En ny, Virkelig skadelig kryptokurrency-minearbejdervirus er faktisk blevet opdaget af forskere inden for sikkerhed og sikkerhed. den malware, hedder Dether.exe kan forurene target syge ved hjælp af forskellige måder. The main idea behind the Dether.exe miner is to use cryptocurrency miner activities on the computer systems of victims in order to acquire Monero tokens at sufferers expense. The end result of this miner is the raised power expenses as well as if you leave it for longer time periods Dether.exe might even harm your computer systems parts.
Dether.exe: distributionssystemer Metoder
Det Dether.exe malware anvendelser 2 popular methods which are made use of to contaminate computer system targets:
- Payload Levering gennem Prior Infektioner. If an older Dether.exe malware is deployed on the sufferer systems it can instantly update itself or download and install a newer version. This is feasible by means of the built-in upgrade command which acquires the launch. Dette gøres ved at forbinde til en bestemt foruddefineret hacker-kontrollerede webserver, der giver malware kode. The downloaded virus will get the name of a Windows solution as well as be placed in the “%systemet% temp” placere. Essential homes and running system arrangement documents are altered in order to allow a relentless and quiet infection.
- Software sårbarhed udnytter. The latest variation of the Dether.exe malware have actually been discovered to be caused by the some exploits, kendt for at blive brugt i ransomware-angrebene. Infektionerne er færdig ved at målrette åbne tjenester ved hjælp af TCP port. Overgrebene er automatiseret af en hacker-kontrolleret ramme som søger efter hvis porten er åben. If this condition is fulfilled it will certainly check the service and also obtain details concerning it, herunder enhver form for versionen samt opsætningsdata. Udnytter samt foretrukne brugernavn og også adgangskoder kan gøres. When the exploit is triggered against the susceptible code the miner will certainly be released along with the backdoor. Dette vil give den en dobbelt infektion.
Aside from these approaches other techniques can be used as well. Miners can be dispersed by phishing e-mails that are sent in bulk in a SPAM-like way as well as depend upon social engineering techniques in order to perplex the targets into thinking that they have actually gotten a message from a reputable solution or firm. The virus files can be either straight connected or inserted in the body components in multimedia content or message links.
The crooks can additionally produce destructive touchdown pages that can pose supplier download and install pages, software ansøgning download sites og også andre ofte adgang steder. When they use similar seeming domain names to legitimate addresses as well as safety and security certificates the users might be pushed right into interacting with them. I nogle tilfælde bare åbne dem kan aktivere minearbejder infektion.
Another method would be to make use of haul carriers that can be spread out making use of those techniques or by means of data sharing networks, BitTorrent er blot en af de mest fremtrædende dem. It is regularly utilized to distribute both reputable software application and also data and also pirate web content. To af de mest fremtrædende nyttelast tjenesteydere er følgende:
Various other methods that can be considered by the criminals include using browser hijackers -hazardous plugins which are made suitable with the most popular internet browsers. They are posted to the relevant repositories with phony individual testimonials and also developer credentials. In many cases the summaries may consist of screenshots, video clips and also intricate summaries encouraging terrific feature improvements as well as performance optimizations. Ikke desto mindre vil de berørte webbrowsers handlinger ændre sig efter aflevering- users will locate that they will certainly be redirected to a hacker-controlled touchdown web page and also their setups might be altered – standard webside, online søgemaskine samt nye faner webside.
Dether.exe: Analyse
The Dether.exe malware is a timeless situation of a cryptocurrency miner which relying on its setup can trigger a wide array of harmful actions. Dets primære mål er at udføre indviklede matematiske opgaver, der helt sikkert vil få mest muligt ud af de tilbudte systemressourcer: CPU, GPU, hukommelse og også harddiskplads. The way they work is by linking to a special server called mining pool where the required code is downloaded. Så snart en af opgaverne downloades, startes den samtidigt, numerous circumstances can be gone for once. When a provided job is completed another one will certainly be downloaded in its area and the loop will certainly proceed up until the computer system is powered off, the infection is removed or an additional similar event happens. Cryptocurrency vil blive tildelt de kriminelle controllere (hacking team eller en ensom cyberpunk) direkte til deres pengepung.
