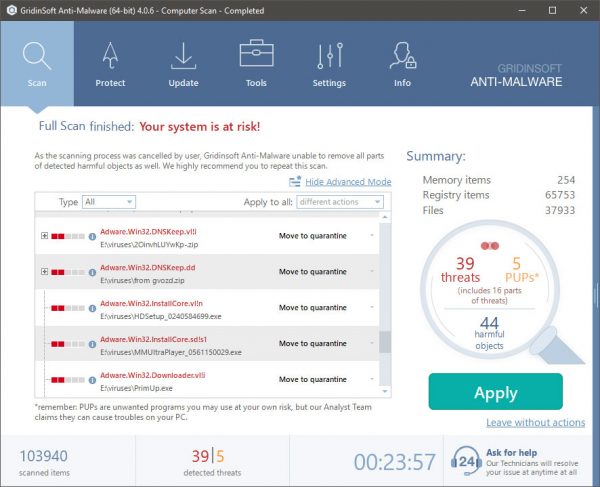
En ny, virkelig usikker kryptokurrency-minearbejdervirus er faktisk blevet fundet af sikkerhedsforskere. den malware, hedder Issch.exe kan forurene målofre ved hjælp af en række forskellige måder. Hovedpunktet bag Issch.exe-minearbejderen er at anvende cryptocurrency-minearbejder på målsystemers computersystemer for at erhverve Monero-tokens på ofrets bekostning. The end result of this miner is the raised electrical power bills and also if you leave it for longer periods of time Issch.exe may also harm your computers elements.
Issch.exe: distributionssystemer Metoder
Det Issch.exe malware uses two popular approaches which are utilized to infect computer system targets:
- Nyttelast Levering ved hjælp af kendte Infektioner. If an older Issch.exe malware is released on the target systems it can instantly update itself or download a newer version. This is feasible via the integrated update command which acquires the release. This is done by linking to a specific predefined hacker-controlled server which provides the malware code. The downloaded and install virus will acquire the name of a Windows service and also be placed in the “%systemet% temp” Beliggenhed. Essential buildings and operating system setup files are transformed in order to allow a persistent as well as silent infection.
- Software programmet sårbarhed udnytter. The newest variation of the Issch.exe malware have actually been located to be caused by the some exploits, populært forstået for at blive brugt i ransomware-angreb. Infektionerne er færdig ved at målrette åbne løsninger ved hjælp af TCP port. Strejkerne er automatiseret af en hacker-kontrolleret struktur, som opsøger hvis porten er åben. If this condition is satisfied it will certainly check the solution and obtain details regarding it, including any kind of version as well as configuration information. Exploits as well as preferred username and also password mixes might be done. When the exploit is activated against the vulnerable code the miner will certainly be deployed in addition to the backdoor. Dette vil helt sikkert give det en dobbelt infektion.
Besides these techniques other techniques can be used also. Miners can be dispersed by phishing e-mails that are sent wholesale in a SPAM-like way as well as depend on social design tricks in order to puzzle the victims into believing that they have actually obtained a message from a genuine service or company. The virus data can be either directly attached or inserted in the body contents in multimedia material or message web links.
The offenders can additionally develop harmful touchdown pages that can pose vendor download pages, software application download sites and also other frequently accessed areas. When they use comparable seeming domain to genuine addresses and also safety and security certifications the users may be pushed into interacting with them. I nogle tilfælde kan blot åbning af dem forårsage minearbejdsinfektion.
Another strategy would certainly be to make use of payload carriers that can be spread using those methods or via file sharing networks, BitTorrent er en af de mest populære dem. It is often used to disperse both legitimate software and data and also pirate material. 2 af en af de mest foretrukne leverandører af transporttjenester er følgende:
Other methods that can be taken into consideration by the crooks include using internet browser hijackers -harmful plugins which are made compatible with one of the most popular web internet browsers. They are submitted to the relevant repositories with phony customer testimonials and programmer credentials. Oftentimes oversigter kan omfatte skærmbilleder, video clips as well as elaborate descriptions promising fantastic function improvements and also performance optimizations. However upon setup the behavior of the impacted browsers will certainly alter- customers will certainly discover that they will be redirected to a hacker-controlled touchdown page and also their settings may be altered – standard startside, internetsøgemaskine samt splinterny faneblad side.
Issch.exe: Analyse
The Issch.exe malware is a timeless situation of a cryptocurrency miner which relying on its setup can trigger a variety of unsafe activities. Its major objective is to perform complex mathematical tasks that will make the most of the readily available system sources: CPU, GPU, hukommelse samt harddisk plads. The way they operate is by linking to an unique web server called mining pool where the called for code is downloaded. Så snart blandt jobs er downloadet, vil det helt sikkert blive påbegyndt på samme tid, flere omstændigheder kan køre på, så snart. When a provided task is completed an additional one will certainly be downloaded and install in its place and the loop will certainly continue till the computer system is powered off, infektionen fået fjernet eller en mere ens lejlighed sker. Cryptocurrency vil blive tildelt de kriminelle controllere (hacking gruppe eller en enkelt hacker) direkte til deres tegnebøger.
A dangerous quality of this category of malware is that examples such as this one can take all system resources and almost make the victim computer system unusable till the threat has actually been entirely gotten rid of. The majority of them include a relentless setup that makes them really difficult to eliminate. Disse kommandoer vil foretage ændringer også alternativer, arrangement documents and also Windows Registry values that will certainly make the Issch.exe malware start automatically when the computer system is powered on. Access to recuperation food selections as well as choices might be blocked which makes numerous hands-on removal guides virtually useless.
