
Eksperter fra Fidelis cybersikkerhed studerede sårbarheder, der var mest populære blandt hackere i første kvartal af 2019.
Though value of vulnerabilities dramatically falls immediately after publication of patches for them, ubudne gæster ikke nægte mod udnyttelse af bugs så hurtigt. faktisk, hackere fortsætte med at bruge sårbarheder, indtil de kan nå alle værdige mål med deres hjælp.“In addition to staying current with new threat campaigns and techniques, our intelligence team feels it’s also imperative to ensure we don’t lose focus on previously identified and existing threats”, — consider in Fidelis Cybersecurity.
According to Fidelis Cybersecurity report, many of the most actual threats in the first quarterly of 2019 are old, well-known bugs, patches for them arrived few years ago.
Så, nearly one third of all detected in the first quarterly problems (udnytter, sårbarheder, Malware) date 2017 og tidligere.
For eksempel, the most active malwares were H-W0rm (Houdini) og njRAT, two Trojans of remote access (ROTTE) that exist at least since 2012. i øvrigt, experts suggest that developers of these “tools” work together.
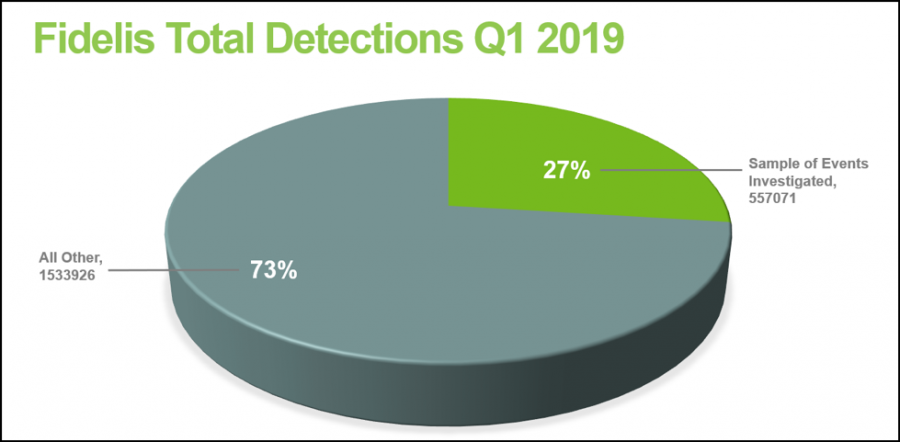
Derudover, analysts accounted that om 27% of compromise attempts (Mere end 550 000 investigated incidents) were linked to vulnerabilities, detected in 2017 og tidligere.
“Threat actors and campaigns not only are able to adjust to current trends and update capabilities, but also highlights the continued focus on pre-existing vulnerabilities and recurring tactics to carry out their campaigns and activity”, — emphasize in Fidelis Cybersecurity.
Som resultat, top-5 most popular old issues look like this:
- CVE-2017-8570— RCE bug Composite Moniker, exploit is publicly available;
- CVE-2017-0143– problem that involves SMBv1, exploit is published by ShadowBrokers (Eternal Synergy) Gruppe;
- CVE-2018-11776– RCE-vulnerability in Apache Struts, exploit is publicly available;
- CVE-2017-11882— RCE-vulnerability in Microsoft Office, exploit is publicly available;
- CVE-2009-3129– RCE-vulnerability in Microsoft Excel/Word, was used in Red October operation, exploit is publicly available.
Kilde: www.fidelissecurity.com