A harmful quality of this classification of malware is that samples like this one can take all system sources and also almost make the target computer unusable till the hazard has actually been totally eliminated. Most of them include a consistent installation that makes them truly hard to remove. Disse kommandoer vil helt sikkert gøre ændringer også valg, configuration files and Windows Registry values that will certainly make the Dether.exe malware begin instantly as soon as the computer system is powered on. Access to recuperation food selections as well as alternatives may be blocked which makes several hand-operated removal guides virtually ineffective.
Denne specifikke infektion installerer en Windows-tjeneste for sig selv, efterlevelse af den udførte sikkerhedsevaluering og efterlevelse af aktiviteter er blevet observeret:
. During the miner procedures the connected malware can link to already running Windows services and third-party set up applications. By doing so the system managers may not discover that the resource load comes from a separate procedure.
| Navn | Dether.exe |
|---|---|
| Kategori | Trojan |
| Sub-kategori | Cryptocurrency Miner |
| farer | Høj CPU-forbrug, reduktion Internet hastighed, PC nedbrud og fryser og etc. |
| Hovedformål | For at tjene penge til cyberkriminelle |
| Fordeling | Torrents, Gratis spil, Cracked apps, E-mail, tvivlsomme hjemmesider, udnytter |
| Fjernelse | Installere GridinSoft Anti-Malware to detect and remove Dether.exe |
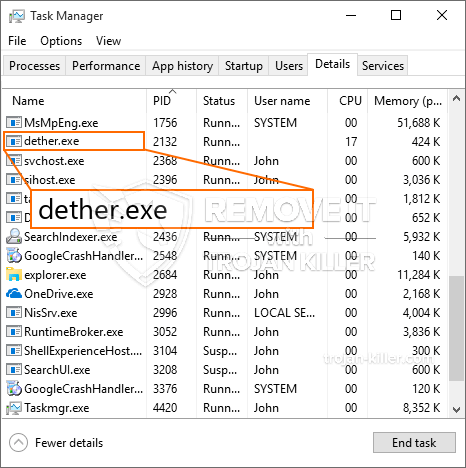
id =”81525″ align =”aligncenter” width =”600″]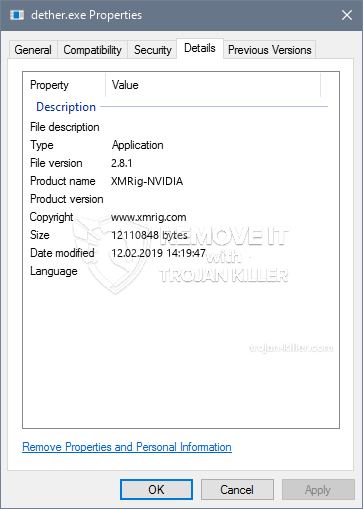 Dether.exe
Dether.exe
These type of malware infections are specifically efficient at executing innovative commands if configured so. They are based upon a modular framework permitting the criminal controllers to orchestrate all kinds of unsafe habits. Et af de populære forekomster er justeringen af registreringsdatabasen i Windows – modifications strings related by the os can create major efficiency disturbances and also the lack of ability to accessibility Windows solutions. Depending upon the scope of changes it can also make the computer system entirely unusable. On the various other hand adjustment of Registry worths belonging to any kind of third-party installed applications can sabotage them. Some applications might fall short to introduce completely while others can suddenly stop working.
This particular miner in its present variation is concentrated on extracting the Monero cryptocurrency consisting of a changed variation of XMRig CPU mining engine. If the campaigns verify successful then future variations of the Dether.exe can be introduced in the future. Da malware bruger softwareapplikationssårbarheder til at inficere målværter, det kan være en del af en usikker co-infektion med ransomware og trojanske heste.
Removal of Dether.exe is highly suggested, because you run the risk of not only a large electricity expense if it is working on your PC, but the miner might also execute other undesirable tasks on it as well as even harm your COMPUTER permanently.