Denne specifikke infektion opsætter en Windows-løsning til sig selv, complying with the carried out safety and security analysis ther complying with actions have been observed:
. During the miner operations the linked malware can hook up to currently running Windows solutions and also third-party installed applications. By doing so the system administrators may not see that the source tons comes from a different procedure.
| Navn | Issch.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Issch.exe |
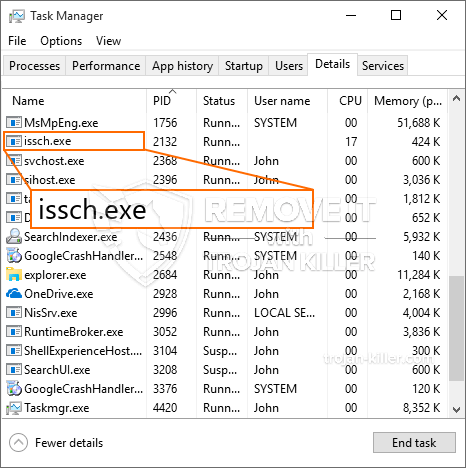
id =”83478″ align =”aligncenter” width =”600″]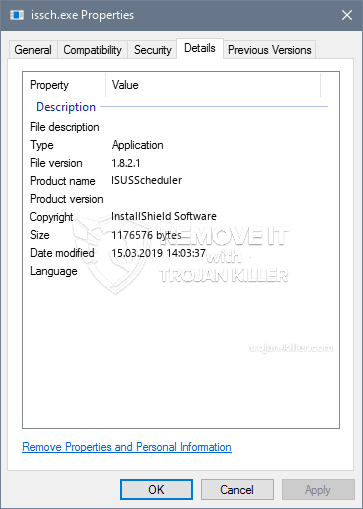 Issch.exe
Issch.exe
These type of malware infections are particularly effective at executing sophisticated commands if set up so. De er baseret på en modulær ramme tillader de kriminelle controllere til at koordinere alle former for skadelige handlinger. One of the prominent examples is the alteration of the Windows Registry – alterations strings connected by the os can create serious efficiency disturbances as well as the lack of ability to access Windows solutions. Depending on the extent of modifications it can likewise make the computer system totally unusable. På den anden side kan manipulation af registreringsværdier, der kommer fra enhver form for tredjeparts installerede applikationer, underminere dem. Some applications may fall short to launch completely while others can unexpectedly quit working.
This specific miner in its existing version is focused on mining the Monero cryptocurrency including a customized variation of XMRig CPU mining engine. If the campaigns show successful then future versions of the Issch.exe can be introduced in the future. Da malware gør brug af software program sårbarheder til at forurene mål værter, det kan være en del af en farlig co-infektion med ransomware og trojanske heste.
Elimination of Issch.exe is highly recommended, considering that you risk not only a large power bill if it is operating on your PC, but the miner may additionally carry out other unwanted tasks on it as well as also damage your COMPUTER completely.
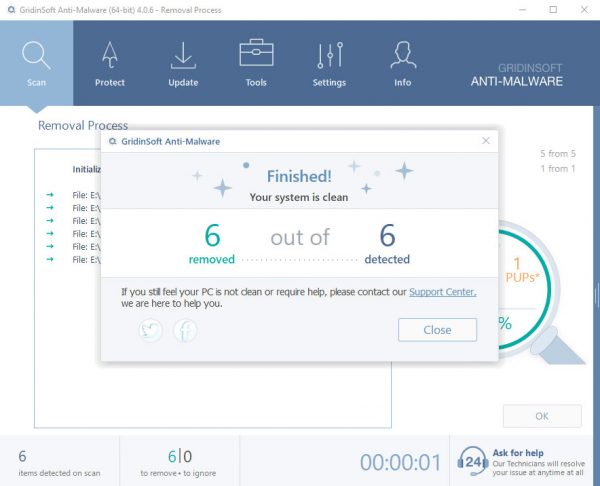
Issch.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
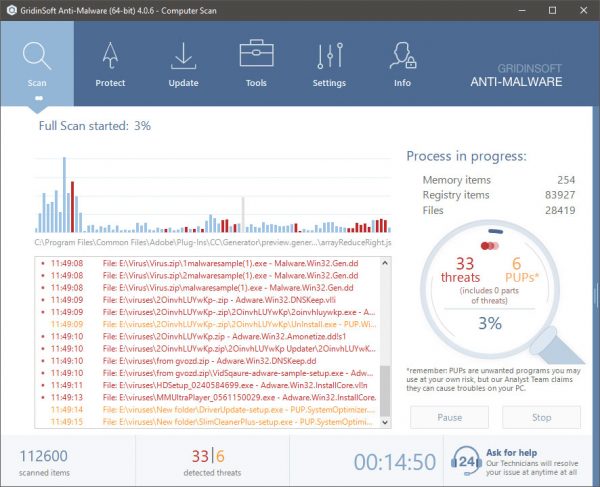
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Issch.exe
TRIN 5. Issch.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Issch.exe
Hvordan undgår din pc fra at blive inficeret med “Issch.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Issch.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Issch.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Issch.exe”.