of not only a large electrical energy expense if it is working on your COMPUTER, but the miner may additionally execute various other unwanted tasks on it and even harm your COMPUTER permanently.
JISUOF.EXE removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove JISUOF.EXE
TRIN 5. JISUOF.EXE Removed!
Video guide: How to use GridinSoft Anti-Malware for remove JISUOF.EXE
Hvordan undgår din pc fra at blive inficeret med “JISUOF.EXE” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “JISUOF.EXE”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “JISUOF.EXE”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “JISUOF.EXE”.







