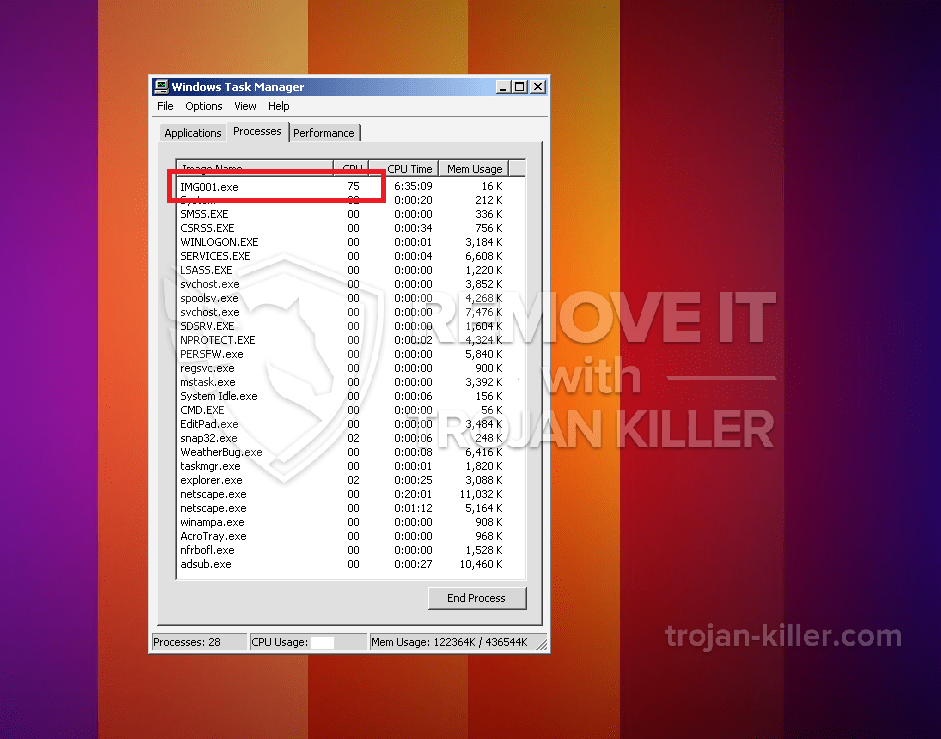
Et helt nyt, meget skadelig kryptokurrency-minearbejderinfektion er blevet opdaget af sikkerhedsforskere. den malware, hedder IMG001.EXE kan forurene målofre ved hjælp af en række forskellige måder. Essensen bag IMG001.EXE minearbejderen er at bruge cryptocurrency minearbejderopgaver på computersystemer for mål for at erhverve Monero-symboler til måludgifter. The outcome of this miner is the raised electrical energy bills and also if you leave it for longer amount of times IMG001.EXE may even damage your computers elements.
IMG001.EXE: distributionssystemer Metoder
Det IMG001.EXE malware udnytter 2 fremtrædende tilgange, der bruges til at forurene computermål:
- Payload Levering hjælp Prior Infektioner. If an older IMG001.EXE malware is released on the target systems it can immediately upgrade itself or download and install a more recent version. This is feasible through the integrated upgrade command which gets the release. This is done by attaching to a certain predefined hacker-controlled server which provides the malware code. The downloaded and install infection will certainly obtain the name of a Windows service as well as be positioned in the “%systemet% temp” Beliggenhed. Crucial properties and operating system arrangement documents are transformed in order to allow a consistent as well as quiet infection.
- Software Application sårbarhed udnytter. The most recent version of the IMG001.EXE malware have been located to be caused by the some ventures, commonly recognized for being made use of in the ransomware strikes. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Overgrebene er automatiseret af en hacker-kontrolleret struktur, som ser op hvis porten er åben. If this problem is satisfied it will certainly check the solution as well as retrieve info concerning it, consisting of any type of variation as well as configuration data. Udnytter og også foretrukne brugernavn og adgangskode blandinger kan gøres. When the manipulate is triggered versus the at risk code the miner will certainly be released together with the backdoor. Dette vil danne en dobbelt infektion.
In addition to these approaches other approaches can be utilized as well. Miners can be dispersed by phishing emails that are sent out wholesale in a SPAM-like way as well as depend upon social design methods in order to puzzle the sufferers right into thinking that they have gotten a message from a legit service or business. The virus files can be either directly affixed or placed in the body components in multimedia content or text web links.
The wrongdoers can likewise develop destructive landing pages that can pose vendor download and install pages, software program download portals and other regularly accessed areas. When they make use of similar seeming domain to legit addresses and also protection certifications the customers might be pushed right into connecting with them. I mange tilfælde blot åbne dem kan aktivere minearbejder infektion.
Another approach would be to utilize payload carriers that can be spread out making use of the above-mentioned techniques or using data sharing networks, BitTorrent er blot en af en af de mest fremtrædende dem. It is regularly made use of to disperse both genuine software application and also files as well as pirate web content. 2 af de mest populære distancer tjenesteydere er følgende:
Various other approaches that can be considered by the criminals consist of using browser hijackers -dangerous plugins which are made suitable with the most popular internet browsers. They are submitted to the appropriate databases with phony customer reviews and designer credentials. I mange tilfælde resuméerne kan omfatte skærmbilleder, videos as well as intricate summaries appealing excellent function improvements and also efficiency optimizations. However upon installation the behavior of the affected browsers will transform- individuals will certainly find that they will be rerouted to a hacker-controlled landing web page and also their setups might be altered – standard startside, søgemaskine samt helt nye faner webside.