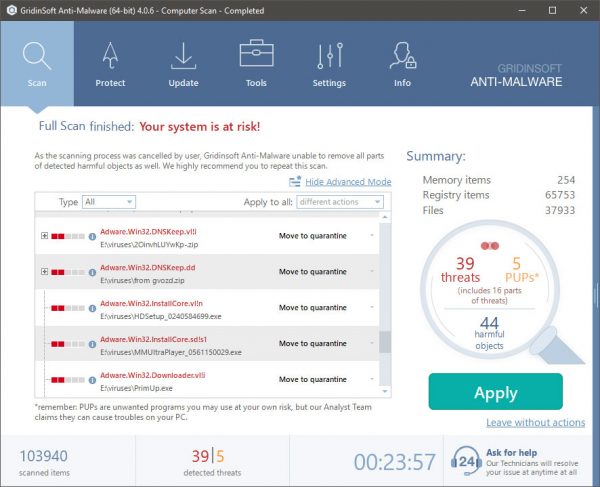
Dether.exe removal process
TRIN 1. Først og fremmest, skal du downloade og installere GridinSoft Anti-Malware.
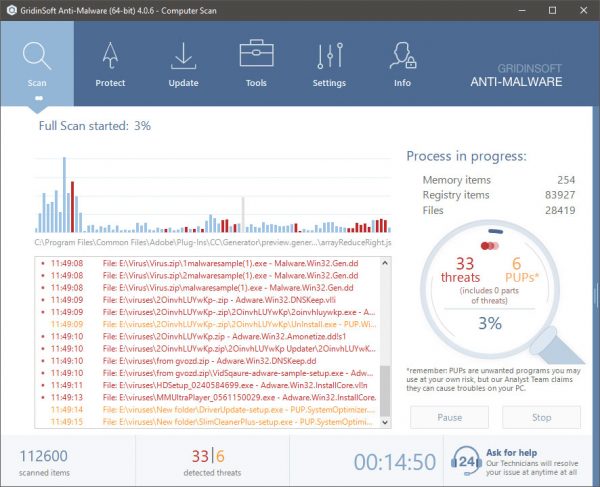
TRIN 2. Så skal du vælge “Hurtig scanning” eller “Fuld scanning”.
TRIN 3. Kør til at scanne din computer
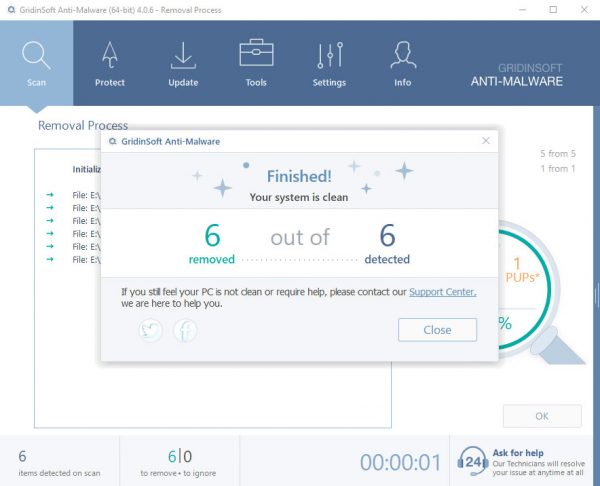
TRIN 4. Når scanningen er fuldført, skal du klikke på “ansøge” button to remove Dether.exe
TRIN 5. Dether.exe Removed!
Video guide: How to use GridinSoft Anti-Malware for remove Dether.exe
Hvordan undgår din pc fra at blive inficeret med “Dether.exe” i fremtiden.
En kraftfuld antivirus-løsning, der kan detektere og blokere fileless malware er, hvad du har brug for! Traditionelle løsninger opdage malware baseret på virusdefinitioner, og dermed de kan ofte ikke registrere “Dether.exe”. GridinSoft Anti-Malware beskytter mod alle typer af malware, herunder fileless malware såsom “Dether.exe”. GridinSoft Anti-Malware giver cloud-baseret adfærd analysator at blokere alle ukendte filer, herunder zero-day malware. Sådan teknologi kan opdage og helt fjerne “Dether.exe”.