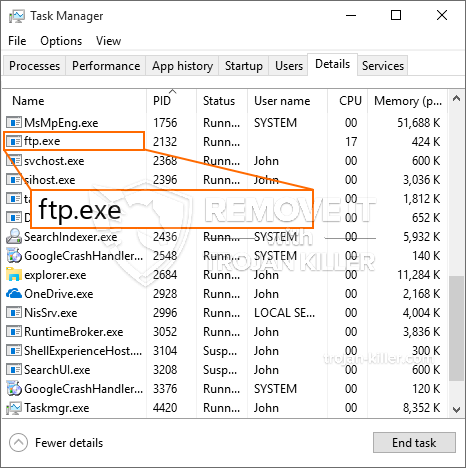
En ny, Virkelig usikker kryptovaluta-minearbejdervirus er faktisk blevet fundet af sikkerhedsforskere. den malware, hedder FTP.exe can infect target victims using a range of ways. The main point behind the FTP.exe miner is to utilize cryptocurrency miner activities on the computers of victims in order to get Monero tokens at sufferers cost. The result of this miner is the raised power bills and if you leave it for longer amount of times FTP.exe might even damage your computer systems parts.
FTP.exe: distributionssystemer Metoder
Det FTP.exe malware uses two popular techniques which are made use of to contaminate computer system targets:
- Payload Levering via Prior Infektioner. If an older FTP.exe malware is deployed on the victim systems it can instantly upgrade itself or download and install a newer variation. This is feasible using the built-in upgrade command which gets the release. This is done by linking to a specific predefined hacker-controlled server which offers the malware code. The downloaded infection will acquire the name of a Windows service and be put in the “%systemet% temp” Beliggenhed. Vital residential properties and running system arrangement data are changed in order to allow a relentless as well as quiet infection.
- Software sårbarhed udnytter. The newest variation of the FTP.exe malware have been discovered to be triggered by the some ventures, berømt anerkendt for at blive anvendt i de ransomware angreb. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Strejkerne er automatiseret af en hacker-kontrolleret ramme som opsøger hvis porten er åben. Hvis denne betingelse er opfyldt, vil kontrollere den service og gendanne oplysninger om det, including any type of variation and configuration information. Exploits and prominent username and password mixes might be done. When the exploit is caused versus the susceptible code the miner will certainly be deployed along with the backdoor. Dette vil helt sikkert give en dobbelt infektion.
Udover disse metoder kan andre teknikker også anvendes. Miners can be dispersed by phishing e-mails that are sent in bulk in a SPAM-like manner as well as depend on social engineering tricks in order to confuse the sufferers right into thinking that they have gotten a message from a legit service or business. The infection files can be either straight attached or put in the body contents in multimedia content or message web links.
The crooks can also develop malicious touchdown pages that can impersonate supplier download and install web pages, software download sites and also other frequently accessed locations. When they make use of comparable appearing domain names to legitimate addresses as well as safety and security certificates the customers might be pushed into engaging with them. I nogle tilfælde blot åbne dem kan udløse minearbejder infektion.
Another technique would be to use haul providers that can be spread utilizing the above-mentioned methods or through data sharing networks, BitTorrent er blandt de mest foretrukne. It is often utilized to disperse both reputable software application and data and pirate content. 2 af de mest populære trækudbydere er følgende:
Various other methods that can be thought about by the crooks consist of making use of browser hijackers -harmful plugins which are made suitable with the most popular internet browsers. They are published to the appropriate databases with fake user testimonials and developer qualifications. I de fleste tilfælde beskrivelserne kan omfatte skærmbilleder, video clips and elaborate summaries appealing excellent attribute improvements and efficiency optimizations. Nonetheless upon installation the behavior of the impacted internet browsers will alter- users will certainly locate that they will certainly be redirected to a hacker-controlled touchdown web page and their setups might be modified – standard startside, online søgemaskine og nye faner webside.

FTP.exe: Analyse
The FTP.exe malware is a classic situation of a cryptocurrency miner which depending on its configuration can create a wide array of dangerous actions. Its main objective is to perform complex mathematical jobs that will certainly make use of the readily available system resources: CPU, GPU, hukommelse og harddisk plads. The way they function is by linking to a special web server called mining pool from where the called for code is downloaded and install. Så snart en af opgaverne er downloadet det vil blive startet på en gang, talrige omstændigheder kan udføres ved så snart. When a given task is finished another one will certainly be downloaded and install in its place and also the loop will proceed until the computer is powered off, infektionen er fjernet, eller der finder en anden sammenlignelig lejlighed sted. Cryptocurrency vil helt sikkert blive tildelt de kriminelle controllere (hacking team eller en enkelt cyberpunk) direkte til deres tegnebøger.
A dangerous characteristic of this group of malware is that samples such as this one can take all system sources and practically make the target computer system pointless up until the danger has actually been totally gotten rid of. A lot of them include a relentless installment which makes them truly challenging to remove. Disse kommandoer vil foretage justeringer også valg, arrangement documents as well as Windows Registry values that will certainly make the FTP.exe malware start immediately once the computer system is powered on. Access to recovery food selections and alternatives might be obstructed which makes lots of manual removal guides almost useless.
Denne vis infektion vil konfigurationshåndtering en Windows-tjeneste for sig selv, following the performed security analysis ther following activities have actually been observed:
During the miner procedures the linked malware can hook up to already running Windows services and third-party installed applications. Ved at gøre så systemet ledere kan ikke se, at kilden belastningen kommer fra en anden procedure.
| Navn | FTP.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove FTP.exe |
These kind of malware infections are especially reliable at executing advanced commands if configured so. De er baseret på en modulær ramme, der tillader de kriminelle kontrollører at koordinere alle former for farlige handlinger. Et af de fremtrædende eksempler er justeringen af Windows-registreringsdatabasen – modifications strings connected by the operating system can create significant performance disruptions and also the failure to accessibility Windows services. Relying on the scope of adjustments it can also make the computer system entirely pointless. On the various other hand adjustment of Registry worths belonging to any type of third-party mounted applications can sabotage them. Some applications may stop working to introduce entirely while others can all of a sudden stop working.
This certain miner in its existing version is concentrated on extracting the Monero cryptocurrency consisting of a changed version of XMRig CPU mining engine. If the projects show effective after that future variations of the FTP.exe can be released in the future. Da de malware gør brug af software applikationer susceptabilities forurene mål værter, det kan være en del af et farligt co-infektion med ransomware og også trojanske heste.
Elimination of FTP.exe is strongly suggested, considering that you risk not only a big power costs if it is running on your COMPUTER, yet the miner might also carry out other unwanted tasks on it and also even harm your COMPUTER permanently.
FTP.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove FTP.exe
TRIN 5. FTP.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove FTP.exe
Hvordan undgår din pc fra at blive inficeret med “FTP.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “FTP.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “FTP.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “FTP.exe”.