IMG001.EXE: Analyse
The IMG001.EXE malware is a traditional situation of a cryptocurrency miner which depending upon its arrangement can create a variety of unsafe activities. Its major objective is to execute complex mathematical jobs that will certainly make the most of the available system resources: CPU, GPU, hukommelse samt harddisk område. The means they operate is by linking to an unique web server called mining pool from where the needed code is downloaded. As soon as among the jobs is downloaded it will certainly be started at the same time, several instances can be performed at once. When an offered task is completed another one will be downloaded and install in its location and the loop will proceed till the computer is powered off, infektionen er fjernet eller ét forekommer mere sammenlignelig begivenhed. Cryptocurrency vil blive kompenseret for de kriminelle controllere (hacking team eller en ensom hacker) direkte til deres punge.
A hazardous characteristic of this group of malware is that examples such as this one can take all system sources and also almost make the target computer system unusable till the risk has been entirely eliminated. A lot of them include a relentless installment that makes them really difficult to eliminate. Disse kommandoer vil foretage justeringer for at starte alternativer, setup data and Windows Registry values that will make the IMG001.EXE malware begin automatically as soon as the computer is powered on. Access to recuperation menus and also alternatives may be obstructed which renders numerous hands-on elimination guides practically worthless.
Denne særlige infektion vil arrangement en Windows-tjeneste for sig selv, complying with the conducted security evaluation ther following actions have been observed:
. During the miner operations the linked malware can attach to already running Windows solutions and also third-party mounted applications. By doing so the system managers may not see that the resource lots comes from a different procedure.
| Navn | IMG001.EXE |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove IMG001.EXE |
id =”81608″ align =”aligncenter” width =”600″] IMG001.EXE
IMG001.EXE
These kind of malware infections are particularly reliable at performing advanced commands if configured so. They are based on a modular framework allowing the criminal controllers to manage all kinds of dangerous actions. Et af de populære eksempler er ændringen af Windows-registreringsdatabasen – modifications strings related by the os can create severe efficiency interruptions and also the lack of ability to accessibility Windows solutions. Depending upon the extent of adjustments it can additionally make the computer system entirely unusable. På den anden side kan justering af registreringsværdier, der kommer fra tredjepartsmonterede applikationer, underminere dem. Nogle applikationer kan ikke starte helt, mens andre pludselig kan holde op med at fungere.
This specific miner in its existing variation is focused on extracting the Monero cryptocurrency including a modified version of XMRig CPU mining engine. If the campaigns prove successful after that future versions of the IMG001.EXE can be launched in the future. Da malware udnytter software program susceptabilities at forurene mål værter, det kan være en del af et farligt co-infektion med ransomware og trojanske heste.
Elimination of IMG001.EXE is highly recommended, given that you take the chance of not just a large electricity expense if it is working on your COMPUTER, but the miner might also execute other unwanted activities on it and even damage your PC permanently.
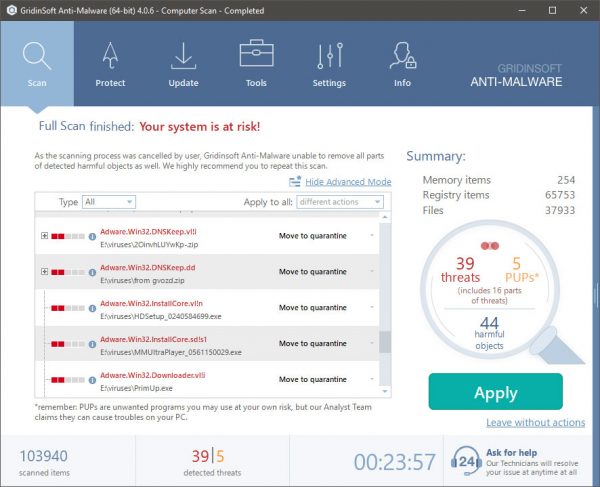
IMG001.EXE removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
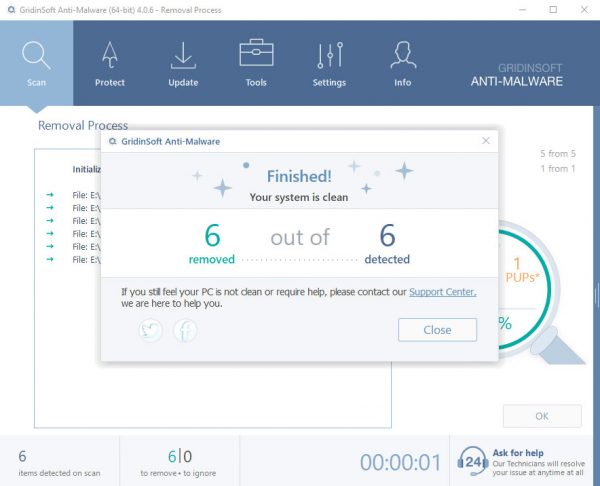
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove IMG001.EXE
TRIN 5. IMG001.EXE Removed!
Video guide: How to use GridinSoft Anti-Malware for remove IMG001.EXE
Hvordan undgår din pc fra at blive inficeret med “IMG001.EXE” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “IMG001.EXE”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “IMG001.EXE”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “IMG001.EXE”.